KB ID 0001239
Problem
Here I’m dealing with AnyConnect VPNs, but the principles are exactly the same for both remote IPSEC and L2TP VPNs. You connect to your VPN and can no longer browse the internet from your remote location.
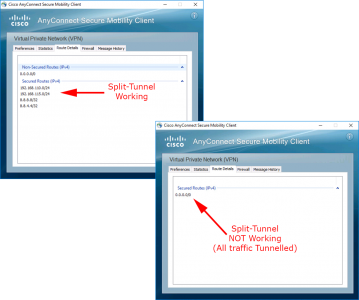
You can confirm that split-tunnelling is working or not by connecting with your VPN client and looking at the routing information.
Solution
Before proceeding are you sure Split-Tunnelling has ever been setup and configured? See the following article.
Cisco ASA – Enable Split Tunnel for IPSEC / SSLVPN / AnyConnect Clients
For Split Tunnelling to work you need;
- An Access Control List, allowing the networks/IP’s that are protected by your ASA, that you need to access over the VPN.
- A Group-policy that references the access-list above.
- A Tunnel Group that references the Group-policy above.
The lines get a bit blurred if you are in the ASDM, in there the terminology, is access control list, group-policy, and connection profile.
Troubleshoot Split Tunnel From CLI
Connect and authenticate an AnyConnect client. Then on the firewall run the following command.
Petes-ASA# show vpn-sessiondb anyconnect
Session Type: AnyConnect
Username : petelong Index : 4
Assigned IP : 172.16.1.1 Public IP : 192.168.100.77
Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel
License : AnyConnect Premium
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES256 DTLS-Tunnel: (1)AES256
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA1 DTLS-Tunnel: (1)SHA1
Bytes Tx : 14128 Bytes Rx : 12305
Group Policy : GroupPolicy_ANYCONNECT-PROFILE
Tunnel Group : ANYCONNECT-PROFILE
Login Time : 12:49:31 GMT/BST Mon Sep 19 2016
Duration : 0h:01m:03s
Inactivity : 0h:00m:00s
VLAN Mapping : N/A VLAN : none
Audt Sess ID : c0a86e010000400057dfd0cb
Security Grp : none
Petes-ASA#From the output above, we know the name of the Group Policy and the Tunnel Group. The fact we can see BOTH is an indication that the tunnel group is setup correctly, but it does no harm to check.
Petes-ASA# show run tunnel-group ANYCONNECT-PROFILE
tunnel-group ANYCONNECT-PROFILE type remote-access
tunnel-group ANYCONNECT-PROFILE general-attributes
address-pool ANYCONNECT-POOL
default-group-policy GroupPolicy_ANYCONNECT-PROFILE
tunnel-group ANYCONNECT-PROFILE webvpn-attributes
group-alias ANYCONNECT-PROFILE enable
Petes-ASA#
Then check that that group-policy has enabled split tunnelling, and referenced the correct access control list.
Petes-ASA# show run group-policy GroupPolicy_ANYCONNECT-PROFILE
group-policy GroupPolicy_ANYCONNECT-PROFILE internal
group-policy GroupPolicy_ANYCONNECT-PROFILE attributes
wins-server none
dns-server value 8.8.8.8 8.8.4.4
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value SPLIT-TUNNEL
default-domain value petenetlive.com
webvpn
anyconnect profiles value testbench type user
Petes-ASA#
Finally take the ACL name (SPLIT-TUNNEL) and make sure that’s OK.
Petes-ASA# show run access-list SPLIT-TUNNEL
access-list SPLIT-TUNNEL standard permit 192.168.110.0 255.255.255.0
access-list SPLIT-TUNNEL standard permit 192.168.115.0 255.255.255.0
Troubleshoot Split Tunnel From ASDM
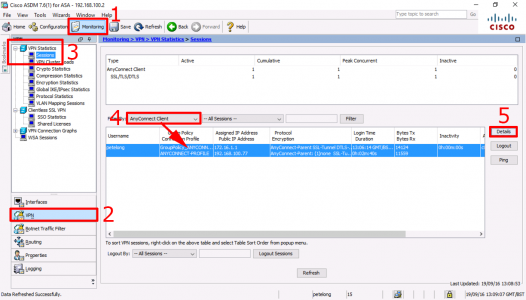
As above connect a remote AnyConnect client > Monitoring > VPN > VPN Statistics > Sessions > AnyConnect Client > Select your connected client > Details.
Note: The info we actually want, is shown on this screen, but let’s look at the session anyway.
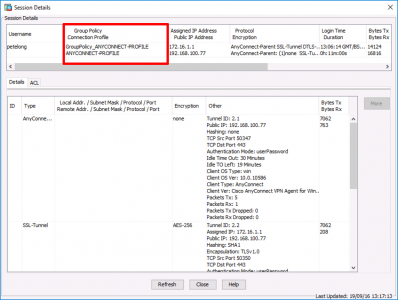
Now you can see the Group Policy and Connection Profile thats been applied to this user.
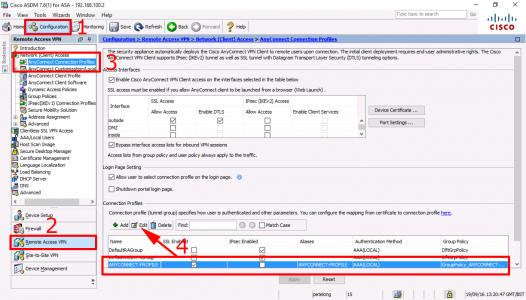
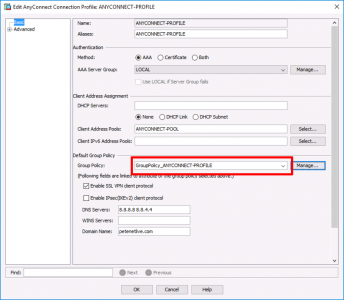
Configuration > Remote Access VPN > AnyConnect Connection Profiles > Select the one shown above > Edit.
Check the Group-Policy is correct, (Note: You can manage it directly from here, but I will take the long way round).
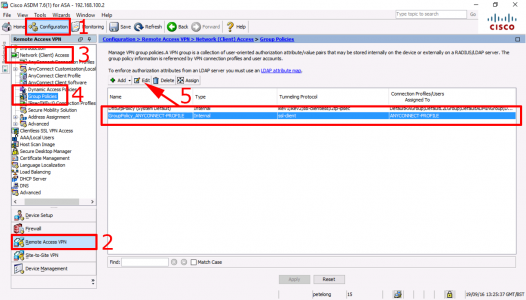
Configuration > Remote Access VPN > Network (Client Access) > Group Policies > Select the one shown above > Edit.
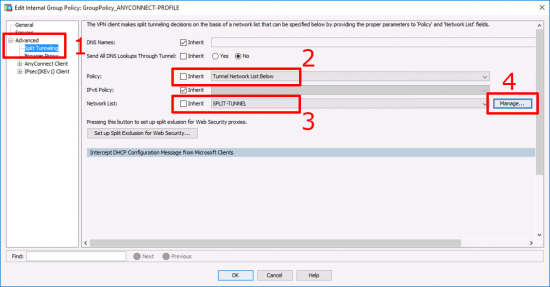
Advanced > Split Tunneling > Ensure Policy is ‘untucked’ and set to ‘Tunnel Network List Below’ > Ensure Network list is ‘untucked’ and set to the name of your split tunnel ACL > Manage.
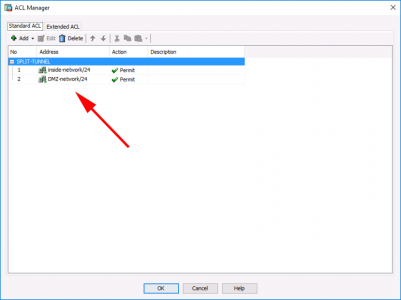
Make sure the network(s) or IP addresses behind your ASA, that you want to access over the VPN, are listed.
Related Articles, References, Credits, or External Links
Cisco ASA – Enable Split Tunnel for IPSEC / SSLVPN / AnyConnect Clients
Cisco ASA – Remote VPN Client Internet Access

10/04/2019
Many thanks for this. It solved a problem for me nice and quickly.
17/07/2019
Thank you. I’d missed the policy bit but now working. Good clear instructions, much appreciated.
Stuart.
05/09/2019
Thanks for these instructions! Excellent detail, and they allowed me to get my users working properly again. I created my own Hell by changing DNS settings, which disabled the split-tunnel settings.
07/11/2019
I don’t have the “advanced” option but a “more options” instead that does not contain the split tunnel option. I’m running ASDM 7.8. Any idea why that would be ?
08/11/2019
I’ve just checked on an ASDM v7.10 and it’s there? The version shown in the article is 7.6?
P