KB ID 0001211
Problem
Note: This is not an exhaustive list, but it’s what I use when securing Remote Desktop Services, (Terminal Services) servers. Some of these settings are ONLY for Server 2012 R2 and later. If you have any settings you think are omitted, please comment below.
Solution
User Access To RDS
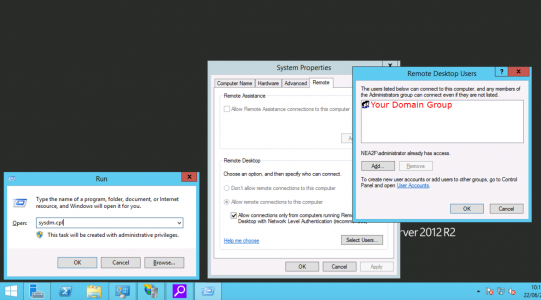
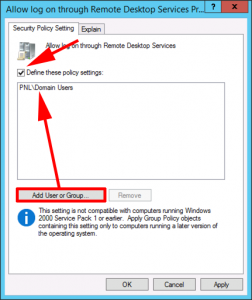
If you want to create a Domain security group for RDS users than please do so. BE AWARE the ‘Remote Desktop Users’ group you see in Active Directory Users and Computers, (in the built in OU) is for access to Domain Controllers Only! In all the examples I use below I am allowing access to ‘Domain Users’.
If you log onto the RDS server itself > Windows Key+R > systm.cpl > Remote > Remote Desktop > Select Users > Add as appropriate.
Errors
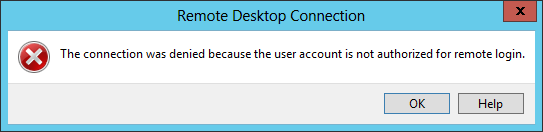
I had a situation where everyone worked apart from one user, who got this error;
The connection was denied because the user account is not authorised for remote login.
This user was a member of domain users, and all the normal boxes were ticked, I had to add ‘Domain Users’ AGAIN via Group Policy before the problem went away?
GPO Location
Group Policy
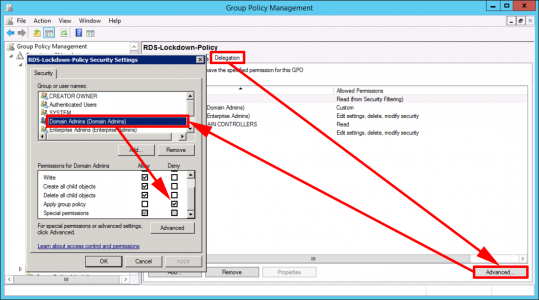
Stop Group Policy Applying to Domain Administrators
Restricting users is fine but if you create a GPO and link it to your RDS servers, and enable ‘loopback processing’, then the policy will apply to the domain administrator, and members of the domain administrators group. To stop that happening, you need to ‘Deny: Apply group policy‘ to the users/groups that you DON’T want the policy being applied to;
Computer Policies
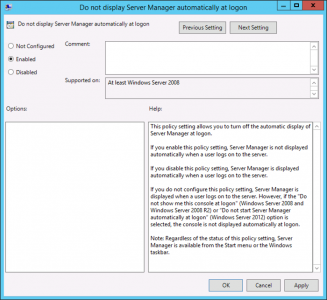
Stop Server Manager Launching at Logon
(Note: to remove the Server Manager shortcut from the task bar see below)
GPO Location
Setting: Enabled
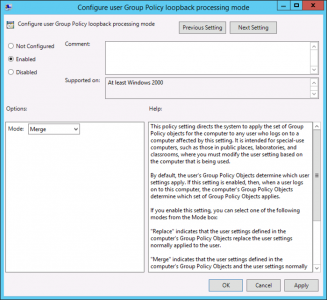
Configure Group Policy Loopback Processing
The reason you do this is, a lot of the policies you want to apply are ‘user policies‘ and the group policy you link to your RDS servers is linked to a domain/site/OU that contains Computer objects. If you enable loopback processing you can configure user settings in the same policy and they get applied to users logging onto those computers the policy is linked to. This is perfect for Remote Desktop Services.
GPO Location
Setting: Enabled
User Policies
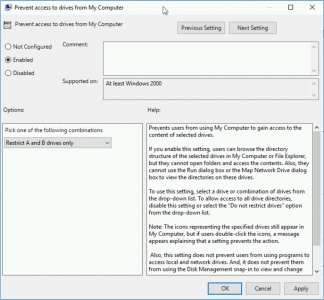
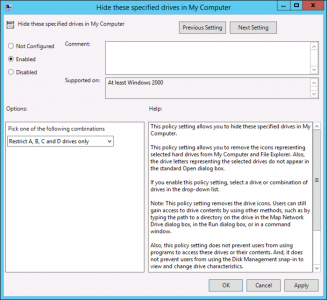
Prevent/Hide Access to Drives
I hide access to the drives that are on the RDS server itself, and leave the rest because most people still have mapped drives and network drives they want access to.
GPO Location
Setting: Enabled
GPO Location (Server 2012 and older)
Setting: Enabled
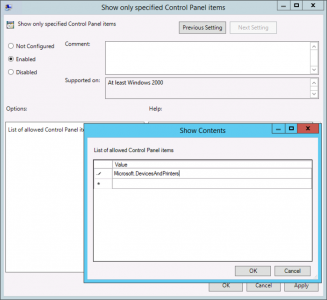
Prevent/Hide Access to Control Applications
There is a policy that blocks access to applications you specify, but I prefer to block ALL applications except the ones I specify, and I only ever allow access to Devices and Printers.
GPO Location
Setting: Enabled
Setting: Microsoft.DevicesAndPrinters
Note: For a list of all applications, search for ‘Canonical names for Control Panel Items’.
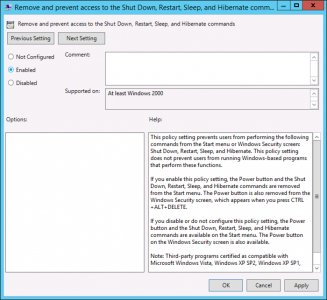
Remove Shut Down / Restart, Sleep and Hibernate
For obvious reasons you don’t want your users to have the ability to shut down the server.
GPO Location
Setting: Enabled
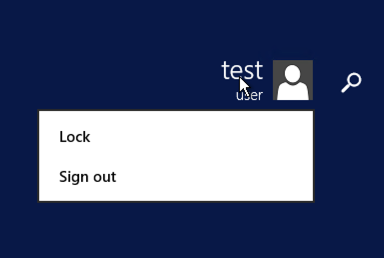
Now your users should just have’ lock’ and ‘sign out’.
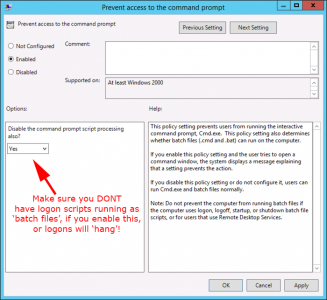
Remove Use Of Command Line (CMD)
I say ‘remove use’, because with this policy enabled, even if a user manages to get a command window to run, they still can’t execute any commands.
GPO Location
Setting: Enabled
Setting: Disable the command prompt script processing also: Yes. (Read the warning!)
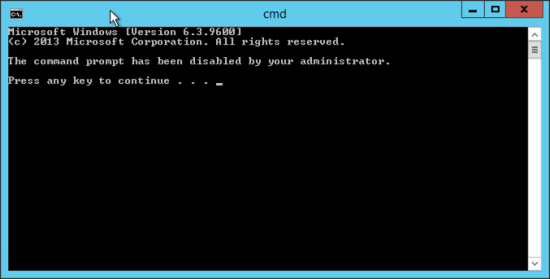
So if a user does manage to get a command window open, this is what they will see;
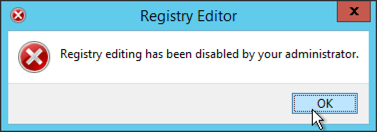
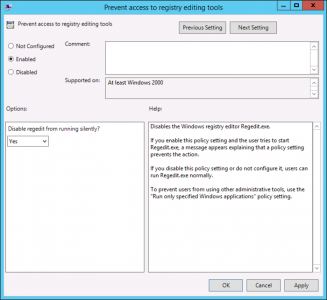
Prevent Access to Registry Editing Tools (Regedit)
For obvious reasons, I don’t trust most techs in the registry, never mind ‘users’.
GPO Location
Setting: Enabled
Setting: Disable Regedit from Running Silently: Yes. (Make sure you dont have any reg commands in your login scripts!)
If a user attempts to run the registry editing tools this is what they will see;
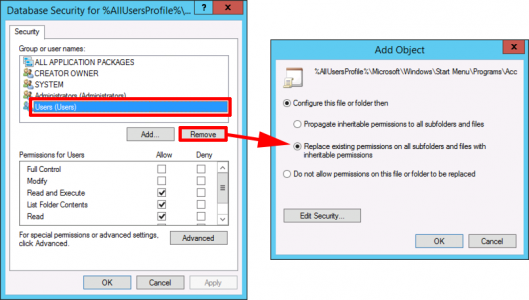
Remove Server Manager From the Task Bar
To do this you need to change permissions on the shortcut files.
GPO Location
Right click File system ‘Add File’, Change the permissions on the following files BY REMOVING USERS,
File: %AllUsersProfile%\Microsoft\Windows\Start Menu\Programs\Administrative Tools\Server Manager.lnk
The users/groups remaining should be;
- Administrators
- Creator
- SYSTEM
- All Application Packages (may not be present)
Note: Sometimes you need to test this with a new ‘fresh user’. This is because these shortcuts are copied into the user profile, the first time a user logs on.
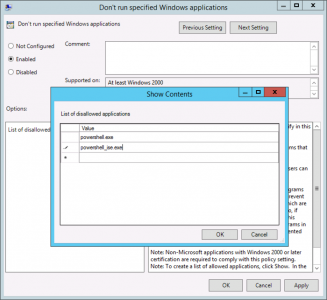
Prevent Access to PowerShell
This is much more difficult that it needs to be! I prevent access to the powershell.exe and powershell_ise.exe files.
GPO Location
Setting: Enabled
Setting: powershell.exe and powershell_ise.exe
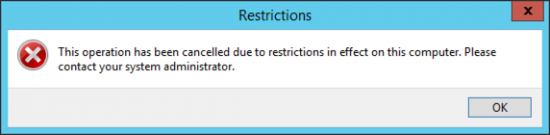
Now if you user attempts to run PowerShell this is what they will see;
RDS Removing Administrative Tools From Start Menu
I do this by creating a custom start menu for my users, see the following article;
RDS – Custom Start Menu (Remove Administrative Tools)
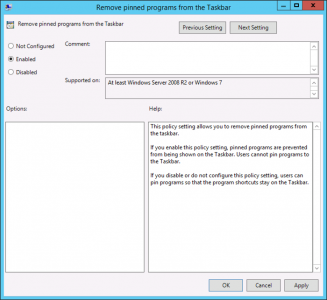
Remove ‘Pinned’ Applications / Programs from the Taskbar
This is a bit of a ‘shotgun approach’, because it removes ALL [pinned items and stops users pinning items (which you might not want). I use it because all solutions Ive found to remove the PowerShell shortcut from the Taskbar don’t seem to work on Server 2012R2
GPO Location
Setting: Enabled
 This is what your users will see;
This is what your users will see;
Related Articles, References, Credits, or External Links
NA


07/07/2016
Thank you! Excellent article, it’s very helpful!
09/07/2016
Much appreciated! It helped a lot!
27/08/2017
Thanks a lot pete your hints regarding start menu heled me a lot !
31/08/2017
no worries 🙂
05/04/2018
Thanks Pete, you clearly put a lot of effort into your content and it’s much appreciated 🙂
06/04/2018
Thanks for the feedback!
23/05/2018
Very impressive article Pete. Thanks for taking time to write this down.
09/06/2018
under “Prevent/Hide Access to Drives”
By default, it has A,B,C & D.
how can you expand it to additional drives such as “E” or “F”?
11/06/2018
Change it to “Restrict all drives”
Pete
21/08/2018
goooooooooooooooood
14/10/2019
Doesn’t exist any longer. Worth to correct it.
User Configuration > Administrative Templates > Windows Components > Windows Explorer >
14/10/2019
Good Catch, Cheers Mark.
Post updated with the new policy location.
Pete
02/04/2020
Hi,
Wanted to ask, our users have laptops which they rdp to their workstations. Laptops are on the domain and they use VPN software and some use remote gateway on personal computers.
I would like to stop them from shutting down their office workstations by accident as some forget they are in a rdp session. So here I am looking into disabling the shutdown/restart option in the start menu only as a computer configuration and not user configuration. As you know this has to be a computer configuration because if it was applied as a user configuration the shutdown button will also be removed from their domain laptop too.
I have read example that this can be done as a local policy but that would be a pain on all workstations and GPO is preferred method.
02/04/2020
No it’s a user policy the only way to get round it, is to create a ‘user policy’ link it to the ‘computer OU’, then enable ‘loopback processing’ in the computer policy section of that same GPO, and set it to remove the shutdowns command, for the particular policy do a search above for hardening RDS servers, Ive written that policy up in that article.
P
02/04/2020
Thanks! I’ll look into it further and your article.