Part 1 (How to Configure Microsoft Certificate Services for AnyConnect)
KB ID 0001030
Problem
I’ve done a lot of AnyConnect deployments, and I’ve even done them with certificates in the past. I’ve seen plenty of articles and blogs that say ‘It would be better to use a PKI deployment like Microsoft Certificate Services’, but there’s very little info out there on how to set it up.
I have a client that was going to deploy Microsoft Direct Access, but due to unforeseen circumstances has changed their requirements and wants to use AnyConnect instead, (with the following requirements).
- The connection should be ‘always on’ for their remote clients.
- It should use certificate based authentication that would use their existing PKI deployment.
- They should be able to control the remote clients from their corporate location (if required).
- They should be able to roll out the software using Microsoft SCCM.
So I disappeared with an ESXi server, a spare firewall, and a large mug of coffee.
Solution
I am going to send out both user and computer certificates, and I’m going to get the machines to ‘Autoenroll’ for the certificates with group policy. (You could just use ‘User’ certificates, but that would be too easy).
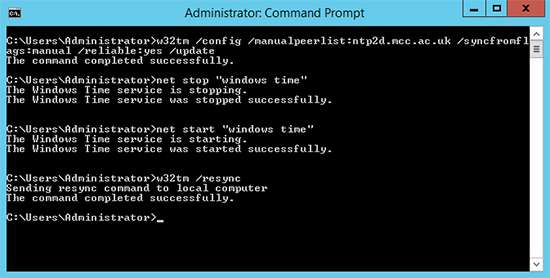
1. Remember certificates are time specific, make sure your Windows domain is keeping good time, I’ve written about this before, but to cut a long story short carry out the following on your PDC emulator at an elevated command prompt.
w32tm /config /manualpeerlist:ntp2d.mcc.ac.uk /syncfromflags:manual /reliable:yes /update net stop "windows time" net start "windows time" w32tm /resync
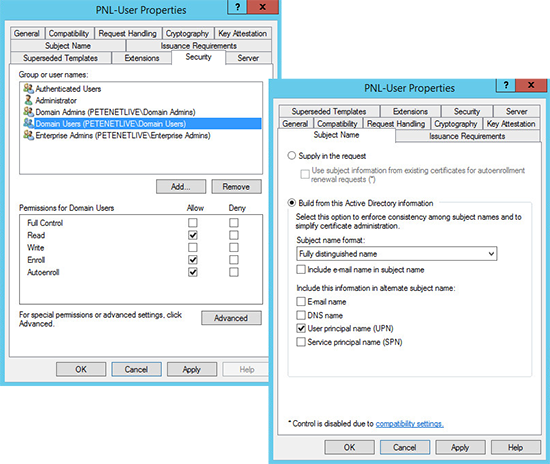
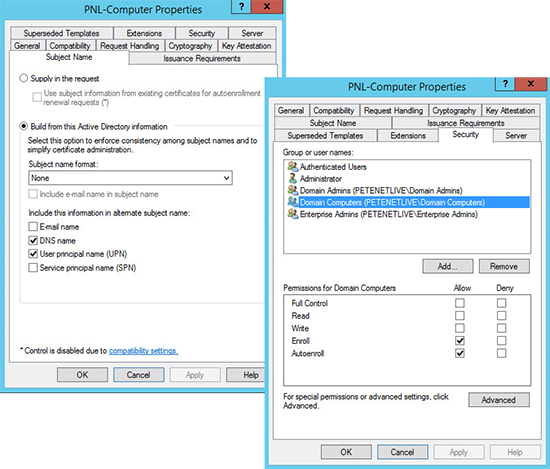
2. I’m assuming you have certificate services setup and have certificates setup for computers and users, if not see Installing Microsoft Certificate Services. Ensure you have templates published and they are configured correctly, like so;
User Certificate Template
Computer Certificate Template
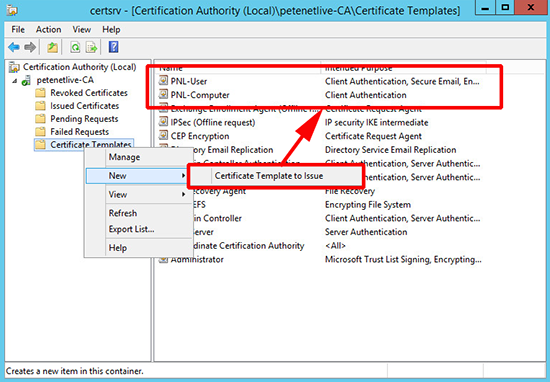
3. Publish the Certificates.
4. Set up a Group Policy for Certificate Auto-enrolment.
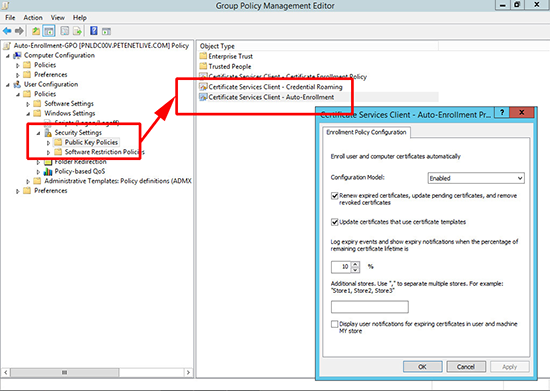
5. For User certificate auto-enrollment go to:
User Configuration > Windows Settings > Security Settings > Public Key Policies > Certificate Services Client - Auto-Enrolment
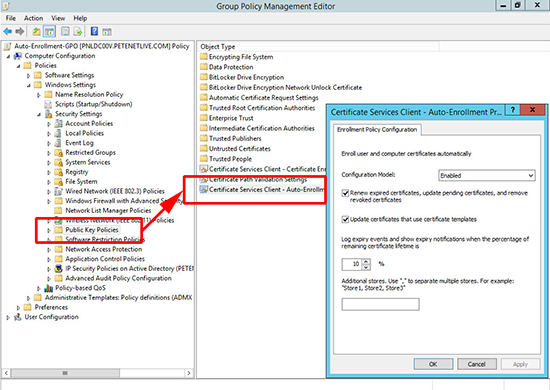
6. For Computer certificate auto-enrollment go to:
Computer Configuration > Windows Settings > Security Settings > Public Key Policies > Certificate Services Client - Auto-Enrolment
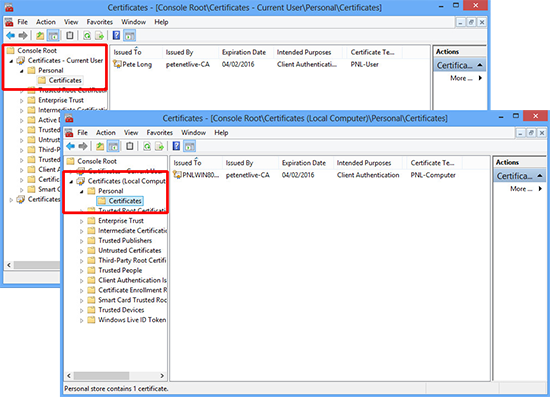
7. Ensure your target machines have their certificates,(user and computer).
***OPTIONAL STEP***
I’m using NDES to put the certificates on my Cisco ASA, and I want to use that same certificate on the ‘outside’ interface of my ASA. Now I could just manually get
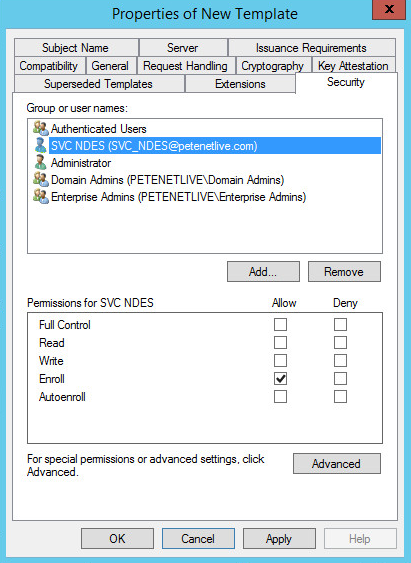
a cert by creating a CSR and giving that to my certificate authority. Then use the ‘Web Server’ template and everything would be peachy. However I want NDES to do ‘EVERYTHING’ for me so I need to make a change to the certificate that NDES uses, (by default ‘IPSEC (Offline request)’). I need to add in the ‘Server Authentication’ Key usage, or when I enable the cert on the outside interface I will get an error. To that end, I need to create a new certificate template, and then get NDES to use that template instead.
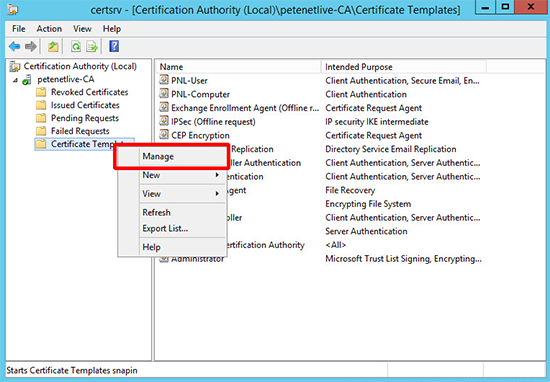
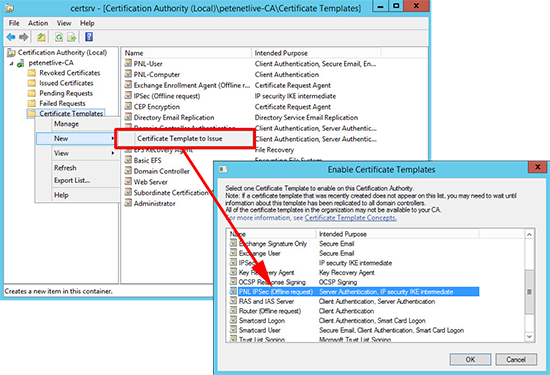
1. Open the Certification Authority management console > Right click Certificate Templates > Manage.
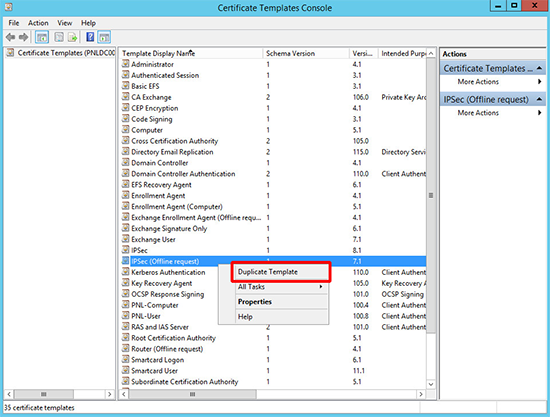
2. Locate ‘IPSEC (Offline request)’ template and clone it.
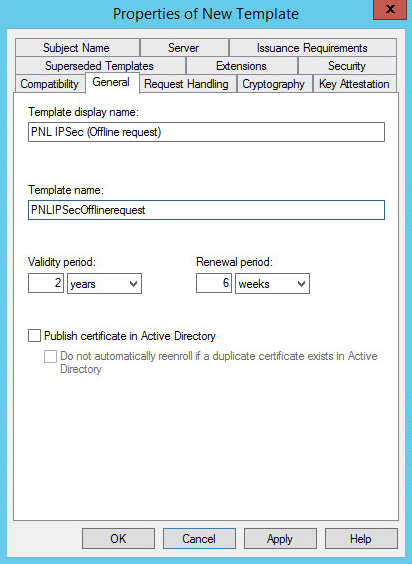
3. Give the cert a name (in the ‘template name’ section leave no spaces or special characters). Then copy the template name to notepad, (you’ll find out why in a minute).
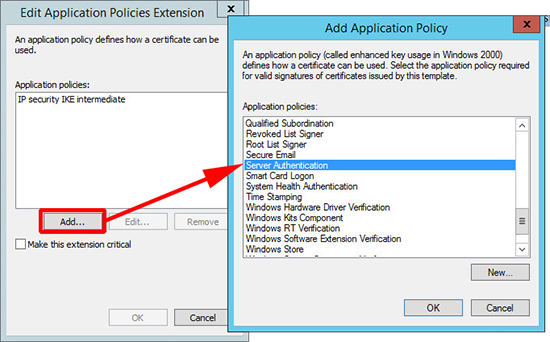
4. Extensions Tab > Application Policies > Edit.
5. Add > Locate and add ‘Server Authentication’ > OK > OK.
6. If you had NDES set up correctly your NDES service account should have enroll rights to this template already, but check to be on the safe side.
7. Save and publish the new template.
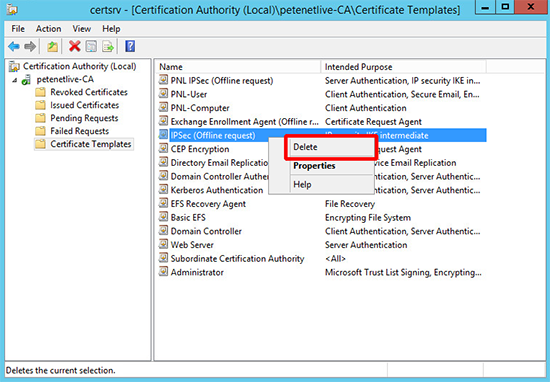
8. Remove the original IPSEC (Offline request) template.
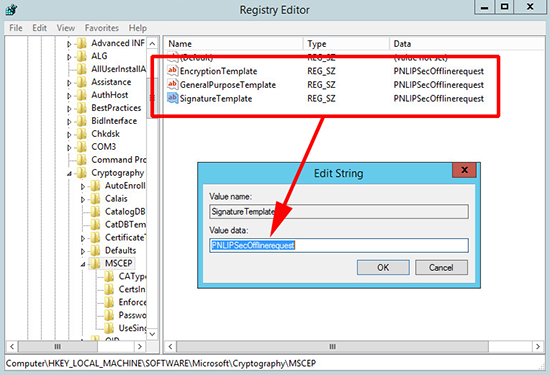
9. To get NDES to use the new template you need to edit three registry values. Open ‘regedit’ an navigate to;
Change the following keys to the new template name;
- EncryptionTemplate
- GeneralPurposeTemplate
- SignatureTemplate
10. At this point you need to restart IIS, though in my case I just rebooted the server.
Related Articles, References, Credits, or External Links
In Part 2 – We will configure the ASA and AnyConnect.