KB ID 0001375
Problem
Seen when attempting to connect to a remote machine via Remote Desktop;
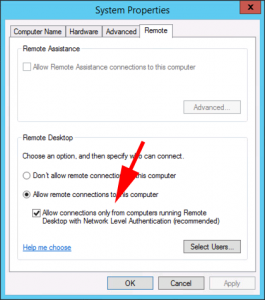
The remote computer that you are trying to connect to requires network level authentication (NLA), but your windows domain controller cannot be contacted to perform NLA. If you are an administrator on the remote computer, you can disable NLA by using the options on the remote tab of the System properties dialog box.
Also See: Windows RDP: ‘An authentication error has occurred’
Solution
Well the clue is in the error massage, RDP is enabled but it requires NLA authentication. e.g. This box has been selected.
Now, if you want NLA that’s fine, make sure your RDP client has been updated, and you, and the target, are domain authenticated, and can see a domain controller. But what if that computer is on a remote site, and you need to get on it? Or it’s in the server room downstairs and you’re lazy like me!
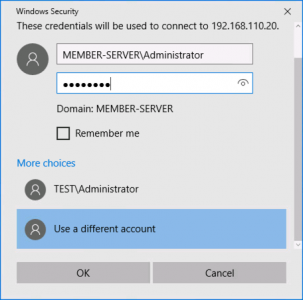
Well the simplest way to get on is to use a LOCAL account on that machine, (if you know the username and password for a LOCAL account,) like so;
WARNING/DISCLAIMER
This article was written at a time when clients may not have had up to date RDP clients that supported NLA, that’s no longer the case (If you are in a sole Windows environment, and you are updating your clients). Simply disabling NLA is NOT a solution. I’m really getting tired of people posting comments saying ‘This is a bad article’ and ‘I don’t understand’. Well how about you have 500 linux based thin clients that use RDP software that does not support NLA? Before posting a criticism please take some time to work in, and support a few different environments guys. And appreciate that you are here because you couldn’t fix it yourself, so you clicked on the link to come here, to read information that I’m providing for free, in my own time, to help you out.
Disable NLA Remotely (via Registry)
Read above disclaimer before proceeding
The drawback of this method is it usually requires a reboot (which we can do remotely, but if it’s a production server that will mean some downtime).
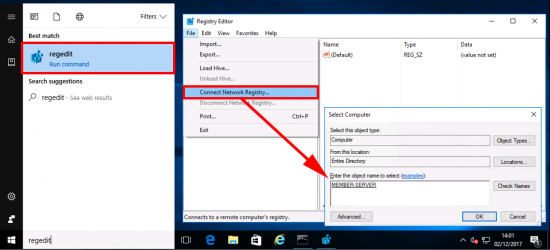
Open Regedit > File > Connect Network Registry > Search for and select your target machine > OK.
Navigate to;
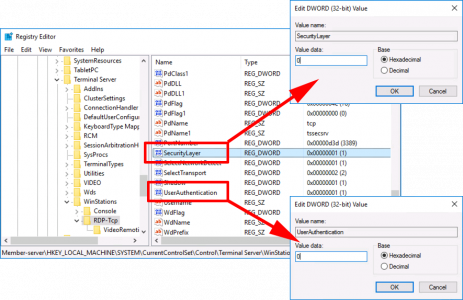
Locate the following two values, and set them to 0 (zero)
- SecurityLayer
- UserAuthentication
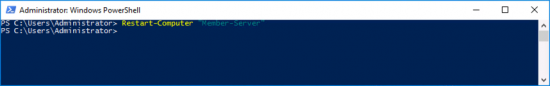
Give it a try now, but I found I needed to reboot the target first, using the ‘restart-computer’ PowerShell Commandlet.
Disable NLA Remotely (via PowerShell)
Read above disclaimer before proceeding
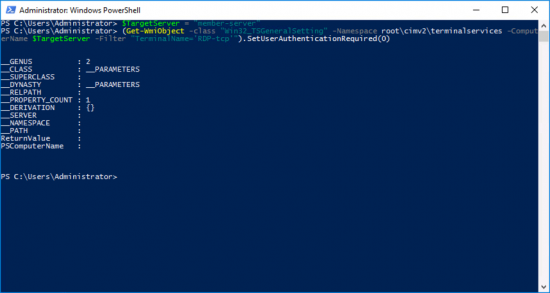
I prefer this method as it works instantly, and can be reversed just as quick! Open an administrative PowerShell command window. Execute the following two commands;
$TargetMachine = “Target-Machine-Name“
(Get-WmiObject -class “Win32_TSGeneralSetting” -Namespace root\cimv2\terminalservices -ComputerName $TargetMachine -Filter “TerminalName=’RDP-tcp'”).SetUserAuthenticationRequired(0)
Disable NLA Remote Desktop Requirement Through Group Policy
Read above disclaimer before proceeding
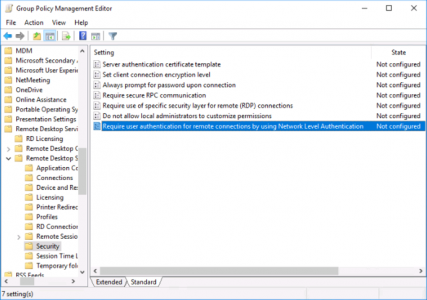
If you want to ‘blanket disable’ NLA then group policy is the way to go;
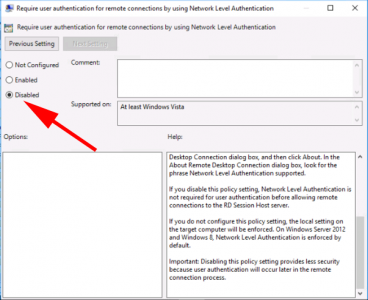
Locate the ‘Require user authentication for remote connections by using Network Level Authentication’ and set it to disabled.
Then Force a Domain Group Policy Refresh,
Related Articles, References, Credits, or External Links
NA


16/05/2019
This is terrible advice. how about understanding and solving the problem and not just disabling security features to “make the error go away”?
16/05/2019
Hi Mike,
I do say in the article;
>>Now, if you want NLA thats fine, make sure your RDP client has been updated, and you, and the target are domain authenticated, and can see a domain controller.
>>how about understanding
I do understand, and have outlined the cause of the problem.
Please bear in mind this article was written two years ago, simply everyone didn’t have post RDP 6.1 NLA capable clients, and this will have been written at the time that NLA became a requirement. Also not all RDP clients are Windows, If this causes several thousand thin clients to go down at 0900 hrs on a Monday morning, do you disable NLA or update a thousand Linux based thin Wyse/NUC/iGEL/HP clients the that have no central administration?
>>This is terrible advice.
Well you are entitled to your opinion I suppose, but some client’s simply don’t have the investment to update their client’s and have to disable features until that can be done. In the real world we can’t all stop working until we replace/update all our client machines.
Either way I welcome all feedback, even if it’s negative.
Regards
Pete
28/05/2020
Mike Crowley – please advise why this is terrible advice – this is perfectly acceptable advice and I’m saying this as I work in a very restrictive environment. What is your level of knowledge when it comes to technology?
18/04/2021
It’s awful advice. If you were having a problem with your key not working properly in your front door, would you just remove the lock and consider it “solved”? Because that’s exactly what this so called “fix” is.
19/04/2021
Read the disclaimer Nick.
01/07/2021
I’ll toss in another example, where I’m pretty sure I’ll end up having to disable NLA.
I have a VM on my personal machine. The VM is bound to my organization’s AzureAD, but the machine isn’t. I’m getting the NLA error, even though my desktop and the VM have NLA enabled, and I’m guessing it’s because the machine isn’t attached to the domain, so it can’t pass NLA.
I’m a developer, mind, not an admin, so I only vaguely get this sort of thing, but it appears that NLA is blocking my use case here. That leaves me to either only use Hyper-V’s connection interface, or disable NLA so I can use RDP properly. I hate disabling security features, but sometimes it’s the only solution.
31/05/2019
“Now, if you want NLA thats fine, make sure your RDP client has been updated, and you, and the target are domain authenticated”
So connections from a remote network, like through a Branch Office VPN, won’t work if the RDP client is not a part of your domain network?
31/05/2019
Hi Eric, Not Necessarily, just because you’re not authenticated against a ‘local’ domain controller does not mean you are not authenticated.
09/09/2020
I was looking for a solution for the same error. Disabling the NLA was not an option for me as there is a policy in place to force this behavior. In my instance, I was able remove the workstation from the domain and add it back in. This corrected the error message. Hope it helps someone else out.
01/10/2020
Matt please help me I’m in a race with a fellow colleague of mine. First to figure out how to add a computer to the domain via powershell/command prompt via smartcard and you have to use a username hint. I was super close with my line but username hint keeps getting in the way. I’m just trying to piece it together. Any guidance about username hint will be greatly appreciated! If you can write a powershell/command line that can remotely add a computer to the domain while using a smart card login and use proper password and username hint (username hint is the hardest) I will give you $20 not even kidding.
01/10/2020
Have you guys looked into using username hint for adding to domain by smart card? It’s a long stretch but is there a way to incorporate username hint into command prompt code?
16/05/2022
This is good for when you have a ec2 instance in AWS that has GPO’s that lock the machine down due to FTI requirements and it looses connection to the Domain… And your only way in is local account and RDP. So for all negative comments 😛