KB ID 0001474
Problem
A few years ago I replaced a firewall that was setup like this, and while it took me a while to work out what was going on, I remember thinking it was an elegant solution. Fast forward to today, and I’m now working with the guy who set it up! (Kudos to Paul White).
So when I had a client with a similar requirement, I sat down fired up the lab, and documented it.
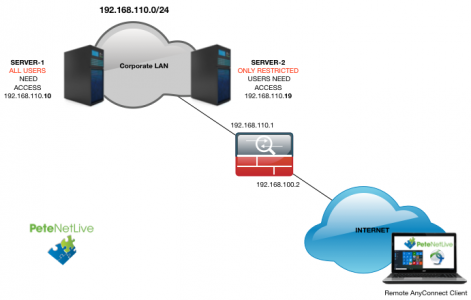
What was used;
- Windows 10 Remote Client
- AnyConnect v4 Client
- Server 2016 NAP (NPAS) Server
- Windows 2016 Domain.
- Cisco vASA (v9.2)
Solution
Deploy Microsoft NAP
Rather than reinvent the wheel, I’ve already ran though this. Use the link (below) to install the role, add the ASA as a RADIUS client, then return here (before configuring any policies!)
Windows Server 2016 & 2012 Setup RADIUS for Cisco ASA 5500 Authentication
Configure NAP Network Policies For Group Authentication
Firstly you will need some groups setup in AD, with some users in them, for testing.
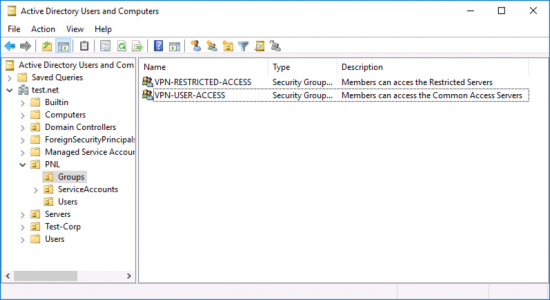
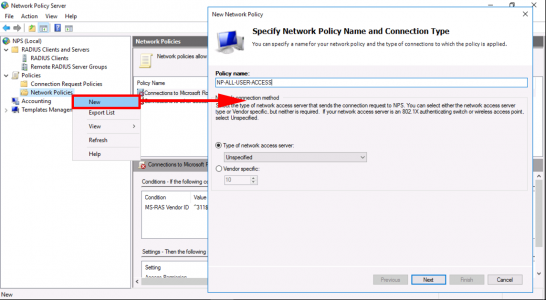
Then, on your NAP Server create a Network Policy (for each group), like so;
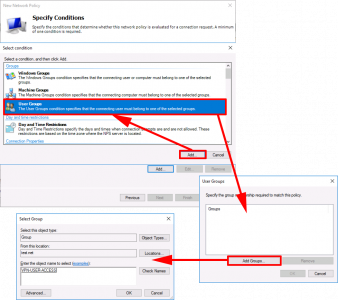
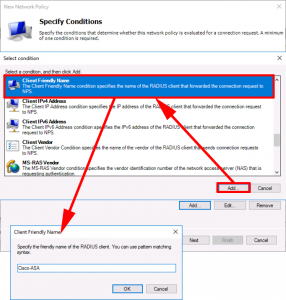
Add the ‘User Group Condition’ with the correct AD Group for this policy.
Add the ‘Client Friendly Name‘ condition, and set to to the name you used for the RADIUS client.
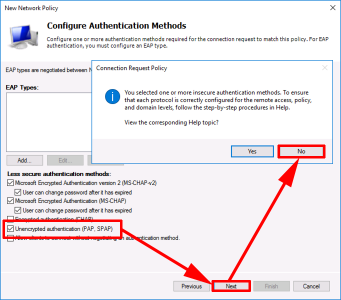
Next > Next > Add in ‘Unencrypted (PAP SPAP)‘ > Next > No.
Next > Add > Select ‘Class’ > Add > Enter ‘ou={Name-of-Cisco-Group-Policy-To-Apply}‘ > OK > Close > Next > Finish.

Cisco ASA Configuration
First, configure RADIUS AAA;
!
aaa-server PNL-RADIUS protocol radius
aaa-server PNL-RADIUS (inside) host 192.168.110.19
key 666999
radius-common-pw 666999
exit
!
Create a ‘Pool’ of IP addresses for the remote clients;
!
ip local pool POOL-ANYCONNECT-SN 192.168.249.1-192.168.249.254 mask 255.255.255.0
!
Create some ‘Objects’ one for the Pool you created above, one for the server(s) that everyone can access, and one for the server(s) only restricted users can access;
!
object network OBJ-ANYCONNECT-SN
subnet 192.168.249.0 255.255.255.0
!
object-group network OBJ-USER-ACCESS-SERVERS
description Servers than can be accessed by VPN-USER-ACCESS AD Group
network-object host 192.168.110.10
!
object-group network OBJ-RESTRICTED-ACCESS-SERVERS
description Servers than can only be accessed by VPN-RESTRICTED-ACCESS AD Group
network-object host 192.168.110.19
!
Enable Webvpn and AnyConnect;
!
webvpn
enable outside
no tunnel-group-list enable
anyconnect image disk0:/anyconnect-win-4.6.00362-webdeploy-k9.pkg 1
anyconnect image disk0:/anyconnect-macos-4.6.00362-webdeploy-k9.pkg 2
anyconnect enable
!
Create the ACLs for your TWO AD user groups;
!
access-list ACL-VPN-USER-ACCESS-SERVERS extended permit ip object-group OBJ-USER-ACCESS-SERVERS object OBJ-ANYCONNECT-SUBNET
!
access-list ACL-VPN-RESTRICTED-ACCESS-SERVERS permit ip object-group OBJ-USER-ACCESS-SERVERS object OBJ-ANYCONNECT-SUBNET
access-list ACL-VPN-RESTRICTED-ACCESS-SERVERS permit ip object-group OBJ-RESTRICTED-ACCESS-SERVERS object OBJ-ANYCONNECT-SUBNET
!
Stop NAT being performed on the remote AnyConnect traffic;
!
nat (inside,outside) 1 source static any any destination static OBJ-ANYCONNECT-SN OBJ-ANYCONNECT-SN no-proxy-arp route-lookup
!
Each Group-Policy (below) wont have its own tunnel-group so you need to enable RADIUS on the default web tunnel-group, and assign the IP Pool you created (above). Note: I’m allowing authentication to fall back to LOCAL in case the RADIUS server fails;
!
tunnel-group DefaultWEBVPNGroup general-attributes
authentication-server-group PNL-RADIUS LOCAL
address-pool POOL-ANYCONNECT-SN
!
Finally, create a group-policy that the NAP server will tell the ASA to allocate to the users of the AD Groups (VPN-USER-ACCESS, and VPN-RESTRICTED-USER-ACCESS);
!
group-policy GP-USER-ACCESS-SERVERS internal
group-policy GP-USER-ACCESS-SERVERS attributes
dns-server value 192.168.110.10
vpn-idle-timeout 30
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value ACL-VPN-USER-ACCESS-SERVERS
default-domain value test.net
!
group-policy GP-RESTRICTED-ACCESS-SERVERS internal
group-policy GP-RESTRICTED-ACCESS-SERVERS attributes
dns-server value 192.168.110.10
vpn-idle-timeout 30
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value ACL-VPN-RESTRICTED-ACCESS-SERVERS
default-domain value test.net
!
Related Articles, References, Credits, or External Links
Thanks to Paul White and Trevor Stanley.
Windows Server 2016 & 2012 Setup RADIUS for Cisco ASA 5500 Authentication
Windows Server 2008 R2 – Configure RADIUS for Cisco ASA 5500 Authentication
Cisco ASA5500 Client VPN Access Via RADIUS (Server 2003 & IAS)
Cisco – Testing AAA Authentication (Cisco ASA and IOS)

30/10/2018
Add code below and you can skip use Unencrypted (PAP SPAP) and use MS-CHAPv2 insteed.
tunnel-group DefaultWEBVPNGroup general-attributes
password-management
21/03/2020
Great!!
Tks so much!!
12/07/2020
There seems to be something wrong with the ACLs and NO-NAT statement, it is reversed.
14/07/2020
No they are correct.
24/09/2020
is it posible for the anyconnect to usea a diferent GROUP-POLICY than the one define on the tunnel-group?
This is the configuration:
!—————————————————-!
!
tunnel-group AnyConnect-ASAv type remote-access
tunnel-group AnyConnect-ASAv general-attributes
address-pool ANYCONNECT-ASAv-POOL
authentication-server-group Acceso
default-group-policy GroupPolicy_AnyConnect-ASAv
tunnel-group AnyConnect-ASAv webvpn-attributes
group-alias AnyConnect-ASAv enable
!
group-policy GroupPolicy_AnyConnect-ASAv internal
group-policy GroupPolicy_AnyConnect-ASAv attributes
wins-server none
dns-server value 10.6.0.12 10.6.7.220
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value ANYCONNECT-ASAv-ACL
url-filter FILTRO-URL
default-domain value xxxxxxxxxx.com
!
!—————————————————-!
!
tunnel-group AnyConnect-2 type remote-access
tunnel-group AnyConnect-2 general-attributes
address-pool ANYCONNECT-ASAv-POOL
authentication-server-group Acceso
default-group-policy GroupPolicy_AnyConnect-2
tunnel-group AnyConnect-2 webvpn-attributes
group-alias AnyConnect-2 enable
!
group-policy GroupPolicy_AnyConnect-2 internal
group-policy GroupPolicy_AnyConnect-2 attributes
wins-server none
dns-server value 10.6.0.12 10.6.7.220
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value ANYCONNECT-2-ACL
default-domain value xxxxxxxxxx.com
!—————————————————-!
Session Type: AnyConnect
Username : vpnuser Index : 22395
Assigned IP : x.x.x.x Public IP : x.x.x.x
Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel
License : AnyConnect Premium, AnyConnect for Mobile
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES-GCM-256 DTLS-Tunnel: (1)AES256
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA384 DTLS-Tunnel: (1)SHA1
Bytes Tx : 23214 Bytes Rx : 7960
Group Policy : GroupPolicy_AnyConnect-ASAv
Tunnel Group : AnyConnect-2
Login Time : 04:54:32 UTC Thu Sep 24 2020
Duration : 0h:02m:11s
Inactivity : 0h:00m:00s
VLAN Mapping : N/A VLAN : none
Audt Sess ID : ac10fe510577b0005f6c2688
Security Grp : none
!
?So the user can’t be on multiples Groups on the AD?
28/09/2020
It will connect and match with the first one on the list?
21/05/2021
I’m not a Cisco expert, but trying to setup our ASA 5506 with multiple groups segregating employees and vendors. I have all the AnyConnect Connection Profiles setup and separate RADIUS Server groups using same NPS servers with individual Network Policies. At the same time trying to integrate Duo for 2FA. Everything works with the exception any user part of any of the Windows VPN groups can use any of the AnyConnect Groups to authenticate and make a successful connection. I tried following this post and didn’t make a difference for me. I wouldn’t mind some help here..thanks in advance..
17/06/2021
Hi astrotekbug
I have the same problem as you
did you find a solution?
thank you
19/11/2021
Hi, @astrotekbug! Try to use Vendor-Specific parameter with value = name_of_tunnel_group instead Class with value = name_of_group_policy. More detail in https://community.cisco.com/t5/security-documents/steps-to-configure-group-lock-for-vpn-users-on-microsoft-radius/tac-p/4505478