KB ID 0001705
Problem
Well the ASA5516-X was the last one to go end of sale. You may be able to get stock of the remainder of the ASA5500-X series as people clear their shelves, or they may be available as ‘refurb’ stock but they are disappearing.
So you would think that the replacements would be better documented? Well it’s sketchy at best, and when you look a the data sheets for the new FPR range the links on Cisco website go to the wrong place, or give you little or no guidance 🙁
Solution
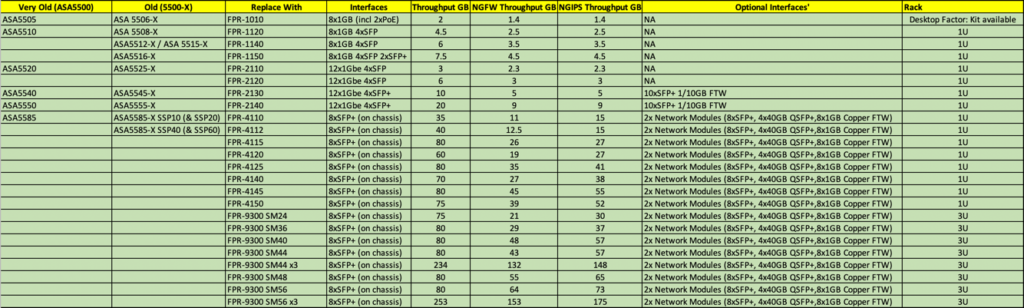
I’ve put together the following to help, it’s not sanctioned by Cisco, (though I did engage Cisco Partner GVE to assist me. The following table shows FPR models that run ASA code, (not FTD code). I’m not a fan personally of the FTD solution, and I wont be deploying it anywhere for a client. But Standard Asa code keeps my support and network techs happy.
If you disagree with any of my recommendations, please post below, and (providing your objection is valid,) and I’ll update it accordingly.
Related Articles, References, Credits, or External Links
NA


02/10/2020
Very useful post Pete – thanks for sharing. I was coincidentally just working on a customer ASA replacement bill of materials when I saw your newsletter with the link to this article pop up in my mailbox. Very timely!
I might suggest that given an ASA 5525-X throughput is only around 1 Gbps (2 Gbps best case in the lab) that a Firepower 1120 or so would fit the bill as a 1-1 replacement. The 2100 series would certainly work as well with more future growth capacity.
05/10/2020
Hi Marvin,
I don’t disagree, that’s one of the few models that Cisco actually have a decent recommendation for! ‘I think’ their thinking is its a modern replacement for, the FPR throughput on all models is considerably better pound for pound but that they are a LOT newer. 🙂
P
05/10/2020
Can I still take advantage of Firepower’s services (AMP, IPS, URL, etc.) and run ASA code on the new generation of devices similar to how it works today? Like you, I find the FTD to be incomplete. It seems they are forcing you to FTD if you want to leverage any of the firepower services. Am I right?
05/10/2020
Nope, if you run ASA code on a FTD/FPR device, there is no SFR module to run the ‘old’ firepower on.
16/10/2020
Hi, Pete,
first of all, thank you very much for your detailed summary and great contributions!
Just like “Rob R” I was looking for an answer to the question.
Currently we use a 5516-X with SFR + TAMC Subscription.
If I understood that correctly, Cisco will soon only sell FPxxxx models instead of ASA55XX-X models.
I’m a friend of the ASA code just like you. But seriously, what’s the point of replacing ours with an FPR-1150 and putting ASA code on it but not being able to use IPS/FirePOWER (TAMC) features ? Is such a firewall without these security features still up-to-date ? Or am I missing something massively ?
16/10/2020
>>Cisco will soon only sell FPxxxx models instead of ASA55XX-X models.
That is correct 🙂
>>But seriously, what’s the point of replacing ours with an FPR-1150 and putting ASA code on it
>>but not being able to use IPS/FirePOWER (TAMC) features ? Is such a firewall without these
>>security features still up-to-date ? Or am I missing something massively?
I agree, remember firepower on the 5500-X was sort of ‘shoe horned’ into the firewall it had to run on its own Kernel on its own module. With FPR the chassis are designed to run either FTD or ASA code, but if it’s running ASA code, there’s no separate chip or module any more. Thats the real reason why.
P
17/10/2020
Hi Pete, Your site has been a lifesaver for me – so many times. Thanks!!
Quick question
>I’m not a fan personally of the FTD solution, and I wont be deploying it anywhere for a client.
So which solution(s) are you a fan of?
Cheers,
19/10/2020
I’m sticking with ASA on the FPR platform for now.
22/10/2020
Is anyone else a little worried that Cisco will eventually no longer support the ASA code? It sounds like Cisco is just buying time to develop FirePower and will eventually tell all of us ASA folks to take a hike.
I have been a Cisco firewall fan since the PIX days. I work for a MSP, and we have exclusively sold and implemented Cisco ASAs up until now. For us, the ASA may not have had all the bells and whistles but was affordable and reliable. The new FPR model has us looking at other Vendors. The main reason has to do with the fact that several features aren’t available on the FPR running the ASA code, i.e. Link Aggregation and IPS. I started to play with FirePower OS and lost interest immediately when I tried to make simple changes through the CLI (is it even possible to make changes via CLI?). Don’t get me wrong, I’m all about change, innovation, and moving forward. Therefore, we decided to look at other options. All our techs will have to learn a brand-new platform whether we stick with Cisco or go with something else. We might as well use this time to see what else is out there.
Let me tell you, Cisco is behind the eight ball. The other players have surpassed Cisco if you ask me.
Pete, thank for all of the Cisco ASA articles that you have published over the years. You Rock!
26/10/2020
Thanks Brandon, I agree, in my day job we are starting to look at Fortigate, as a replacement. I’m the Cisco ASA champion and I really cant defend Cisco firewalls any more. I’ll be deploying a few FPR in the mean time. But the writing is on the wall.
Thanks for the feedback!
27/10/2020
For anyone else taking the plunge.
We shopped Fortigate, Sonicwall, Meraki, Palo Alto, and Juniper. I have spent the last 10 years throwing out Sonicwalls and of course that’s what we decided to go with. The irony!
Sonicwall seems to be in touch with the SMB and MSP industry. The biggest selling point for us was that Sonicwall has a cloud hosted, multi-tenant, management portal to manage firewalls. The new TZ570 and TZ670 appliances can get up to 5gbps of throughput (so they say) which is awesome for a SMB unit.
Fortinet was on point, but a few of my colleagues who had previously used the Fortigate central management UI said it was very buggy and they had a lot of problems with it.
Palo Alto – I have heard great things but never heard back from their sale people.
Juniper – Same as Palo
Meraki – The lack of a remote VPN client turned us off. But oh by the way, Meraki will be integrating Anyconnect very soon. There is a beta program already in progress
05/03/2021
Hi, I’m currently running a 5516x with asa and firepower module (sensor) and a seperate VM for FMC. Looking to replace with a FPR-1120. How do I manage FMC if there is no firepower module? I guess I’m forced to go FTD if I want to have the NGFW-capabilites (URL, Malware, IPS) and have the FMC experince and policy setup?
05/03/2021
Spot on yes, or go Fortigate, which is what most of my clients are doing.
24/03/2021
Hi Pete! Thanks for the ASA code summary! The other point is not to go for the NGFW features is subscription model. Every year you have to pay nearly half of hardware price for TAMC license. Not much customers likes it.
19/07/2024
I used to be a long-time IOS and ASA tech being CCNA since 1999. In 2018 I decided to take a career hairpin into the IT legal field, and for several reasons, 2024 sees me back in the chicken shack of my old business. One of my first tasks was to take over a few ASAs 5525X on code from 2017. (I should add that I found a STACK of untouched, new ones here). Learning that these boxes are EOS I keep guessing I need to replace them. Can someone re-rail me a little bit on what to go for – general tips are very welcome, too.
26/07/2024
FPR-1000 or 2000 series (preferably runnig ASA code) look at the data sheets and see which suits your needs best. Or Fortigate 101/201 again depending on your needs.
P