KB ID 0001310
Problem
In Part One we deployed our offline Root CA Server, now we are going to deploy a ‘Certificate Revocation Location’ server.
Solution
Before you start:
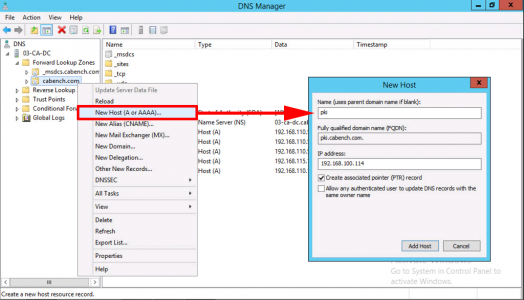
Create a DNS record for ‘pki‘ that points to the IP address, that you will have the CRL web server hosted on.
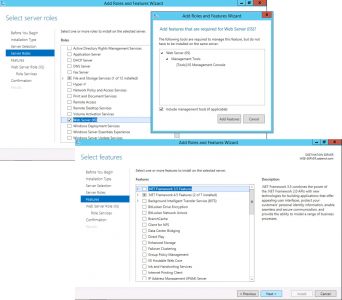
I’m installing my CRL server on a separate web server because thats good practice. Starting with a domain joined member server, launch Server Manager > Manage > Add Roles and Features.
Role Based > Next > Select the Local Server > Next.
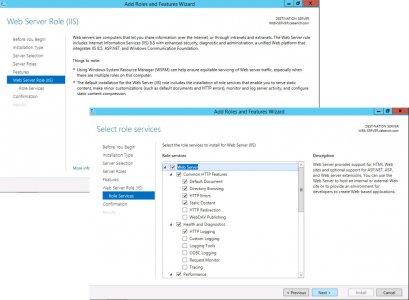
Select Web Server IIS > Add Features > Next > Next.
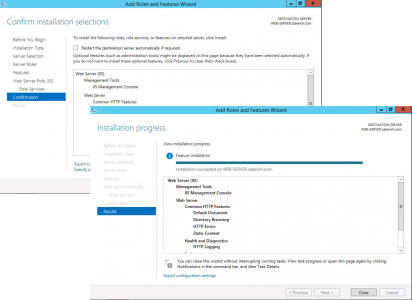
Next > No additional features are required > Next.
Next > Install > Close.
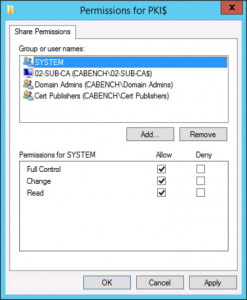
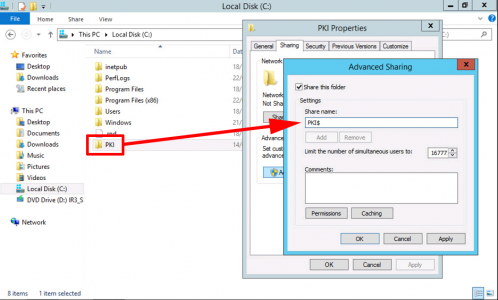
Create a Folder called PKI on the Root of your web server and share it as PKI$ (The dollar denotes hidden share).
Set the share permissions as follows;
- SYSTEM: Full Control
- Domain Admins: Full control
- Cert Publishers: Change
- Servers That Will Publish CRLs: Full Control
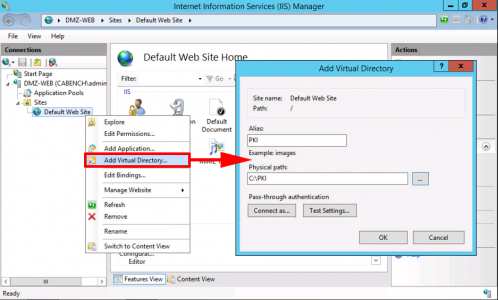
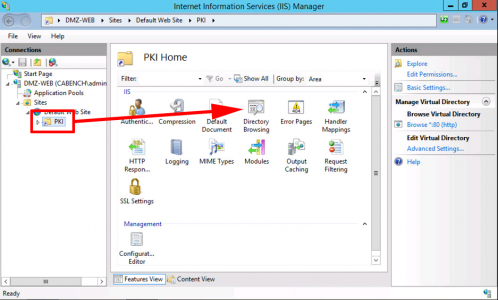
Launch Internet Information Services (IIS) > Server-name > Sites > Default Web Site > Add Virtual Directory.
- Alias: PKI
- Physical Path: C:\PKI
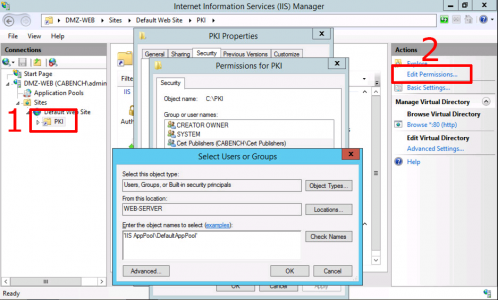
Select your new PKI directory > Edit Permissions.
- Cert Publishers: Modify.
- DefaultAppPool: Read and Execute.
Note: You cannot browse to DefaultAppPool > Change the source to local computer-name > type in the username ‘IIS AppPool\DefaultAppPool’.
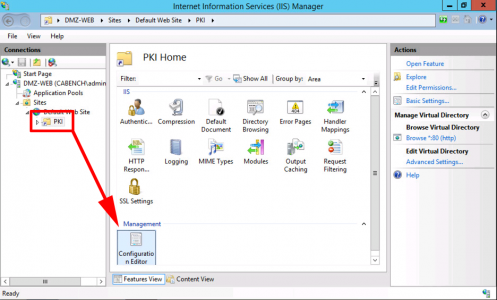
For your PKI Virtual Directory select ‘Configuration Editor’.
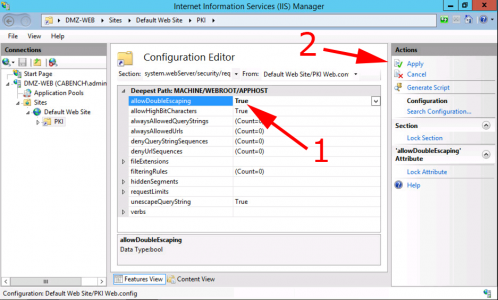
System.webServer > Security > requestFiltering > allowDoubleEscaping > Change to ‘True’ > Apply.
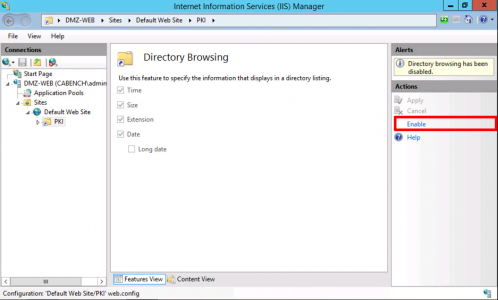
Now select ‘Directory Browsing’.
Enable.
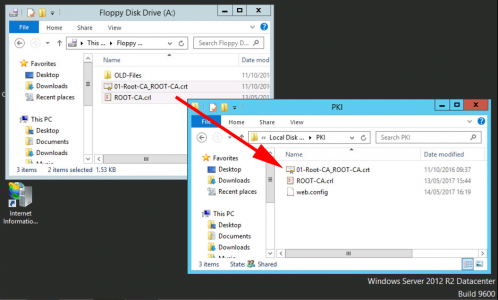
At this point I copy in the .crl file you exported from your Offline Root CA. (I also copy in the RootCA certificate, so I know where I can get a copy!)
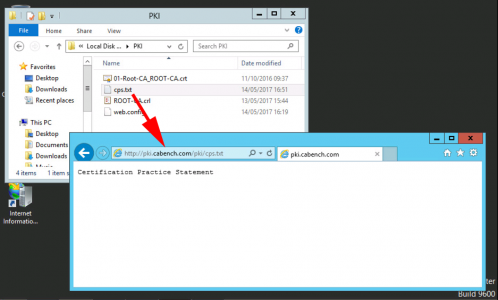
When you setup your CA Servers in the CAPolicy.inf file theres a section of the ‘Legal Policy Statement’ and the URL I used points to this server as well, (it was http://pki.cabench.com/pki/cps.txt). So create the cps.txt file in the same directory. To decide what text will go in the file, read RFC 7382.
The next most logical step depends on whether you are building a two tier, or three tier PKI environment. If it’s a three tier, then you are going to deploy your Intermediate Sub CA server next. If it’s a two tier then you are going to deploy your Issuing CA next.
Microsoft PKI Planning and Deploying Certificate Services Part 3
Related Articles, References, Credits, or External Links
NA

10/05/2019
Just to clarify, you have a domain joined server running IIS with the PKI share in your DMZ? How do you handle all the AD traffic between that server and the DCs? Or did I miss something? Very possible I missed something 🙂
This is how I understand it to be:
root-ca (offline,non-domain,inside)
inter-sub-ca [t3](online,domain,inside)
issue-sub-ca [t2 or t3] (online,domain,inside)
web (online,[non?]domain,dmz)
10/05/2019
I don’t think I mention DMZs do I? Anyway, I’ve deployed CRLs in a DMZ before, you only need to publish to a file share, so the web server does not need to be a domain member in that instance, you just need the file sharing open so you can publish the deltas and the CRLS.
10/05/2019
I saw DMZ-WEB in one of the screen captures,on that server is the PKI share with “domain admins” permissions. I guess that led me to believe it was a domain joined IIS box in the DMZ.
Sorry man, this stuff makes my brain hurt.
28/11/2020
Is there any reason the CRL server needs to be a Windows box? I feel like a tiny Linux box in our DMZ would be a superior solution.
03/12/2020
I don’t see why not, as long as you can push updates to it.