KB ID 0000947
Problem
NDES, is the name for what we used to call MSCEP, which was an ‘add-on’ for the Server 2003 family of servers. In Server 2008 it was renamed to NDES. It is a role service that runs on a Certificate Services Server, and is used to create a registration authority (RA) that can issue certificates from your PKI infrastructure to network devices, i.e. Routers, Firewalls and Switches.
Solution
Installing Network Device Enrollment Service
I’m assuming you already have an Active Directory Certificate Services Server setup, if not you can deploy that and add in NDES at the same time.
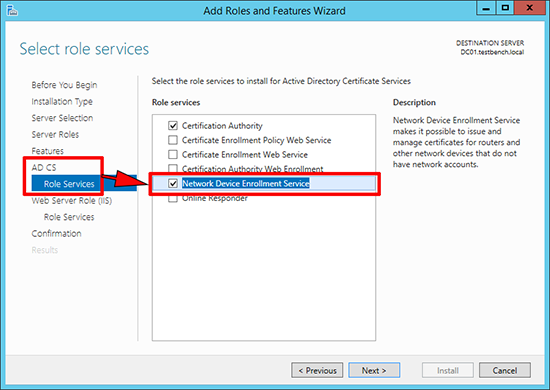
1. Either: Launch Server Manager > Manage > Add Roles and Features > Below Active Directory Certificate Services select Network Device Enrollment Service.
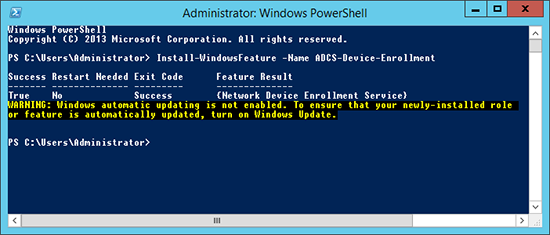
2. Or: From within PowerShell run the following command;
Configuring Network Device Enrollment Service
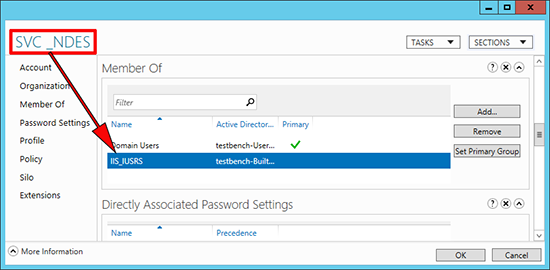
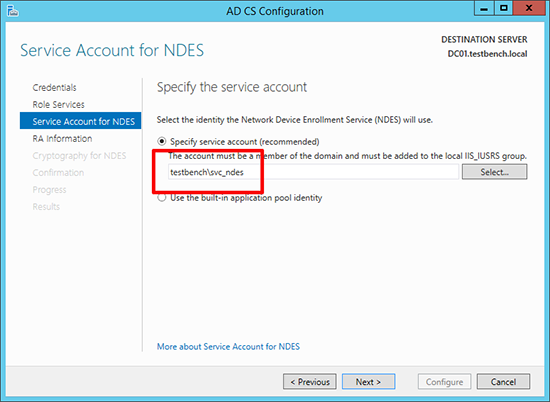
1. Create a domain user (below I’ve called it SVC_NDES) > Add that user to the IIS_IUSRS group on the CA server.
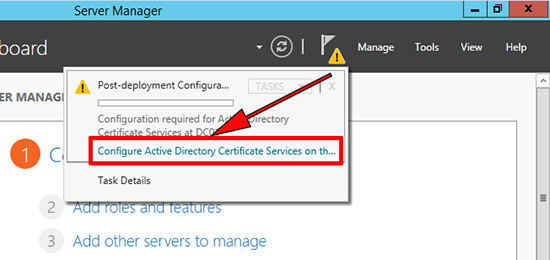
2. From within Server Manager launch the post deployment configuration wizard.
3. Next.
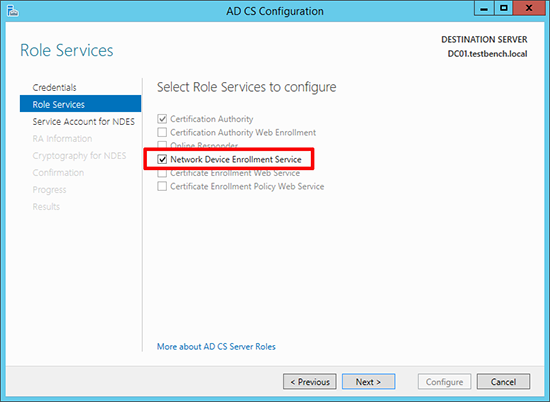
4. Select Network Device Enrollment Service, (if not already selected).
5. Change the account details, to the service account you created above.
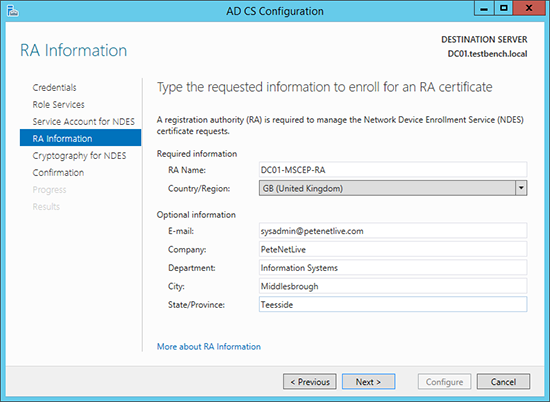
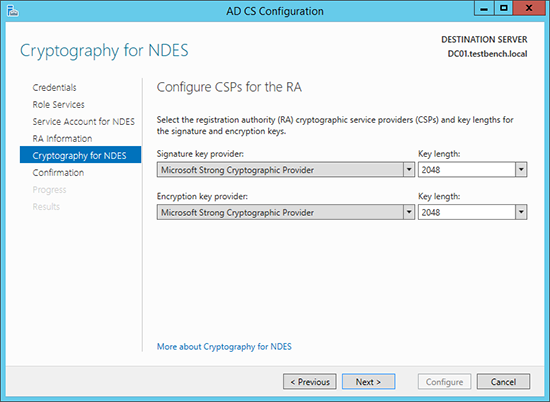
6. Enter the details that will be used to enroll the RA certificate.
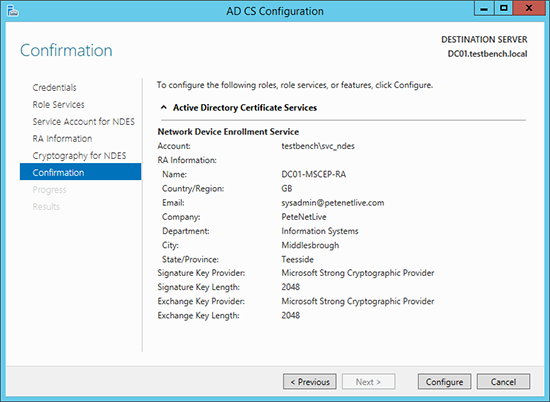
7. Accept the defaults > Next.
8. Configure.
9. Close.
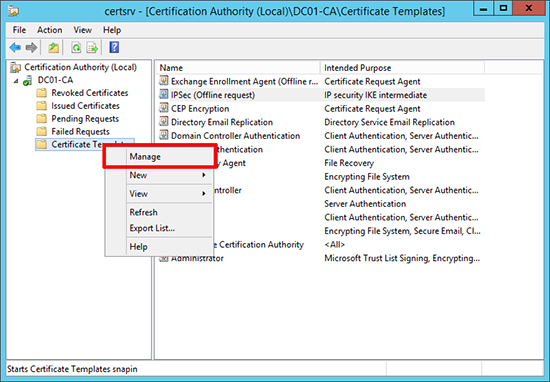
10. Launch the Certificate Authority management console > Certificate Templates > Right Click > Manage.
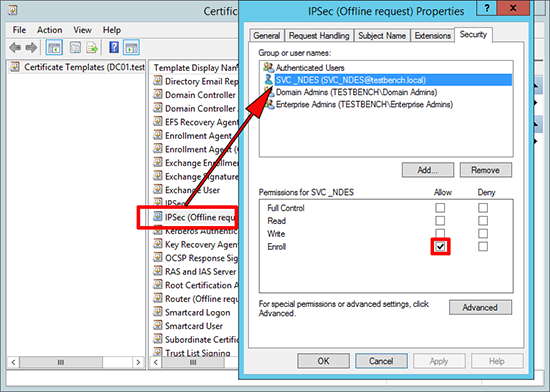
11. Open the properties of the ‘IPSec (Offline request)’ certificate > Security Tab > Make sure the account you created (above) has the ‘Enroll’ permission.
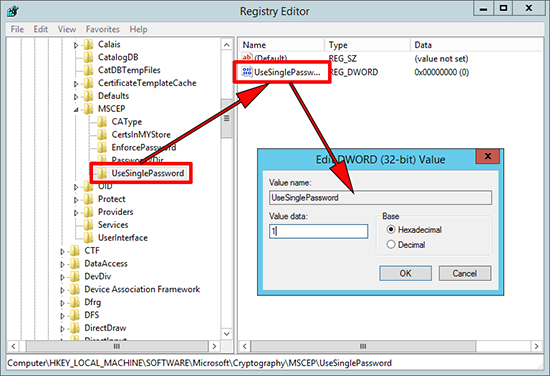
NDES Disable Password Requirement.
I’ve read a few blogs and articles that say;
“There is no way for Cisco devices to supply the required password to enroll with NDES/MSCEP, so you need to disable the requirement for a password.”
This is NOT TRUE, however the whole point of issuing certificates via your PKI infrastructure, is that it can scale dramatically. If you are creating passwords and embedding those passwords in all your enrollments, it can get a little unwieldy. So it may be sensible to remove the password requirement.
1. Windows Key+R > regedit {Enter} > Navigate to;
To disable change the value to 0 (zero).
Update: 22/10/21: You may also need to recycle the SCEP application pool in IIS (on the Certificate Services Server)
From IIS Manager > CA > Application Pools, SCEP. > From the right hand panel > Advanced Settings.
> Set Load User Profile to ‘True‘ > OK.
Again in the right panel > Recycle > From IIS Manager > Sites > Default Web Site. > From the right panel, click Restart.
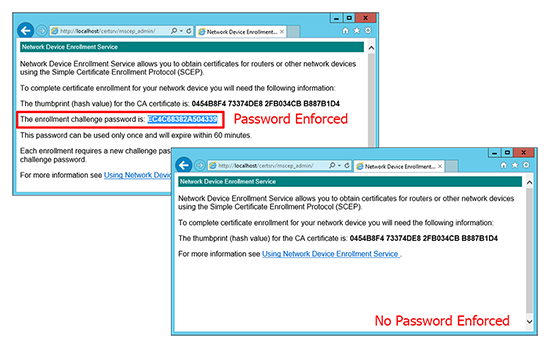
Below you can see the difference, with the password requirement enforced, and without.
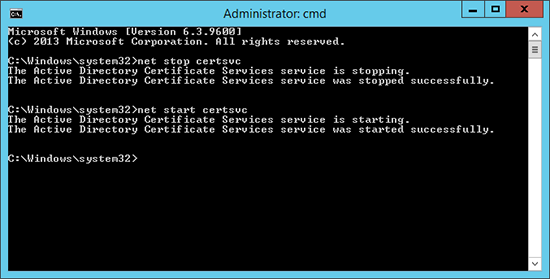
2. Restart the Certificate Services Service;
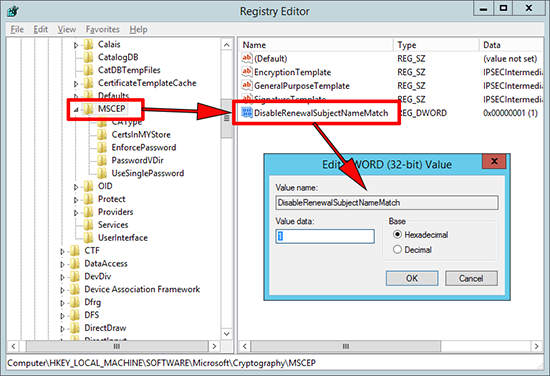
NDES More Password Options and Renewing Certificates
If you do want the more secure option of using passwords, but don’t want to ad a new password every time you have a new enrollment, you can specify that the password does not expire after the default 60 minutes, in fact it never expires. This is handy if you want to renew certificates without generating new passwords. To do that carry out the following procedure;
1. Windows Key+R > regedit {Enter} > Navigate to;
Set the value to 1 (one).
2. Navigate to;
Create a new 32 bit DWORD value called ‘DisableRenewalSubjectNameMatch’ Set the value to 1 (one).
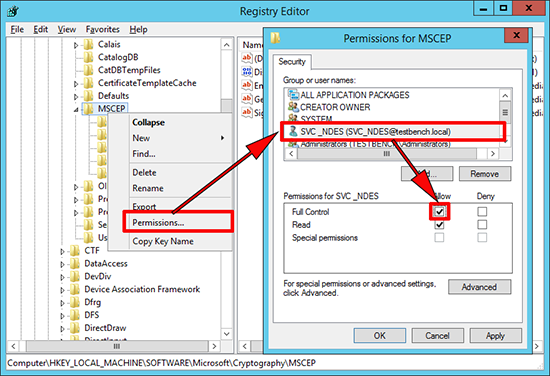
3. If (as above), you are running NDES under a service account, ensure that account has full control of the MSCEP key. (Again don’t forget to restart the Certificate Server service.)
IIS Query String Problem
You may find that with the default IIS settings you may encounter some problems. This is because (by default) IIS will only accept a Query String that’s less than 2048 characters long. If that happens you may see the following errors;
- Request URL Too Long
- HTTP Error 414. The request URL is too long.
- HTTP Error 404.15 – Not Found
- The request filtering module is configured to deny a request where the query string is too long.
In the IIS logs you will see errors like;
2014-05-14 16:12:39 192.168.80.130 GET /certsrv/mscep/mscep.dll/pkiclient.exe operation=GetCACert&message=hsca04 80 – 192.168.80.150 Mozilla/4.0+(compatible;+MSIE+5.0;+Cisco+PKI) 200 0 0 218
2014-05-14 16:12:39 192.168.80.130 GET /certsrv/mscep/mscep.dll/pkiclient.exe operation=PKIOperation&message=<base64 encoded certificate request> 80 – 192.168.80.150 – 404 15 0 15
2014-05-14 16:19:21 192.168.80.130 GET /certsrv/mscep/ operation=GetCACert&message=any 80 – 192.168.80.160 – 200 0 0 328
2014-05-14 16:19:21 192.168.80.130 GET /certsrv/mscep/ operation=PKIOperation&message=<base64 encoded certificate request> 80 – 192.168.80.160 – 404 15 0 703
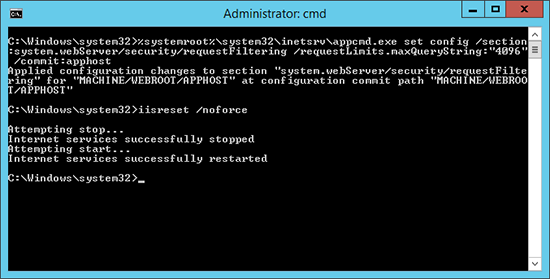
To stop that happening open a command window (Run as Administrator), and execute the following command;
Note: If this ‘wraps’ in your browser, it is one command!
%systemroot%\system32\inetsrv\appcmd.exe set config /section:system.webServer/security/requestFiltering /requestLimits.maxQueryString:"4096" /commit:apphost
Then restart the web services;
Now you can get your network devices to enroll, in the next couple of days, I will post how to enroll from both a Cisco ASA, and a Cisco Router.
Note: If you devices are going to be checking your PKI’s CRL then you will need to set that up.
Windows Certificate Services – Setting up a CRL
Related Articles, References, Credits, or External Links
Cisco ASA – Enrolling for Certificates with NDES
Thanks to Nafti for the heads up in the additional IIS steps.