Default Receive Connectors KB ID 0001314
Problem
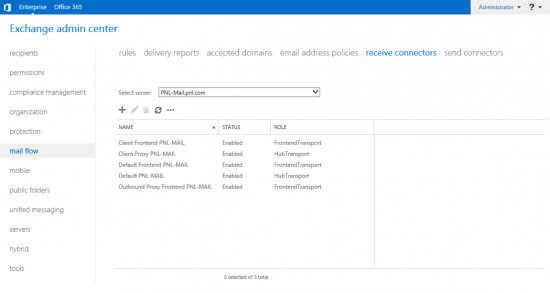
Out of the box, Exchange 2016 (&2013) has five receive connectors. Three for the frontend transport service and two for the mailbox transport service.
- Front End Transport Service: Does not alter, inspect, or queue mail. It is the first port of call for ALL mail coming into (and out of) the Exchange organisation. This service creates THREE receive connectors All are bound to 0.0.0.0 0.0.0.0, and all IPv6;
- Client frontend {Server-Name} : listens on TCP 587 (Secure SMTP). It is generally only used for POP clients that are ‘Authenticated’, so are then able to send mail though the Exchange Org.
- Default frontend {Server-Name}: Listens on TCP 25 (SMTP) and will allow Anonymous connections (by default). Note: Your incoming mail, (from the public internet,) usually comes in through this connector.
- Outbound proxy frontend {Server-name}: Confusingly this is actually a send connector and it’s only used if you have set your ‘send connector’ to proxy though one of your Exchange servers.
- Mailbox Transport Service: Does NOT receive mail from clients it, (as the name implies), routes mail from/to mailboxes from/to the frontend transport service. It is further broken down into;
- Mailbox Transport Submission Service:
- Mailbox Transport Delivery Service:
- This creates two more receive connectors;
- Client Proxy {Server-Name}: Listens on TCP 465.
- Default {Server-Name}: Listens on TCP Port 25 (or 2525).
So what if someone ‘fiddles’ with them, or you are unsure if they are setup correctly?
Solution: Default Receive Connectors
Default Receive Connectors Settings
If you just want to check the settings in the Exchange Admin Center;
- Client Frontend {Server-Name}
- General Settings;
- Name: Client Frontend {Server-name}
- Connector Status: Enable
- Protocol logging level: None
- Maximum receive message limit size (MB): 36
- Maximum hop local count: 12
- Maximum hop count: 60
- Security Settings;
- Transport Layer Security (TLS)
- Basic Authentication
- Offer basic authentication only after starting TLS
- Integrated Windows Authentication
- Permission Groups;
- Exchange Users
- Scoping;
- Remote network settings;
- ::-ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
- 0.0.0.0-255.255.255.255
- Network adaptor bindings;
- (All Available IPv6) Port 587
- (All Available IPv4) Port 587
- FQDN: {The internal FQDN of your server}
- Remote network settings;
- General Settings;
- Client Proxy {Server-Name}
- General Settings;
- Name: Client Proxy {Server-name}
- Connector Status: Enable
- Protocol logging level: None
- Maximum receive message limit size (MB): 36
- Maximum hop local count: 12
- Maximum hop count: 60
- Security Settings;
- Transport Layer Security (TLS)
- Basic Authentication
- Offer basic authentication only after starting TLS
- Integrated Windows Authentication
- Exchange Server Authentication
- Permission Groups;
- Exchange Servers
- Exchange Users
- Scoping;
- Remote network settings;
- ::-ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
- 0.0.0.0-255.255.255.255
- Network adaptor bindings;
- (All Available IPv6) Port 465
- (All Available IPv4) Port 465
- FQDN: {The internal FQDN of your server}
- Remote network settings;
- General Settings;
- Default {Server-Name}
- General Settings;
- Name: Default {Server-name}
- Connector Status: Enable
- Protocol logging level: None
- Maximum receive message limit size (MB): 36
- Maximum hop local count: 12
- Maximum hop count: 60
- Security Settings;
- Transport Layer Security (TLS)
- Basic Authentication
- Offer basic authentication only after starting TLS
- Integrated Windows Authentication
- Exchange Server Authentication
- Permission Groups;
- Exchange Servers
- Legacy Exchange Servers
- Exchange Users
- Scoping;
- Remote network settings;
- ::-ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
- 0.0.0.0-255.255.255.255
- Network adaptor bindings;
- (All Available IPv6) Port 2525
- (All Available IPv4) Port 2525
- FQDN: {The internal FQDN of your server}
- Remote network settings;
- General Settings;
- Default Frontend {Server-Name}
- General Settings;
- Name: Default Frontend {Server-name}
- Connector Status: Enable
- Protocol logging level: None
- Maximum receive message limit size (MB): 36
- Maximum hop local count: 12
- Maximum hop count: 60
- Security Settings;
- Transport Layer Security (TLS)
- Enable domain security (mutual Auth TLS)
- Basic Authentication
- Offer basic authentication only after starting TLS
- Integrated Windows Authentication
- Exchange Server Authentication
- Transport Layer Security (TLS)
- Permission Groups;
- Exchange Servers
- Legacy Exchange Servers
- Anonymous
- Scoping;
- Remote network settings;
- ::-ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
- 0.0.0.0-255.255.255.255
- Network adaptor bindings;
- (All Available IPv6) Port 25
- (All Available IPv4) Port 25
- FQDN: {The internal FQDN of your server}
- Remote network settings;
- General Settings;
- Outbound Proxy Frontend {Server-Name}
- General Settings;
- Name: Outbound Proxy Frontend {Server-name}
- Connector Status: Enable
- Protocol logging level: Verbose
- Maximum receive message limit size (MB): 36
- Maximum hop local count: 12
- Maximum hop count: 60
- Security Settings;
- Transport Layer Security (TLS)
- Enable domain security (mutual Auth TLS)
- Basic Authentication
- Offer basic authentication only after starting TLS
- Integrated Windows Authentication
- Exchange Server Authentication
- Transport Layer Security (TLS)
- Permission Groups;
- Exchange Servers
- Scoping;
- Remote network settings;
- ::-ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
- 0.0.0.0-255.255.255.255
- Network adaptor bindings;
- (All Available IPv6) Port 717
- (All Available IPv4) Port 717
- FQDN: {The internal FQDN of your server}
- Remote network settings;
- General Settings;
Recreating Your Exchange Default Receive Connectors From Scratch
Note: We are talking about the default receive connectors here, if you have created any of you own, for mail relaying from a device for example, you would need to manually recreate these. Below we are going to delete all the default connectors, and recreate them with a PowerShell Script.
Download Recreate Default Exchange Receive Connectors Scripts
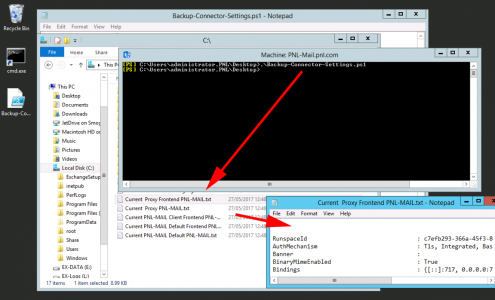
Optional: Take a backup of the default receive connectors settings to a text files. Run the ‘Backup-Connector-Settings.ps1‘ script. This will dump the settings to the root of the C: drive in ‘Current {Server-Name} {Connector-Name}.txt’ format.
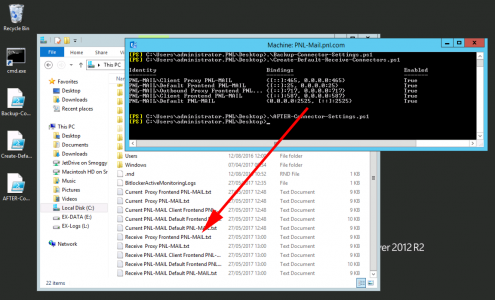
You can now delete the default receive connectors (Warning: Notice I said default receive connectors, this may or may not be all the connectors).
Recreate the Default Receive Connectors: Run the ‘Create-Default-Receive-Connectors.ps1‘ script.
Optional: You can now output the settings of the new connectors, (why? So you can compare them to your original settings.) Run the ‘AFTER-Connector-Settings.ps1’ script. This will dump the settings to the root of the C: drive in ‘Receive {Server-Name} {Connector-Name}.txt’ format.
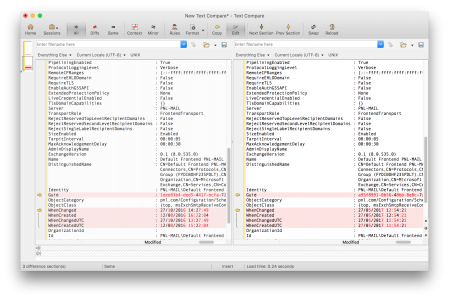
You can now compare differences, the only differences are usually the creation date, and the GUID.
Related Articles, References, Credits, or External Links
NA


15/02/2018
Just awesome, thanks you for this
16/05/2018
If I changed my URI to use external name (webmail.domain.com) should I change FQDN on default and client front end connector to use external name?
18/05/2018
As long as that name can be resolved internally and externally, (to the internal/external ip as approriate) 🙂
P
01/10/2018
Thanks a lot Pete.
You saved our life.
02/10/2018
Np Thanks for the feedback!
06/12/2018
Under Default (Server Name) the ports are listed as 2525 for both IPv4 and IPv6 – is this accurate? I’ve only seen it as port 25 (SMTP).
07/12/2018
2525 is correct 🙂
24/05/2019
Many thank’s
04/11/2019
Thank you!
Is there a powershell to “re-bind” the default front end to 25? Our EXC2016 CU9 update failed, the server rolled back. Brought the server back online. However receiving externally is the only thing not working. Our emails being held at our Sonicwall screener for unable to relay
thanks again!
06/11/2019
The script posted does that?
01/07/2020
Thank you! I’d managed to delete all my receive connectors when troubleshooting a hybrid mail configuration.
I was tearing my hair out for a couple of days as to why I was continually getting “451 4.7.0 Temporary server error. Please try again later. PRX5” errors.
I stumbled on your article when looking to see why I was seeing errors on port 2525 – using your script recreated the connectors and everything kicked into life.
Thanks
13/10/2020
It appears that the “Default Frontend ” keeps port 25 open and doesn’t require authentication to send mail to local users. Isn’t this a bit of a security concern? Am I missing something or is it required to be this way for some other reason?
I’m by no means an Exchange pro, but shouldn’t SSL/TLS and authentication be required to send mail? I trust no one.
13/10/2020
*Default Frontend ServerName
14/10/2020
SMTP isn’t secure? What gave you that idea? where do you think most of your spam comes from?
22/10/2020
Thanks for this! Do you know which Receive Connector Exchange Online uses to connect to in a Hybrid Environment? Is it the “Default Frontend ServerName” connector, and would we have to check the “Partners” box beneath the Permissons group to get it working?
Or does on-prem Exchange in the background use the same automagical connector creation during the hybrid config like Exchange online did ? 🙂
27/11/2020
Thanks a lot, accidently I deleted default connectors, but bcz of you now I can configure back
26/02/2022
I have recreated some of the receive connectors via the Web GUI but this did not work.
So I just deleted all of them but the non standar ones.
Your PS script just saved my b… Thank you very much for this!
20/08/2023
Your scripts saved me a lot of time. Thanks!!
06/03/2025
Thumbs up kind Sir. I have had a crippled On Prem Exchange 2016 server operating in a hybrid environment. It has always served purpose of adding new users to AD and then the Azure AD Connector would populate O365 with the new users. Last year sometime, stopped sending and receiving and I just never got to looking at it because I host all mailboxes in M365. I had reason to get it back to functional recently and I would like to thank you for the scripts as I am able to send and receive once again. Also helps with connector validation in O365 Admin center. Thanks again.
11/03/2025
Happy to help – ThanQ