KB ID 0001445
Problem
To be honest, the title is a little misleading, on an ASA you can specify which interface to launch a ‘ping’ from, but that’s it. I found myself in a situation today where I was working on a client firewall and I was trying to bring up a VPN tunnel, and I did not have access to any of their machines, and nor did they, (hence the reason for the VPN tunnel!)
Well we can’t use good old fashioned ping and specify an IP that’s not one of the ASA’s interfaces, but we can use TCP PING.
Note: You need ASA version 8.4(1) or above to use ‘tcp ping’.
Solution
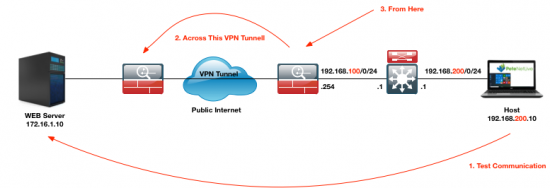
Whats TCP Ping? Well it uses TCP and sends SYN packets to the other end, and waits for the ACK packets to come back, thus testing communication.
Warning: You need to know what ports are open on the other side, the default is port 80 so if theres no web server running on the other end, it wont reply. So TCP port 445 would be good for a windows machine, or TCP 3389 (RDP) if it’s a server with RDP enabled! Or TCP 22 if it’s Linux box with SSH enabled.
How does this help me bring up my VPN tunnel? Well it sends TCP SYN traffic from and to the IP addresses you should have in your VPN cryptomap, so the tunnel will try and establish, (assuming you configured both ends correctly!)
Here I’m using TCP53 (DNS,) as I know the server is a Windows DNS Server.
Petes-ASA# ping tcp Interface: inside Target IP address: 172.16.1.10 Destination port: [80] 53 Specify source? [n]: y Source IP address: 192.168.200.10 Source port: [0] 1024 Repeat count: [5] {Enter} Timeout in seconds: [2]{Enter} Type escape sequence to abort. Sending 5 TCP SYN requests to google port 53 from 192.168.200.10 starting port 1024, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 12/14/16 ms Petes-ASA#
And my VPN is now up!
Related Articles, References, Credits, or External Links
NA

27/06/2018
A great way to bring up the tunnel is to use packet-tracer.
Ex.
packet-tracer input inside tcp 192.168.1.1 1234 1.2.3.4 1234 detailed
This will bring the tunnel up but won’t send any actual packets. You can at least verify if you get an spi for the remote subnet. If you need to verify encap/decap you need to use ping tcp
17/07/2018
Nice!
22/01/2020
Great find!
22/01/2020
Cheers Mark!