KB ID 0001298
Problem
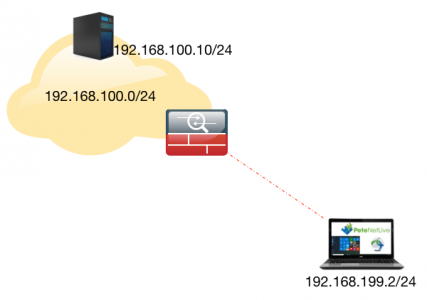
Packet tracer is a great tool, I wrote about it in the ‘Prove It’s Not the Firewall‘ article a while ago. A couple of months ago I was having a discussion with a colleague about packet tracing a remote VPN client to check connectivity, he said at the time, “It will behave differently if the IP you use is already connected”. I never really thought about it until today, when I was troubleshooting a clients AnyConnect they they had ‘hair pinned‘ to another site.
So after I had finished I tested the theory on the bench to discover he was correct.
Solution
Results When The IP is NOT IN USE
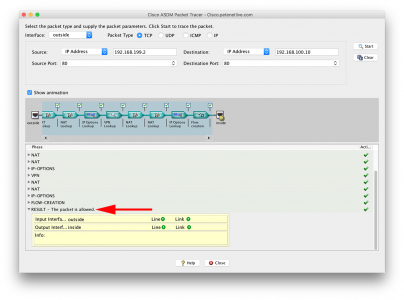
I prefer to work at commend line, so if I packet-trace the above connection (using normal http port 80 for example) This is what I get;
Petes-ASA# packet-tracer input outside tcp 192.168.199.2 www 192.168.100.10 w$
Phase: 1
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 192.168.100.0 255.255.255.0 inside
Phase: 2
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (inside,outside) source static any any destination static OBJ-ANYCONNECT-SUBNET OBJ-ANYCONNECT-SUBNET no-proxy-arp route-lookup
Additional Information:
NAT divert to egress interface inside
Untranslate 192.168.100.10/80 to 192.168.100.10/80
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group inbound in interface outside
access-list inbound extended permit tcp any object Internal_HTTP_Server eq www
Additional Information:
Phase: 4
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection decrement-ttl
service-policy global_policy global
Additional Information:
Phase: 5
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (inside,outside) source static any any destination static OBJ-ANYCONNECT-SUBNET OBJ-ANYCONNECT-SUBNET no-proxy-arp route-lookup
Additional Information:
Static translate 192.168.199.2/80 to 192.168.199.2/80
Phase: 6
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 8
Type: VPN
Subtype: ipsec-tunnel-flow
Result: ALLOW
Config:
Additional Information:
Phase: 9
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
nat (inside,outside) source static any any destination static OBJ-ANYCONNECT-SUBNET OBJ-ANYCONNECT-SUBNET no-proxy-arp route-lookup
Additional Information:
Phase: 10
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 11
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 12
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 5786108, packet dispatched to next module
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: allow
Petes-ASA#If you really must use the ASDM here’s what it looks like in there;
Results When The IP is IN USE
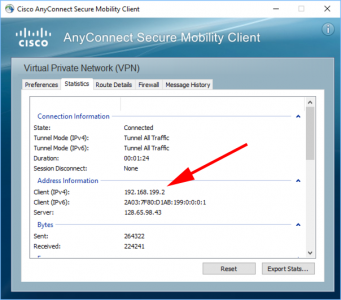
So, if I connect my remote client, and it gets an IP, (for simplicities sake the same IP we used above), like so;
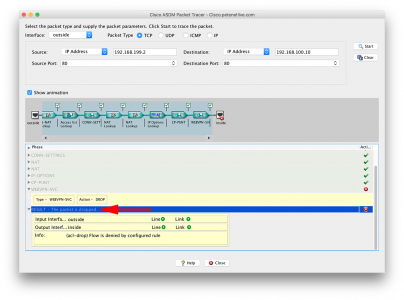
Then run the exact same test, here’s the result;
Petes-ASA# packet-tracer input outside tcp 192.168.199.2 www 192.168.100.10 www Phase: 1 Type: ROUTE-LOOKUP Subtype: input Result: ALLOW Config: Additional Information: in 192.168.100.0 255.255.255.0 inside Phase: 2 Type: UN-NAT Subtype: static Result: ALLOW Config: nat (inside,outside) source static any any destination static OBJ-ANYCONNECT-SUBNET OBJ-ANYCONNECT-SUBNET no-proxy-arp route-lookup Additional Information: NAT divert to egress interface inside Untranslate 192.168.100.10/80 to 192.168.100.10/80 Phase: 3 Type: ACCESS-LIST Subtype: log Result: ALLOW Config: access-group inbound in interface outside access-list inbound extended permit tcp any object Internal_HTTP_Server eq www Additional Information: Phase: 4 Type: CONN-SETTINGS Subtype: Result: ALLOW Config: class-map class-default match any policy-map global_policy class class-default set connection decrement-ttl service-policy global_policy global Additional Information: Phase: 5 Type: NAT Subtype: Result: ALLOW Config: nat (inside,outside) source static any any destination static OBJ-ANYCONNECT-SUBNET OBJ-ANYCONNECT-SUBNET no-proxy-arp route-lookup Additional Information: Static translate 192.168.199.2/80 to 192.168.199.2/80 Phase: 6 Type: NAT Subtype: per-session Result: ALLOW Config: Additional Information: Phase: 7 Type: IP-OPTIONS Subtype: Result: ALLOW Config: Additional Information: Phase: 8 Type: CP-PUNT Subtype: Result: ALLOW Config: Additional Information: Phase: 9 Type: WEBVPN-SVC Subtype: in Result: DROP Config: Additional Information: Result: input-interface: outside input-status: up input-line-status: up output-interface: inside output-status: up output-line-status: up Action: drop Drop-reason: (acl-drop) Flow is denied by configured rule Petes-ASA#
Again, the same thing in the ASDM;
So the moral of the story is, if you are testing, make sure the IP you are using for the remote client is NOT in use.
How do I know which AnyConnect IPs are in use? Simple run the ‘show vpn-sessiondb anyconnect‘ command like so;
Petes-ASA# show vpn-sessiondb anyconnect Session Type: AnyConnect Username : pete.long Index : 293 Assigned IP : 192.168.199.2 Public IP : 123.123.123.123 Assigned IPv6: 2a03:7f80:d1ab:199::1 Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel License : AnyConnect Essentials Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES128 DTLS-Tunnel: (1)AES128 Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA1 DTLS-Tunnel: (1)SHA1 Bytes Tx : 4948010 Bytes Rx : 555588 Group Policy : PNL-GP-ANYCONNECT-ACCESS Tunnel Group : PNL-TG-ANYCONNECT-ACCESS Login Time : 14:07:00 GMT/BST Wed Apr 5 2017 Duration : 0h:34m:48s Inactivity : 0h:00m:00s NAC Result : Unknown VLAN Mapping : N/A VLAN : none Petes-ASA#
Related Articles, References, Credits, or External Links
Packet-Tracer Fails Subtype: rpf-check Result: DROP
Cisco ASA ASDM – Packet Tracer Wont Work
Cisco ASA (acl-drop) Flow is Denied by Configured Rule

05/04/2017
Great article !! You may want to add a note about the outside ACL. In most cases, Anyconnect traffic is not added in the outside ACL as it is bypassed using the “sysopt connection permit-vpn” command. Packet-tracer just assumes that the packet comes in on the outside interface and does cannot differentiate it as VPN traffic. What’s going to happen then is that the packet-tracer will show a drop on Phase 3 (ACL check). For this to work, the admin may need to temporarily add the Anyconnect traffic to be allowed on the the outside-in ACL.
05/04/2017
Good Catch!
Regards,
Pete
02/08/2017
Is there a way to test AnyConnect without disabling the “sysopt connection permit-vpn” command? I have a replacement ASA I am testing before installation and wanted to make sure AnyConnect will work. Given, I assume AnyConnect should function properly as the live ASA allows VPN connections via AnyConnect (I have simply exported the old config to the new device with few modifications).
03/08/2017
Hi Bryan – Not sure what you’re trying to do VPN will bypass ACL traffic by default, and thats a hidden command, so even if you restore from an older OS it will still be enabled. All disabling it means, is you have to put in extra ACLs to allow the VPN traffic?
Pete
24/12/2019
I believe i could see the Outside-in acl for the VPN pool segment in my org and still the packet tracer shows the packet drop in the WEBVPN-SVC
24/12/2019
The ‘inbound’ acl should not be affecting you, you will see a WBVPN-SVC drop if you don’t use an IP address for an ‘already established’ VPN session.
P
05/11/2020
Nice one.
30/04/2024
Thanks for this, helped me out today