KB ID 0001656
Problem
I did a Duo run through a few weeks ago, and to be honest their documentation is usually pretty good. I was spinning this up as a PoC for a client so I thought I’d put my take on the procedure here.
ADFS Duo Pre-Requisites
I already have a Duo Authentication Proxy server setup and my users are enrolled, you will need to set this up first. See the following article;
Duo: ADSync and Enroll Users via SMS
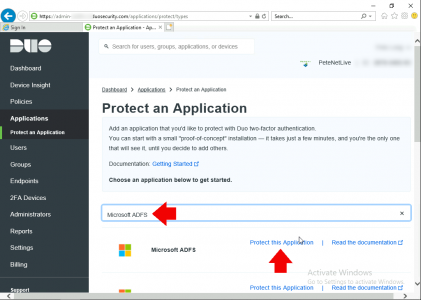
Log into the the Duo Admin Portal > Applications > Protect an Application > Search for and select Microsoft ADFS > Protect This Application.
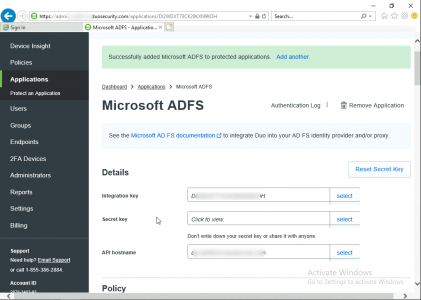
Copy the Integration Key, Secret Key and the API hostname to notepad.
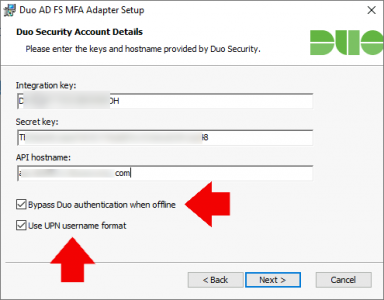
Download the Duo AD FA MFA Adapter on your ‘first‘ ADFS server. Enter the information you copied to Notepad, (above). Tick ‘Bypass Duo Authentication when offline’, and because my users are logging on with their Office 365 UPNs, I’m also ticking ‘Use UPN username format’ (SEE USERNAME NORMALISATION NOTE BELOW.)
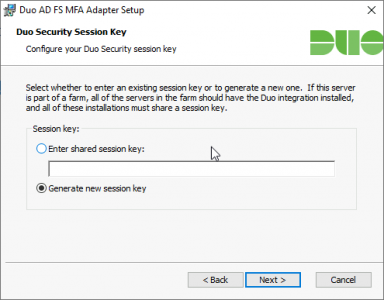
Note: I only have one ADFS server, if you have an ADFS Server farm you will need to install each one with the SAME shared session key, you can generate one of these yourself in PowerShell with the following commands;
$bytes = new-object "System.Byte[]" 30 (new-object System.Security.Cryptography.RNGCryptoServiceProvider).GetBytes($bytes) [Convert]::ToBase64String($bytes)
I only have one, so I’ll simply ‘Generate new session key‘ > Finish the install wizard.
Note: If one has already been deployed, and you don’t know the key, go to the ADFS server on which it’s working, and look in the following registry key.
HKEY_LOCAL_MACHINE\SOFTWARE\Duo Security\DuoAdfs\AKey
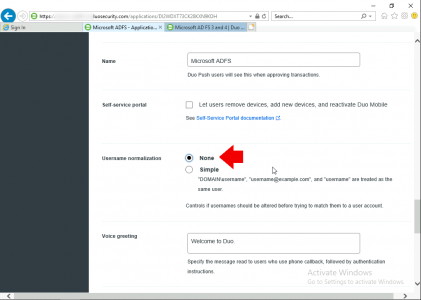
USERNAME NORMALISATION: Because I’m logging users on with UPNs (first-name.last-name.domain-name.com) Back in the Duo Portal under protected applications Microsoft ADFS > Set username normalisation to ‘None” > Scroll down and save the change.
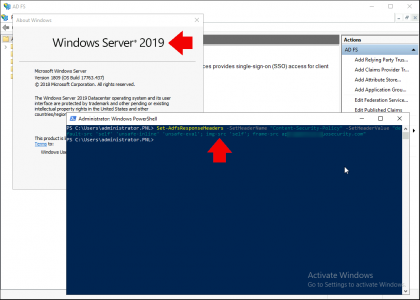
Server 2019 Only: I’m deploying on Server 2019 so I also need to execute the following Powershell command, you will need to enter YOUR API Hostname (you copied above).
Set-AdfsResponseHeaders -SetHeaderName "Content-Security-Policy" -SetHeaderValue "default-src 'self' 'unsafe-inline' 'unsafe-eval'; img-src 'self'; frame-src api-xxxxxxxx.duosecurity.com"
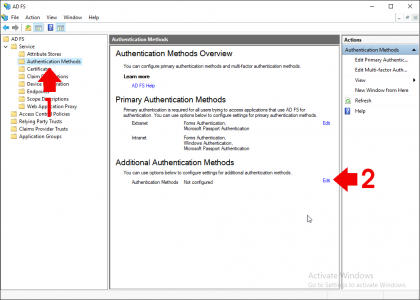
Launch the ADFS Management Console > Authentication Methods > Additional Authentication Methods > Edit.
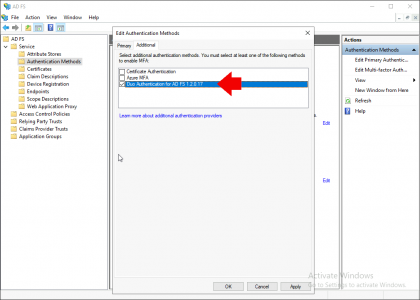
Tick ‘Duo Authentication for AD FS {version}’ > Apply > OK.
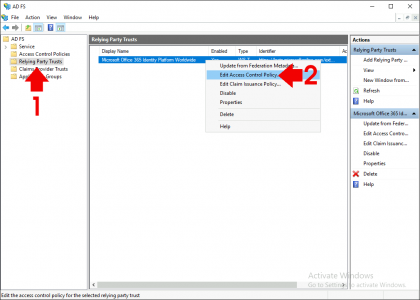
Relying Party Trust > Here I have my Office 365 trust, yours may be for something else! Edit Access Control Policy.
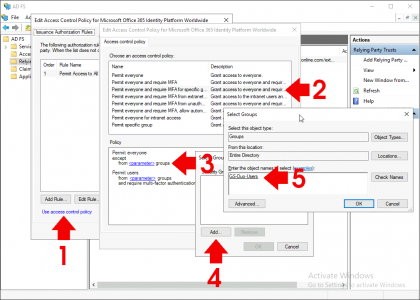
Click ‘Use Access Control Policy’ > The one I want is ‘Permit Everyone and Require MFA for Specific Group‘. This way I can select who gets 2FA challenged, and I can migrate users slowly into this group once I know they are enrolled, (also I use the same group to Sync the users to Duo to make things simple). Change the <parameter> and locate you domain security group.
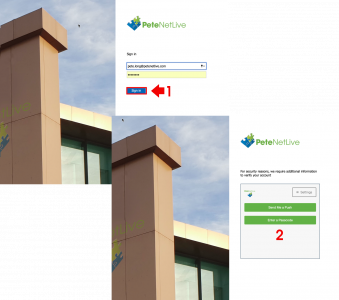
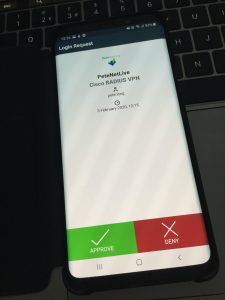
Now when the users connect to ADFS, after they logon, they are challenged to provide 2FA authentication.
like so;
Related Articles, References, Credits, or External Links
NA

08/10/2020
Thank you. I didn’t know about the additional PowerShell requirement for 2019. This article really helped me out. I just sent you a donation. Keep up the good work.
08/10/2020
Thanks David! Glad to help.