KB ID 0000050
Problem
Note: This is for Cisco ASA 5500, 5500-x, and Cisco Firepower devices running ASA Code.
Note: This is quite an OLD POST, only use these instructions if you need to create a VPN tunnel that uses IKEv1, (i.e. The other end is not a Cisco ASA, or it’s a Cisco ASA running code older than 8.4). You can still use an IKEv1 tunnel of course, so this article is still valid, it’s just IKEv2 has some better levels of encryption.
Everyone else, go to the following article instead!
Cisco Site To Site VPN IKEv2 “Using CLI”
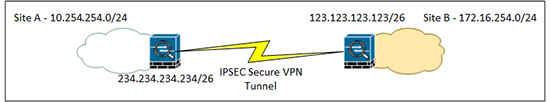
You want a secure IPSEC VPN between two sites.
Solution
Note: There have been a number of changes both in NAT and IKE on the Cisco ASA that mean commands will vary depending on the OS that the firewall is running, make sure you know what version your firewall is running (either by looking at the running config or issue a “sho ver” command).
Note 2: Cisco introduced IKE version 2 with ASA 8.4(x). This assumes we are configuring a tunnel using IKE version 1. (For version 2, both ends need to be running version 8.4(x) or greater).
Before you start – you need to ask yourself “Do I already have any IPSEC VPN’s configured on this firewall?” Because if it’s not already been done, you need to enable ISAKMP on the outside interface. To ascertain whether yours is on or off, issue a “show run crypto ” command and check the results, if you do NOT see “crypto isakmp enable outside” or “crypto ikev1 enable outside” then you need to issue that command.
Firewall Running an OS of 8.4(x) or newer PetesASA# show run crypto crypto ikev1 enable outside << Mines already enabled and its IKE version1 crypto ikev1 policy 10 authentication pre-share encryption 3des hash sha group 2 lifetime 86400 PetesASA# Firewall Running an OS Earlier than 8.4(x) PetesASA# show run crypto crypto isakmp enable outside << Mines already enabled. crypto isakmp policy 10 authentication pre-share encryption 3des hash sha group 2 lifetime 86400 PetesASA#
1. I’m going to create access control lists next, one to tell the ASA what is “Interesting traffic”, that’s traffic that it needs to encrypt. If you are running an ASA older than version 8.3(x) you will need to create a second access list to STOP the ASA performing NAT on the traffic that travels over the VPN.
Warning: (ASA Version 8.3 or older): If you already have NAT excluded traffic on the firewall (for other VPN’s) this will BREAK THEM – to see if you do, issue a “show run nat” command, if you already have a nat (inside) 0 access-list {name} entry, then use that {name} NOT the one in my example.
So below I’m saying “Don’t NAT Traffic from the network behind the ASA (10.254.254.0) that’s going to network behind the VPN device at the other end of the tunnel (172.16.254.0).
Firewall Running an OS of 8.3(x) or newer PetesASA(config)#object network Site-A-SN PetesASA(config-network-object)#subnet 10.254.254.0 255.255.255.0 PetesASA(config)#object network Site-B-SN PetesASA(config-network-object)#subnet 172.16.254.0 255.255.255.0 PetesASA(config)#access-list VPN-INTERESTING-TRAFFIC line 1 extended permit ip object Site-A-SN object Site-B-SN PetesASA(config)#nat (inside,outside) source static Site-A-SN Site-A-SN destination static Site-B-SN Site-B-SN no-proxy-arp route-lookup Firewall Running an OS Earlier than 8.3(x) PetesASA(config)# access-list VPN-INTERESTING-TRAFFIC line 1 extended permit ip 10.254.254.0 255.255.255.0 172.16.254.0 255.255.255.0 PetesASA(config)# access-list NO-NAT-TRAFFIC line 1 extended permit ip 10.254.254.0 255.255.255.0 172.16.254.0 255.255.255.0 PetesASA(config)#nat (inside) 0 access-list NO-NAT-TRAFFIC
2. Now I’m going to create a “Tunnel Group” to tell the firewall it’s a site to site VPN tunnel “l2l”, and create a shared secret that will need to be entered at the OTHER end of the site to site VPN Tunnel. I also set a keep alive value.
Note: Ensure the Tunnel Group Name is the IP address of the firewall/device that the other end of the VPN Tunnel is terminating on.
PetesASA(config)# tunnel-group 123.123.123.123 type ipsec-l2l PetesASA(config)# tunnel-group 123.123.123.123 ipsec-attributes PetesASA(config-tunnel-ipsec)# pre-shared-key 1234567890 PetesASA(config-tunnel-ipsec)# isakmp keepalive threshold 10 retry 2 PetesASA(config-tunnel-ipsec)# exit
3. Now we need to create a policy that will setup how “Phase 1” of the VPN tunnel will be established, we have already put in a shared secret, this policy will make sure we use it. It also sets the encryption type (3DES), the hashing algorithm (SHA) and the Level of PFS (Group 2). Finally it sets the timeout before phase 1 needs to be re-established. It sets the timeout value to 86400 seconds (that’s 1440 Minutes – or 24 hours if your still confused 🙂 ).
Firewall Running an OS of 8.4(x) or newer PetesASA(config)# crypto ikev1 policy 10 PetesASA(config-ikev1-policy)#authentication pre-share PetesASA(config-ikev1-policy)#hash sha PetesASA(config-ikev1-policy)#group 2 PetesASA(config-ikev1-policy)#lifetime 86400 Firewall Running an OS Earlier than 8.4(x) PetesASA(config)# crypto isakmp policy 10 authen pre-share PetesASA(config)# crypto isakmp policy 10 encrypt 3des PetesASA(config)# crypto isakmp policy 10 hash sha PetesASA(config)# crypto isakmp policy 10 group 2 PetesASA(config)# crypto isakmp policy 10 lifetime 86400
4. We stated above that we are going to use 3DES and SHA so we need a “Transform Set” that matches.
Firewall Running an OS of 8.4(x) or newer PetesASA(config)# crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac Firewall Running an OS Earlier than 8.4(x) PetesASA(config)# crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
5. Finally we need to create a “Cryptomap” to handle “Phase 2” of the VPN Tunnel, that also will use 3DES and SHA and PFS. And last of all we apply that Cryptomap to the outside interface.
Firewall Running an OS of 8.4(x) or newer PetesASA(config)# crypto map outside_map 1 match address VPN-INTERESTING-TRAFFIC PetesASA(config)# crypto map outside_map 1 set pfs group2 PetesASA(config)# crypto map outside_map 1 set peer 123.123.123.123 PetesASA(config)# crypto map outside_map 1 set ikev1 transform-set ESP-3DES-SHA PetesASA(config)# crypto map outside_map interface outside Firewall Running an OS Earlier than 8.4(x) PetesASA(config)# crypto map outside_map 1 match address VPN-INTERESTING-TRAFFIC PetesASA(config)# crypto map outside_map 1 set pfs group2 PetesASA(config)# crypto map outside_map 1 set peer 123.123.123.123 PetesASA(config)# crypto map outside_map 1 set transform-set ESP-3DES-SHA PetesASA(config)# crypto map outside_map interface outside
5. Don’t forget to save your hard work with a “write mem” command.
PetesASA(config)#
PetesASA(config)# write mem
Building configuration...
Cryptochecksum: 5c8dfc45 ee6496db 8731d2d5 fa945425
8695 bytes copied in 3.670 secs (2898 bytes/sec)
[OK]
PetesASA(config)#
6. Simply configure the other end as a “Mirror Image” of this one.
ASA 5500 Site to Site VPN Copy and Paste Config
Note: This uses AES and SHA. It also assumes your outside interface is called ‘outside’. Check! I’ve seen them called Outside (capital O), wan, and WAN.
crypto ikev1 enable outside crypto ikev1 policy 10 authentication pre-share encryption aes-256 hash sha group 2 lifetime 86400 ! object network OBJ-MainSite subnet 10.0.0.0 255.255.255.0 object network OBJ-RemoteSite subnet 10.0.3.0 255.255.255.0 ! access-list VPN-INTERESTING-TRAFFIC extended permit ip object OBJ-MainSite object OBJ-RemoteSite nat (inside,outside) source static OBJ-MainSite OBJ-MainSite destination static OBJ-RemoteSite OBJ-RemoteSite no-proxy-arp route-lookup ! tunnel-group 2.2.2.2 type ipsec-l2l tunnel-group 2.2.2.2 ipsec-attributes pre-shared-key 1234567 isakmp keepalive threshold 10 retry 2 ! crypto ipsec ikev1 transform-set VPN-TRANSFORM esp-aes-256 esp-sha-hmac ! crypto map CRYPTO-MAP 1 match address VPN-INTERESTING-TRAFFIC crypto map CRYPTO-MAP 1 set pfs group2 crypto map CRYPTO-MAP 1 set peer 2.2.2.2 crypto map CRYPTO-MAP 1 set ikev1 transform-set VPN-TRANSFORM crypto map CRYPTO-MAP interface outside
Simply change the values in red where;
- 10.0.00 255.255.255.0 is the network behind the ASA you are working on.
- 10.0.3.0 255.255.255.0 is the destination network behind the device you are connecting to.
- 2.2.2.2 is the peer IP address of the device you are attempting to connect to.
- 1234567 Is the shared secret you will use at both ends.
Related Articles, References, Credits, or External Links
Original Article Written 07/06/11, updated 20/04/14