Track failed logon KB ID 0001209
Problem
If a large number of failed logon attempts occur within a certain period of time, it could be an indication of a security threat, which is why it is important that organisations have a proactive means of auditing and monitoring whenever this happens. There are a number of ways you can perform this audit, one of which is using the native tools. Here, we will take you through the steps so that you know how to perform this audit when required:
Note: This will get you to the machine or user that’s presenting the problem. It will not tell you where on that machine the misconfiguration has occurred. I suggest that once you’ve located the offending machine, you look in Services to see what accounts the services are running under (services.msc), and enable local auditing on that machine to help you get further towards the root cause.
Please don’t message me to say “Well, I’ve found the machine, now what?”
Solution : Track Failed Logon
- Run gpmc.msc to Configure Group Policy Audit Settings
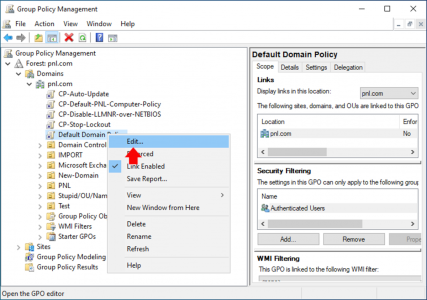
- Edit domain’s Default Domain Policy in the Group Policy Management Editor.
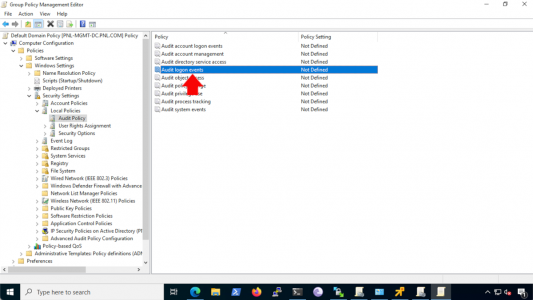
- Expand Computer Configuration>Windows Settings>Security Settings > Local Policies > Audit Policy and double-click ‘Audit logon events’.
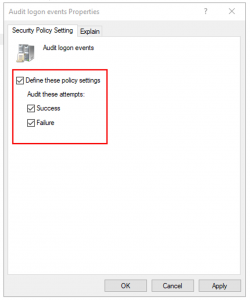
- In the Audit logon event properties, select the Security Policy Setting tab and select Success.
- Open command prompt and run the command gpupdate/force to update Group Policy.
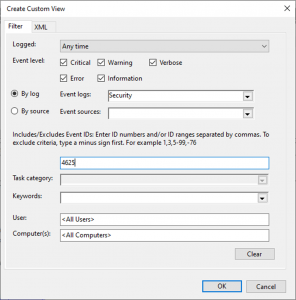
- To know about the failed logon events, filter the Security Event Log for Event ID 4625.
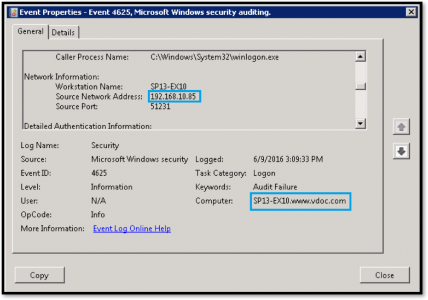
- Double-click on any event to see details of the source from where the failed logon attempts were made.
Conclusion
Regularly auditing failed logon attempts through monitoring your Security event logs is necessary for ensuring security and stability of Active Directory environments. Native tools allow you to view these Security event logs but it is perhaps not the most pro-active or user-friendly method. Many organizations find that it makes more sense to deploy an automated solution, like LepideAuditor Suite – Active Directory that provides in depth reporting and real time alerting.

24/06/2020
Hmm… This gives you the origin of the logon attempt but does not give you the source In my case, I know what machine the logon attempts are coming from but I cannot determine the source of those logon attempts.
There are no NTServices running with those credentials. No tasks in Task Scheduler. SQLAgent doesn’t run on this machine so it isn’t a MSSQLSRVR task. I’ve scoured the registry for the account name in question and nothing turns up; I have not yet searched by SID. I deleted the user’s profile from the machine via System Properties | User Profiles. And yet these failed logon attempts persist and I can find nothing in the Event Log that provides me any additional detail other than the machine where these attempts originate from.
07/08/2020
On my case the network information doesn’t show up on the event viewer
22/09/2021
Hello Andrew, did you ever find the source of the failed logon attempts?
I am troubleshooting a similar issue, I know the source system of the failed network logon attempts, but can find nothing on the source system that’s using the bad credentials.
13/01/2022
Me three! Spent 3 hours trying to kill it.
25/05/2023
What if you have an account getting locked out every 30-60 seconds and the DC doesn’t show any failed login attempts? Auditing is turned on, and I’ve never had a problem tracking down failed logins before.
29/04/2025
This doesn’t show me what application is causing the failed logons.
I already know what workstation the fialed logons are coming from, I need to know what application or where exactly the failed logons are coming from on the sepcific computer.
02/05/2025
Thats correct it does not, I suggestyou look in services to see what user account s have been configured to run services, and then selectively remove software untillthe problem, ceases, or enable LOCAL auditing for success/failiure inthe local policy of that machine.