KB ID 0001422
Problem
When the ASA 5506-X appeared there was much grumbling, “This is not a replacement for the ASA 5505, I need to buy a switch as well!” and “I have six ports on the firewall I cant use” etc.
While I understand that, and if truth be told the ASA 5505, was SUPPOSED to be used in SOHO environments where an all in one device, (with PoE) was a great fit. The problem was, people started throwing them in everywhere, I’ve seen them in large businesses, and in data centres. Because it’s easier to sell a firewall that cost less than 500 quid, than it is to sell a firewall that fits the network requirements!
To ‘fix’ the problem would probably mean changing hardware, so Cisco gave us a BVI, Bridge Virtual Interface instead (with version 9.7). Well not strictly true, Cisco ASA has had BVI interfaces in ‘transparent mode‘ for some time. So on the ASA 5506-X with a default configuration, it ‘Bridges’ interfaces Ge0/2 to Ge0/8, into one interface which you can call the inside interface an give it an IP address.
Oh Great! So Just Like an ASA5505 Then? Well no sorry, I don’t like it because it needs an access-group/ACL for each bridged interface, and a NAT statement for each bridged interface. Unless you have a very simple network that can get very complicated, very quickly! Also note, the same holds true for remote management via SSH/ADSM etc.
Changes to ASA for BVI Interface
I’ll shorten the default firewall config and show you the ‘added commands’ that are used for this configuration.
! interface GigabitEthernet1/2 bridge-group 1 nameif inside_1 security-level 100 ! interface GigabitEthernet1/3 bridge-group 1 nameif inside_2 security-level 100 ! interface GigabitEthernet1/4 bridge-group 1 nameif inside_3 security-level 100 ! interface GigabitEthernet1/5 bridge-group 1 nameif inside_4 security-level 100 ! interface GigabitEthernet1/6 bridge-group 1 nameif inside_5 security-level 100 ! interface GigabitEthernet1/7 bridge-group 1 nameif inside_6 security-level 100 ! interface GigabitEthernet1/8 bridge-group 1 nameif inside_7 security-level 100 ! interface BVI1 nameif inside security-level 100 ip address 192.168.1.1 255.255.255.0 ! same-security-traffic permit inter-interface ! object network obj_any1 subnet 0.0.0.0 0.0.0.0 object network obj_any2 subnet 0.0.0.0 0.0.0.0 object network obj_any3 subnet 0.0.0.0 0.0.0.0 object network obj_any4 subnet 0.0.0.0 0.0.0.0 object network obj_any5 subnet 0.0.0.0 0.0.0.0 object network obj_any6 subnet 0.0.0.0 0.0.0.0 object network obj_any7 subnet 0.0.0.0 0.0.0.0 ! mtu outside 1500 mtu inside_1 1500 mtu inside_2 1500 mtu inside_3 1500 mtu inside_4 1500 mtu inside_5 1500 mtu inside_6 1500 mtu inside_7 1500 ! object network obj_any1 nat (inside_1,outside) dynamic interface object network obj_any2 nat (inside_2,outside) dynamic interface object network obj_any3 nat (inside_3,outside) dynamic interface object network obj_any4 nat (inside_4,outside) dynamic interface object network obj_any5 nat (inside_5,outside) dynamic interface object network obj_any6 nat (inside_6,outside) dynamic interface object network obj_any7 nat (inside_7,outside) dynamic interface ! http 192.168.1.0 255.255.255.0 inside_1 http 192.168.1.0 255.255.255.0 inside_2 http 192.168.1.0 255.255.255.0 inside_3 http 192.168.1.0 255.255.255.0 inside_4 http 192.168.1.0 255.255.255.0 inside_5 http 192.168.1.0 255.255.255.0 inside_6 http 192.168.1.0 255.255.255.0 inside_7 !
Yes I’m not making it up, that’s the added default config for a new 5506-X firewall, (post version 9.7) if you issue a configure factory-default, that’s what you will get! (Don’t panic: If you upgrade a firewall it wont add this in!)
Is That What You Wanted?
Well if you are a small business and make very little changes to the firewall then this may be fine, (if a little cumbersome to setup). But to be honest I think its pretty bobbins! So I’ll be ripping it out of every 5506-X I deploy.
ASA 5506-X Remove the BVI Interface From CLI
First you have to remove the bridge group from the physical interfaces, but first you need to remove the interface name, or it will error. Obviously connect via the console cable, or from the outside interface, (because you’re about to remove the configured inside interface, until we recreate it again).
! interface GigabitEthernet1/2 no nameif no bridge-group 1 interface GigabitEthernet1/3 no nameif no bridge-group 1 interface GigabitEthernet1/4 no nameif no bridge-group 1 interface GigabitEthernet1/5 no nameif no bridge-group 1 interface GigabitEthernet1/6 no nameif no bridge-group 1 interface GigabitEthernet1/7 no nameif no bridge-group 1 interface GigabitEthernet1/8 no nameif no bridge-group 1 !
Only now can you remove the BVI interface.
clear configure interface BVI1
WARNING: DHCPD bindings cleared on interface 'inside', address pool removed
WARNING: BVI interface 1 is in use.
Note: The BVI1 interface will now disappear from the config, (if you’re used to working on routers it’s a bit like removing a loopback interface). Now Remove the ‘defunct’ object groups that were being used for NAT.
no object network obj_any1 no object network obj_any2 no object network obj_any3 no object network obj_any4 no object network obj_any5 no object network obj_any6 no object network obj_any7
Assuming your outside Interface (GigabitEthernet0/1) is still up and connected, (by default it will be set to DHCP and also set to get its outside automatically). You would then need to configure an ‘inside’ interface (I’ll use GigabitEthernet0/2) and specify a NAT/PAT rule to allow traffic out.
!
interface GigabitEthernet1/2
nameif inside
security-level 100
ip address 192.168.1.254 255.255.255.0
!
object network OBJ-NAT-ALL
subnet 0.0.0.0 0.0.0.0
nat (inside,outside) dynamic interface
!
That gets everything up and connected, (all traffic out allowed, and all traffic in (initiated from outside) is blocked)).
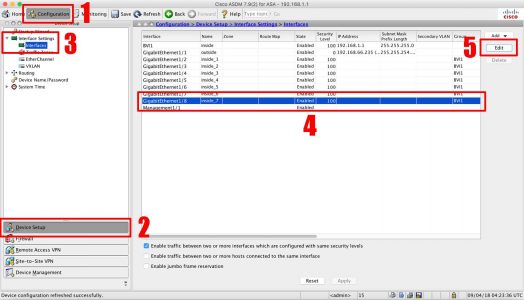
ASA 5506-X Remove the BVI Interface From CLI
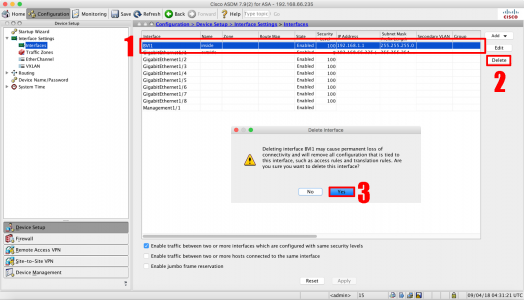
Configuration > Device Setup > Interface Settings > Interfaces > Select interface 1/8 > Edit.
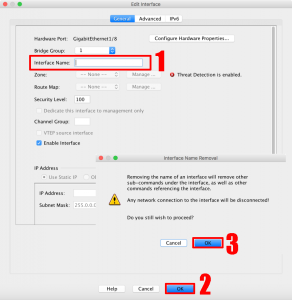
Remove the Interface name > OK >OK.
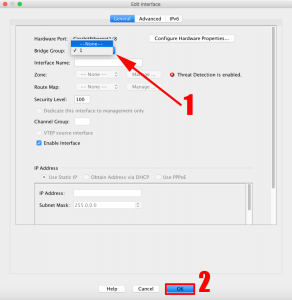
Change the Bridge Group to ‘None’ > OK.
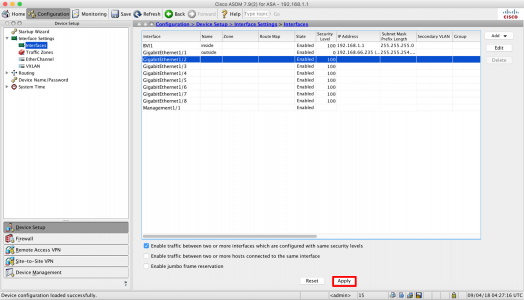
Repeat for interfaces 0/7 to 0/2 > Apply.
Select BVI1 > Delete > Yes.
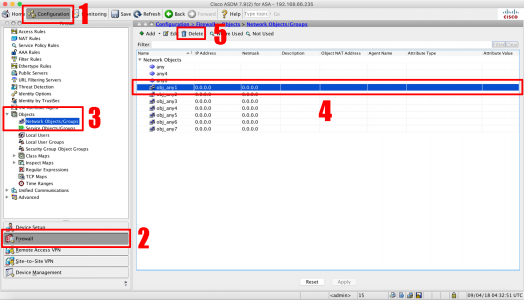
Configuration > Firewall > Objects > Network Objects/Groups > obj_any1 > Delete > Repeat for tall the other objects.
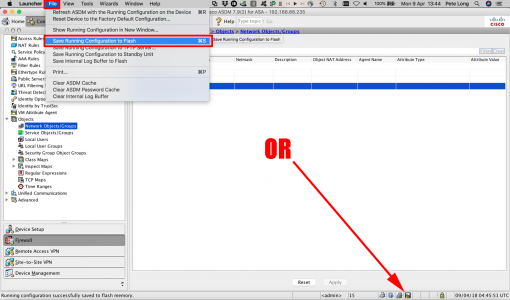
Save the changes.
Related Articles, References, Credits, or External Links
NA


13/04/2018
I wanted to let everyone know that using the BVI Group with a site to site tunnel does NOT allow management to the inside_x interface and is a known bug. The only solution is to go back to named interfaces like inside / outside to allow management via ssh or http over the site to site vpn.
Below is the bug article:
The management traffic was failing because of the following software defect – CSCve82307:
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCve82307
Steven Edelman
Network Engineer
Mindsight
Cisco Gold Partner
16/04/2018
Thanks Steven
P
04/09/2020
I’ve spent so much time trying to figure out what I did wrong on my config! Thank you very much for bringing this bug to my attention.
19/04/2018
I assume there is an error in the G1/2 security-level configuration? It should be set to 100, otherwise the levels for both inside/outside will be 0, and with the same-security-traffic permit intra-interface, it poses a security risk
24/04/2018
Yup – spotted ThanQ – page updated
18/07/2018
Pete, how would one configure just TWO ports for BVI–so that the sfr module can talk on the same subnet via a cable from Management1/1 to GigabitEthernet1/3 or whatever?
Also, I noticed that, though you mentioned that one needs to configure ACLs/access-groups for each interface using the BVI scheme, those commands don’t show up in your detailed “added commands” listing. Is that an oversight?
Thanks in advance…
18/07/2018
Hi Noel, SFR Module is a completely separate article it communicates though M0/0. If you wanted only two ports in a BVI simply omit those ports from the ones listed, (when Im removing the config and the NAT). Not having the ACLs in the post is not really an oversight, as the post is dedicated to removing the BVI altogether. If you left two ports in the BVI then you would need two access-groups each with an access-list applied to the two physical ports left in the BVI.
Pete
14/12/2018
Just what I as was looking for. Thanks.
04/06/2019
After following this, I am not able to connect with ASDM.
04/06/2019
http server enable
http 0.0.0.0 0.0.0.0 inside
Then try 🙂
Pete
05/06/2019
Thanks it works, and remember to end the com-session as well
15/08/2019
Pete,
Another thing of note that I spent some wasted time is that OSPF on the 5506x doesn’t work correctly until you remove the interfaces from the bridged configuration.
The interface and ospf will be stuck in the INIT state (at least with HP switches).
-kg
06/12/2019
Here’s a tough one for ya. Assume you maintain the BVI setup and have the bridge spanning all of the inside interfaces (2-8), and your BVI is essentially the inside VLAN, whose nameif is “inside”. Now you have DHCP servers external to this branch site (say at your data center) and you use those DHCP servers to lease IPs to the hosts internal to your branch site where the 5506 is running. You’ll obviously need to define these servers using the “dhcprelay server x.x.x.x outside” command, but then you need to enable that dhcprelay on your inside interface(s)….though the command “dhcprelay enable inside” just doesn’t work. How do you get around this issue?
06/12/2019
That is a cracking question yes! I don’t have one to hand to test, but if you execute ‘dhcprelay enable ?’ does it list all the inside interfaces separately as inside_1, inside_2, etc? Try those instead bud. (sorry I’m sat in a hotel room with no access to kit!)
Pete
19/07/2020
This is an interesting situation. You cannot enable relay for clients on BVI interface. I have single port for SERVER vlan and a BVI interface “CLIENT” with
few bridged ports CLIENT_1, CLIENT_2 and so on and here is what I get… even BVI “CLIENT” isnt listed there:
ciscoasa(config)# dhcprelay server 172.16.2.1 SERVER
ciscoasa(config)# dhcprelay enable ?
configure mode commands/options:
Available interfaces on which relay agent will accept client requests:
OUTSIDE Name of interface GigabitEthernet1/1
SERVER Name of interface GigabitEthernet1/2
ciscoasa(config)# dhcprelay enable
15/09/2021
I am in this exact situation. did you find a way to dhcprelay on bridged interfaces?