KB ID 0000764
Problem
As far as Cisco is concerned you can’t upgrade a PIX 506E past version 6.3(5) PIX 506E and 501 Firewall Image and PDM Upgrade
However if you have a spare one lying around and you want to have a play, you CAN get it to version 7.1(2).
Note: It is possible to run the 8.0(2) version of the PIX OS on a 506E, Howerver you need to decompress the image and make some changes to it before it will work (usung lzma.exe). I could not find any decent details on how to do this, and I’m not really a code jockey. If anyone would like to document that and send me the details, I’ll publish it here.
Solution
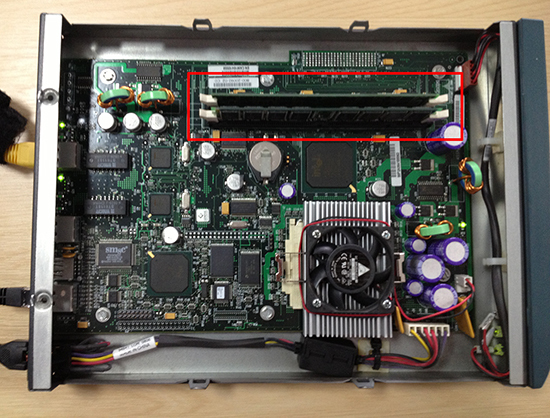
Memory For the PIX 506E
Your first task is to get some more memory in the firewall. There are two slots on the board and only one will be populated with a 32MB PC133 chip. You need to be at AT LEAST 64MB to attempt this upgrade.
Opening the PIX 506E Chassis
What memory Do I need to find? Any PC133 will work, the memory in the firewall is non ECC, so if you locate some ECC memory you will need to replace the on board memory. Because it will not boot if you mix them (I know I tried). It’s not fussy if you use ECC or non ECC, as long as you don’t mix them. (Note: A lot of the ECC memory I found that worked, was ex server RAM, and it was fine, but the chips were “too tall” to get the lid back on the firewall afterwards.)
Can I use PC100? Yes! And you can mix PC100 and PC133, and the firewall will still boot (This is what I did).
Perform the Upgrade
1. Connect to the firewall via console cable, just to prove it’s still version 6, issue a show version command, Note the RAM and version number;
Important: At this point take a copy of the firewall Activation Key!
Petes-PIX> en Password: Petes-PIX# show version Cisco PIX Firewall Version 6.3(5) Cisco PIX Device Manager Version 3.0(4) Compiled on Thu 04-Aug-05 21:40 by morlee Petes-PIX up 1 min 5 secs Hardware: PIX-506E, 64 MB RAM, CPU Pentium II 300 MHz Flash E28F640J3 @ 0x300, 8MB BIOS Flash AM29F400B @ 0xfffd8000, 32KB
Output removed for the sake of space!
Serial Number: 810412141 (0x304de999) Running Activation Key: 0x2d796132 0x68c660cd 0x334cac62 0xcaeddaaa Configuration has not been modified since last system restart. Petes-Pix#
2. Before continuing make sure you have the 7.1(2) version of the PIX Operating system, and you have a TFTP Server set up ready to send you that file. The new OS needs so much flash memory you WILL NOT be able to run the ASDM*. First erase all files from the flash memory and reboot.
*You could try running th ASDM form your TFTP Server.
Petes-PIX# clear flashfs Petes-PIX# show flash flash file system: version:0 magic:0x0 file 0: origin: 0 length:0 file 1: origin: 0 length:0 file 2: origin: 0 length:0 file 3: origin: 0 length:0 file 4: origin: 0 length:0 file 5: origin: 0 length:0 Petes-PIX# reload Proceed with reload? [confirm] Rebooting.
3. Press Esc as the firewall boots to boot into ROMMON mode. Then set it to load its operating system from your TFTP server (here running on my laptop at 172.16.254.207).
Use BREAK or ESC to interrupt flash boot. PRESS ESC Use SPACE to begin flash boot immediately. Flash boot in 10 second. Flash boot interrupted. 0: i8255X @ PCI(bus:0 dev:14 irq:10) 1: i8255X @ PCI(bus:0 dev:13 irq:11) Using 1: i82557 @ PCI(bus:0 dev:13 irq:11), MAC: 0019.aabe.d624 Use ? for help. monitor> address 172.16.254.240 address 172.16.254.240 monitor> server 172.16.254.207 server 172.16.254.207 monitor> file pix712.bin file pix712.bin monitor> tftp tftp pix712.bin@172.16.254.207 ....................................... ...................................................................... ......................................................... Received 6764544 bytes Cisco PIX admin loader (3.0) #0: Tue Mar 14 16:46:07 PST 2006 ##################################################### ##################################################### ##################################################### ##################################################### ##################################################### 64MB RAM Total NICs found: 2 mcwa i82559 Ethernet at irq 11 MAC: 0019.aabe.d624 mcwa i82559 Ethernet at irq 10 MAC: 0019.aabe.d623 BIOS Flash=am29f400b @ 0xd8000 Old file system detected. Attempting to save data in flash Flash filesystem is corrupted (0x0). Could not save data in flash. Initializing flashfs... flashfs[7]: Checking block 0...block number was (-2131)
Output removed for the sake of space!
flashfs[7]: Checking block 61...block number was (0) flashfs[7]: erasing block 61...done. flashfs[7]: 0 files, 1 directories flashfs[7]: 0 orphaned files, 0 orphaned directories flashfs[7]: Total bytes: 7870464 flashfs[7]: Bytes used: 1024 flashfs[7]: Bytes available: 7869440 flashfs[7]: flashfs fsck took 52 seconds. flashfs[7]: Initialization complete. Need to burn loader.... Erasing sector 0...[OK] Burning sector 0...[OK] INFO: Unable to read firewall mode from flash Cisco PIX Security Appliance Software Version 7.1(2) Copyright (c) 1996-2006 by Cisco Systems, Inc.
4. Now the operating system is in memory but if you rebooted the firewall it would not work, you need to configure the IP address, some basic settings, and copy the new OS to the firewall permanently.
pixfirewall> enable Password: pixfirewall# show flash Directory of flash:/ No files in directory 7870464 bytes total (7868416 bytes free) pixfirewall# configure terminal pixfirewall(config)# int Ethernet1 pixfirewall(config-if)# ip address 172.16.254.240 255.255.255.0 pixfirewall(config-if)# nameif inside INFO: Security level for "inside" set to 100 by default. pixfirewall(config-if)# no shutdown pixfirewall(config-if)# exit pixfirewall(config)# global (outside) 1 interface INFO: outside interface address added to PAT pool pixfirewall(config)# nat (inside) 1 0.0.0.0 0.0.0.0 pixfirewall(config)# ping 172.16.254.207 Sending 5, 100-byte ICMP Echos to 172.16.254.207, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/36/180 ms pixfirewall(config)# copy tftp://172.16.254.207/pix712.bin flash Address or name of remote host [172.16.254.207]? Source filename [pix712.bin]? Destination filename [pix712.bin]? Accessing tftp://172.16.254.207/pix712.bin...!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! Writing file flash:/pix712.bin... !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! 6764544 bytes copied in 64.950 secs (105696 bytes/sec) pixfirewall(config)# show flash Directory of flash:/ 5 -rw- 6764544 11:37:32 Feb 08 2013 pix712.bin 7870464 bytes total (1103872 bytes free)
5. Change the firewall so that it uses this file to boot from, save the changes, and then reboot.
pixfirewall(config)# boot system pix712.bin INFO: Converting pix712.bin to flash:/pix712.bin pixfirewall(config)# write mem Building configuration... Cryptochecksum: f59a9bd3 3129b8bc 474b2415 52f2db0f 1049 bytes copied in 0.430 secs [OK] pixfirewall(config)# reload Proceed with reload? [confirm] --- START GRACEFUL SHUTDOWN --- Shutting down isakmp Shutting down File system --- SHUTDOWN NOW --- Rebooting....
6. Post reboot you should be upgraded.
pixfirewall> enable Password: pixfirewall# show version Cisco PIX Security Appliance Software Version 7.1(2) Compiled on Tue 14-Mar-06 17:00 by dalecki System image file is "flash:/pix712.bin" Config file at boot was "startup-config" pixfirewall up 10 secs Hardware: PIX-506E, 64 MB RAM, CPU Pentium II 300 MHz Flash E28F640J3 @ 0xfff00000, 8MB BIOS Flash AM29F400B @ 0xfffd8000, 32KB 0: Ext: Ethernet0 : address is 0019.aabe.d623, irq 10 1: Ext: Ethernet1 : address is 0019.aabe.d624, irq 11 The Running Activation Key is not valid, using default settings: Licensed features for this platform: Maximum Physical Interfaces : 2 Maximum VLANs : 2 Inside Hosts : Unlimited Failover : Not supported VPN-DES : Disabled VPN-3DES-AES : Disabled Cut-through Proxy : Enabled Guards : Enabled URL Filtering : Enabled Security Contexts : 0 GTP/GPRS : Disabled pixfirewall#
6. Finally add the original activation key you took note of in step one back into the firewall.
pixfirewall# configure terminal pixfirewall#(config)# activation-key 0x2d796132 0x68c660cd 0x334cac62 0xcaeddaaa pixfirewall(config)# write mem Building configuration... Cryptochecksum: f59a9bd3 3129b8bc 474b2415 52f2db0f 1049 bytes copied in 0.430 secs [OK] pixfirewall(config)#
Related Articles, References, Credits, or External Links
NA