KB ID 0001494
Problem
I had this problem after a VMware host upgrade last night, this domain controller would not boot, I tried ‘Last Known Good Configuration’, I tried ‘Safe Mode’ it would not boot. More out of desperation than procedure, I tried to boot to ‘Directory Services Restore Mode’ and it booted up (hooray!) I tried all the client’s usual passwords, and could not log in, I messaged them to ask for the DSRM password, and tried all the ones they sent me, it seems I was defeated!
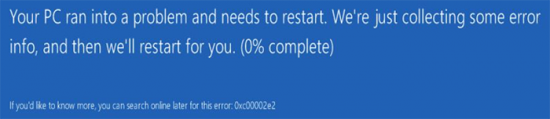
They had other domain controllers, and their critical systems were up, so I arranged for this server to be restored the following morning from tape.
A lot of you will (I hope) know your DSRM password, so you have less problems that I had, so you can skip reseting the DSRM password part.
Reset DSRM Password (From Boot Disk)
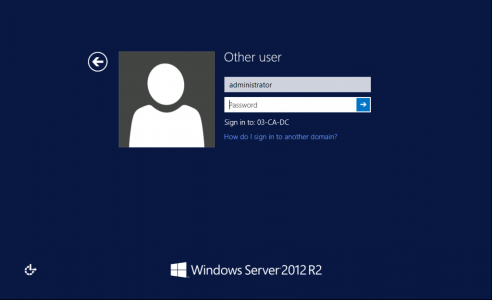
If you Google resetting the DSRM password you get a ton of posts telling you to use ntdsutil, which is great if you can logon, but I could not. I’ll let you into a secret: The DSRM password is actually the LOCAL administrators password on the Domain Controller, and resetting the local admin password, (using a Linux boot disk, {don’t panic it’s simple!}) well we have been able to do this since the days of NT4! (DON’T PAY FOR A UTILITY TO DO THIS).
To download the boot disk and see how this is done follow the instructions I’ve already written in THIS POST. The only difference is, I chose to {blank} the password, rather than reset it, (you can reset it afterwards using ntdsutil if you want to).
Select option 1: Clear (blank) user password;
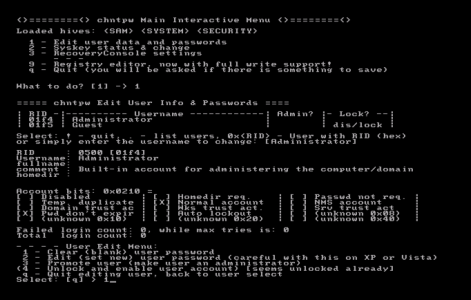
Boot Into DSRM Mode and Repair Active Directory
You can now boot into DSRM mode, (if you don’t see these options Press F8 as the server boots).
As soon as you enter ‘administrator’ and then click in the password box, the ‘Sign in to‘ option will change from the domain name to the domain controllers name. This usually happens on all machines, that are NOT domain controllers, but in this case, it’s expected behaviour, (as we will be logging in with a LOCAL password.) Remember I blanked the password, so I’m leaving it empty.
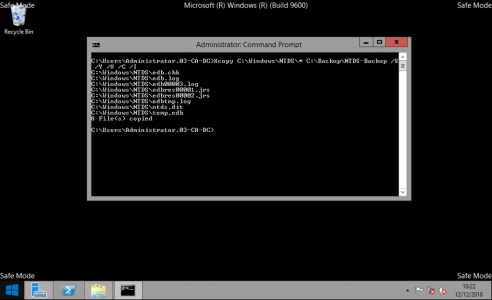
First let’s take a backup of AD. Open a command window, and execute the following command;
xcopy C:\Windows\NTDS\* C:\Backup\NTDS-Backup /E /Y /V /C /I
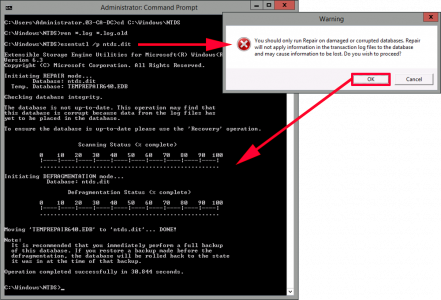
Then execute the following commands;
cd C:\Windows\NTDS ren *.log *.log.old esentutl /p C:\Windows\NTDS\ntds.dit
When prompted; CLICK OK.
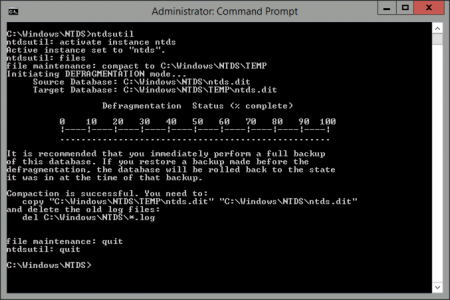
Now run the following commands;
ntdsutil activate instance ntds files compact to C:\Windows\NTDS\TEMP quit quit
As it’s telling us (above), we now need to copy the compacted and repaired database, over the top of the live database, and then get rid of the logs. To do that, run the following commands;
copy "C:\Windows\NTDS\TEMP\ntds.dit" "C:\Windows\NTDS\ntds.dit" Yes del *.log del *.log.old shutdown -r -f
The server will reboot, and boot back into Windows as normal.
Related Articles, References, Credits, or External Links
A big thank you to Alex at iThinkVirtual.com, for the AD repair procedure, I would not have got over the line without his excellent ‘Fixing a corrupt Domain Controller’ post.


12/06/2022
Thank you so much for this article, you saved me 🙂
28/06/2022
thanks you, this save me from hours of work!
best regards,