KB ID 0001261
Problem
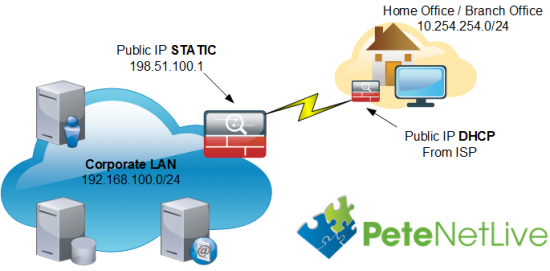
EZVPN is a technology that lets you form an ISAKMP/IPSEC VPN tunnel from a site with a dynamically assigned IP (EZVPN Client,) back to a device with a static IP (EZVPN Server).
I’ve called this EZVPN revisited, because this is a technology I’ve talked about before. So why am I here again? Well back then I used the ASDM. If you do that now, you need to go in and mess about with things to get it to work properly. Last week a client was asking me about buying a 5505 for his home, and putting a VPN into his place of work. Obviously he did not have a static IP at home, which was why I suggested EZVPN.
So it’s time to ‘Man Up’ and get to grips with the CLI. In the example below my corporate LAN is behind a Cisco ASA 5515-X, and my ‘Home Office’ is behind a Cisco ASA 5506-X, (you can use a 5508-X as well, or an old 5505).
Solution
So How does EZVPN Work? Well there’s no separate/special technology, it’s a good old fashioned Client IPSEC VPN. The one we used to use the OLD IPSEC VPN client for, (yes the one that went end of life – in 2011!)
But instead of using a piece of software to supply the username/password and the group/pre-shared-key, you configure a hardware device to supply those details. This enables the hardware device to bring up a software client VPN session. There are two methods of doing this, Client Mode and Network Extension Mode (NEM).
- Client Mode: Works exactly like the VPN client software, and leases an IP address from a pool of IP addresses supplied by the ASA, (or a DHCP server).
- Network Extension Mode: This works like a ‘proper’ site to site VPN, insofar as, all the IP addresses on the client/remote site can be addressed from the main site.
I’m going to use Network Extension Mode for this example, I’m also going to enable ‘Split tunnelling’ so that only VPN traffic goes over the VPN.
Remote EZVPN Client WARNING
The client that ‘dials in’ cannot be running any other VPN solution. In fact it can’t even have IKE policies defined, (even if they are not in use).
Configure the EZVPN Server
The bulk of the work is on the main site ASA.
! crypto ikev1 policy 65535 authentication pre-share encryption 3des hash sha group 2 lifetime 86400 ! crypto ipsec ikev1 transform-set TS-IPSEC-VPN esp-3des esp-sha-hmac ! access-list SPLIT-TUNNEL standard permit 192.168.100.0 255.255.255.0 ! group-policy IPSEC-VPN internal group-policy IPSEC-VPN attributes password-storage enable nem enable vpn-tunnel-protocol ikev1 split-tunnel-policy tunnelspecified split-tunnel-network-list value SPLIT-TUNNEL vpn-simultaneous-logins 3 ! tunnel-group IPSEC-VPN type remote-access tunnel-group IPSEC-VPN general-attributes default-group-policy IPSEC-VPN authentication-server-group LOCAL tunnel-group IPSEC-VPN ipsec-attributes ikev1 pre-shared-key Cisco123456 ! crypto dynamic-map DYNAMIC-CRYPTO-MAP 65535 set ikev1 transform-set TS-IPSEC-VPN ! crypto map CRYPTO-MAP 65535 ipsec-isakmp dynamic DYNAMIC-CRYPTO-MAP ! crypto map CRYPTO-MAP interface outside ! crypto ikev1 enable outside ! object network OBJ-EZVPN-SUBNET subnet 10.254.254.0 255.255.255.0 ! nat (inside,outside) source static any any destination static OBJ-EZVPN-SUBNET OBJ-EZVPN-SUBNET no-proxy-arp route-lookup ! username EZVPNSite1 password P@ssword123 !
Points to Note:
- I’m using 3DES and SHA1 for Phase 1 (ISAKMP,) and phase 2 (IPSEC).
- The Network behind my main site ASA is 192.168.100.0/24.
- The Network behind my remote site ASA is 10.254.254.0/24.
- I’ve enabled split tunnelling.
- My interfaces are called inside and outside, yours might be different!
- Crypto Map Warning: If you already have a crypto map applied to the outside interface use the name of the existing one (i.e NOT CRYPTO-MAP), or your exiting VPN’s will stop working! Issue a ‘show run crypto map‘ command to check.
- I have not enabled PFS. (If I had it would have been in the crypto map).
Configure the EZVPN Client (Remote Site)
The remote site(s) are easy.
! vpnclient server 198.100.51.1 vpnclient mode network-extension-mode vpnclient nem-st-autoconnect vpnclient vpngroup IPSEC-VPN password Cisco123456 vpnclient username EZVPNSite1 password P@ssword123 vpnclient enable !
Adding Additional EZVPN Sites
To add another site in Client Mode you would simply add another username and password, on the EZVPN server. With Network Extension Mode then you would add an object and NAT exemption on the main site, then setup a new username and password for that site like so;
New Site EZVPN Server Config
! object network OBJ-EZVPN-SUBNET-2 subnet 10.254.254.0 255.255.255.0 ! nat (inside,outside) source static any any destination static OBJ-EZVPN-SUBNET-2 OBJ-EZVPN-SUBNET-2 no-proxy-arp route-lookup ! username EZVPNSite2 password P@ssword456 !
New Site EZVPN Client Config
You just need the new username and password;
! vpnclient server 198.100.51.1 vpnclient mode network-extension-mode vpnclient nem-st-autoconnect vpnclient vpngroup IPSEC-VPN password Cisco123456 vpnclient username EZVPNSite2 password P@ssword456 vpnclient enable !
Related Articles, References, Credits, or External Links
NA

09/01/2017
Really nicely written article. Thank you very much.
In the Points to Note section;
“The Network behind my eemote site ASA is 192.168.100.0/24”
I’m sure you meant to type:
“The Network behind my remote site ASA is 10.254.254.0/24”
09/01/2017
ThanQ – Well spotted – Article updated.
Pete
14/07/2017
How do you define the interesting traffic to be addressed through the VPN tunnel?
17/07/2017
For EZVPN, all traffic is interesting traffic, it behaves like the old IPSEC VPN client software.
P
29/11/2018
Adding new VPN client to ASA, do need to reboot ASA?
03/12/2018
No definitely not 🙂
05/01/2020
Hello There,
Thank you for the article. Really helpful.
I’m trying to implement the same but I have multiple VLANS in both main as well as in the remote sites which needs communication.
Can you please guide on how to set this up also what should I range should I use for split tunneling?
Thank you
06/01/2020
Split Tunnelled VLANS are just the VLAN’s behind the ASA at the main site (EZVPN Server).
As for having multiple remove VLANS, this does not matter as long as you are in NEM mode.
P
21/03/2019
Thanks 😀
30/03/2020
One of the best resource on Ezvpn, Superbly written.
30/03/2020
ThanQ
07/07/2020
Thanks for the article. Have you find a “workaround” to use multiple ports on the ASA-5506-X as part of the “Inside” interface. I know it is a code limitation supporting NAT on multiple BVI interfaces.
Regards,
Oscar Perez
07/07/2020
Hi Oscar – Ive written an article about it. https://www.petenetlive.com/KB/Article/0001422
P
04/09/2020
Is there support for EZVPN as a client on any device that Cisco has not gone EOS/EOL? Are there any third party devices that can support EZVPN (i.e. Sonicwall, etc.)?
08/09/2020
No, if you need to use Sonicwall etc. then you need to do this https://www.petenetlive.com/KB/Article/0001683
07/10/2021
This is the best article about ezvpn out there!! thank you so much for your post.
I just have one question, how the NEM mode routing works? Static IP or maybe the remote site subnets are inserted in server side and vice versa?
Thank you again!
12/10/2021
It’s supposed that all server side routing ends up back at the firewall (EZVPN Server), if that’s not the case then you need to manually route it there 🙂
21/10/2021
Is it possible to use this same scenario but not NAT traffic across the tunnel? In particular, if the headend firewall were non-Cisco, would I need to NAT the EZ VPN client traffic?
22/10/2021
If the head end device is not Cisco then you can’t use EZVPN?