KB ID 0001273
Problem
If you have remote users who connect via VPN, and a policy that forces them to change their password periodically, this can result in them getting locked out without the ability to change their password (externally).
If your Cisco ASA is using LDAP to authenticate your users, then you can use your remote AnyConnect VPN solution to let them reset their passwords remotely.
Solution
Standard LDAP runs over TCP port 389, to allow the ASA to reset the password for the users, it needs to be connected via LDAPS ((TCP Port 636). Your AD server needs to be able to authenticate via LDAPS, by default it will not. I’ve already covered how to set that up in another post see the following article.
Windows Server 2012 – Enable LDAPS
So, assuming your AD server(s) that the Cisco ASA is authenticating against is already setup, you need to ensure that your AAA Settings for LDAP is set to use port 636.
Enable LDAPS via Command Line
On my test network I only have one LDAP server in my LDAP AAA group, you may need to repeat this procedure for each one in yours.
Petes-ASA(config)# aaa-server TEST-LDAP-SERVER (inside) host 192.168.110.10 Petes-ASA(config-aaa-server-host)# server-port 636
Enable LDAPS From within the ASDM
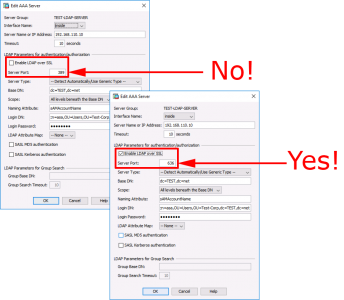
Log into the ADSM > Configuration > Device Management > Users/AAA > Select the LDAP Server Group > Select the Server > Edit > Enable LDAP over SSL > Server Port = 636.
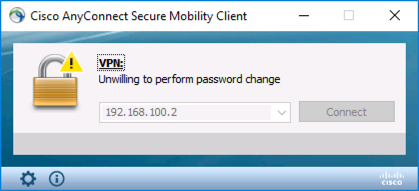
Note: If you attempt to reset a user password without LDAPS, then you will see the following error;
Unwilling to perform password change
Next you need to edit the AnyConnect connection profile to allow password resets. Or the tunnel-group if you work at command line.
Allow Password Reset via Command Line
Petes-ASA(config)# tunnel-group ANYCONNECT-PROFILE general-attributes
Petes-ASA(config-tunnel-general)# password-management password-expire-in-days 3
Allow Password Reset via ASDM
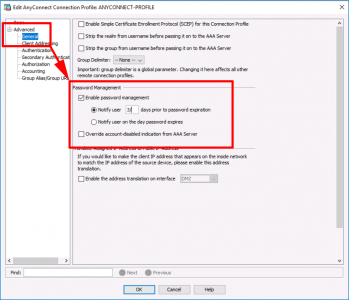
Connect to the ADSM > Configuration > Remote Access VPN > Network Client remote Access > AnyConnect Connection Profile > Select the one for AnyConnect > Edit > Advanced > General > Password Management > Enable Password Management > Select to notify user the amount of days before his/her password expires > OK > Apply > File > Save running configuration to flash.
Now your users have the ability to reset their password remotely as they are about to expire, and when they have expired.
If you want to test with a particular user you can set his password to ‘expired’ using the following procedure;
Reset an AD Users Password Expiry Date
Related Articles, References, Credits, or External Links
NA


21/02/2019
Just wanted to say a huge thanks for this article : https://www.petenetlive.com/KB/Article/0001273
Very helpful
21/02/2019
ThanQ
P
20/05/2019
I agree. This article is super helpful in explaining it in simple language on how to do this. This setup will save us a lot of time spent helping users reset their passwords, and we don’t need to pay for extra software to get this option.
12/02/2021
Excelente articulo..
Para complementar el tema de cli
Petes-ASA(config)# aaa-server TEST-LDAP-SERVER (inside) host 192.168.110.10
Petes-ASA(config-aaa-server-host)#ldap-over-ssl enable
No olvidar hacer el test