KB ID 0001156
Problem
Carrying on from PART 1
Solution
Add > Create Before.
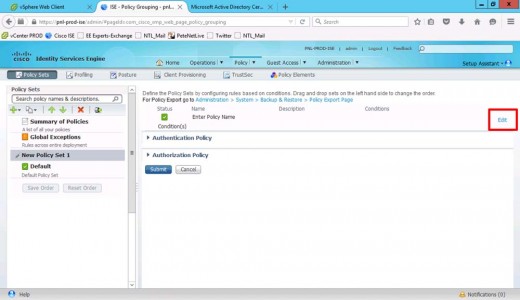
Edit the Policy
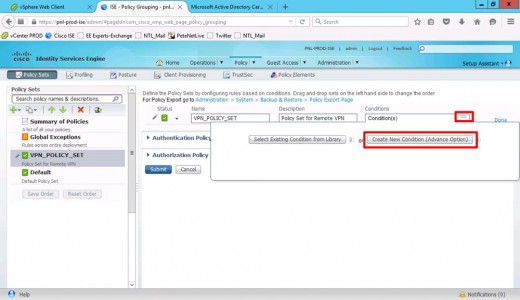
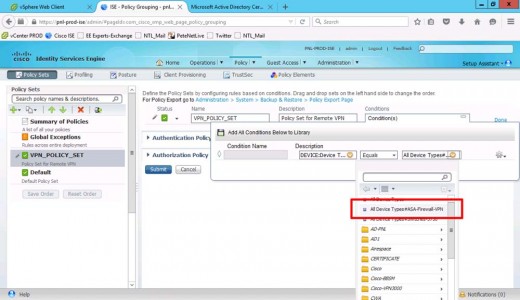
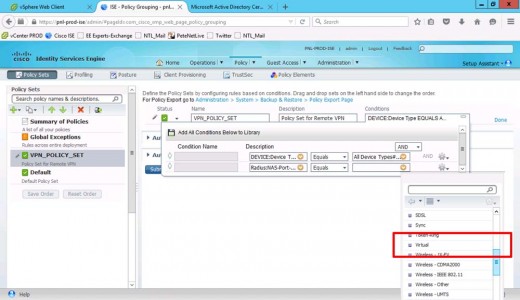
Giv the policy set a name and description > Create a new condition.
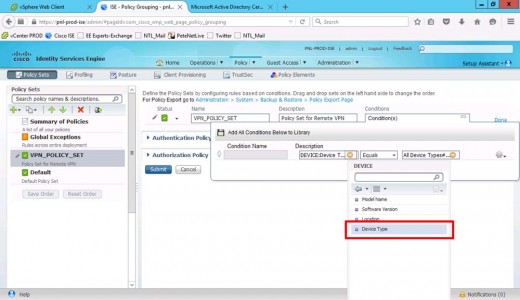
Set Description to Device Type.
Equals > All Device Types (The Device Group You Created Above).
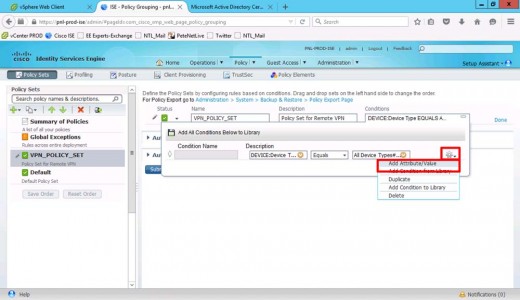
Add attribute value.
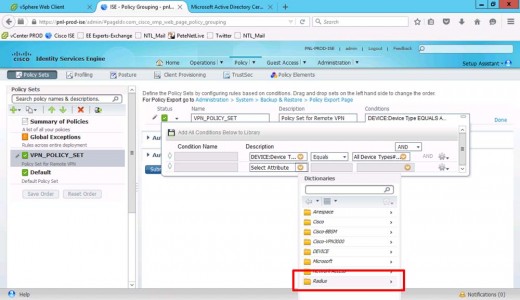
Set Description to RADIUS.
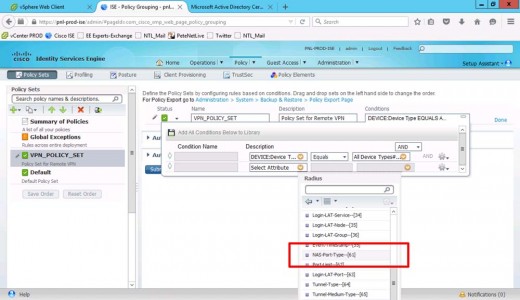
NAS-Port-Type-[61].
Equals > Virtual.
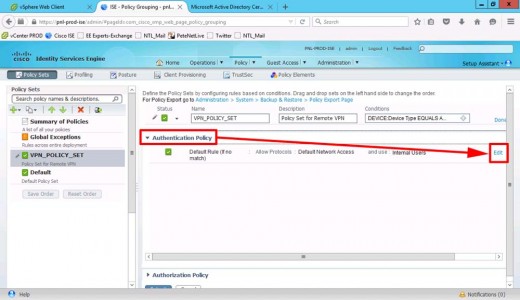
Edit the Authentication Policy.
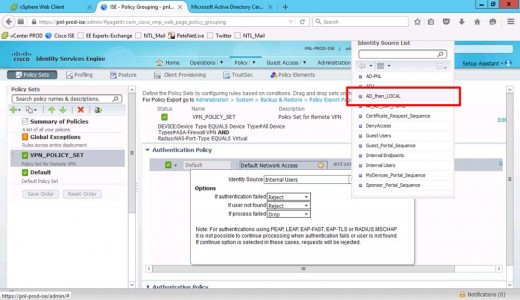
Change the identity source to the the identity source sequence you created above.
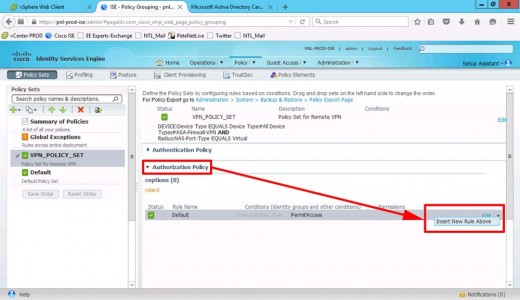
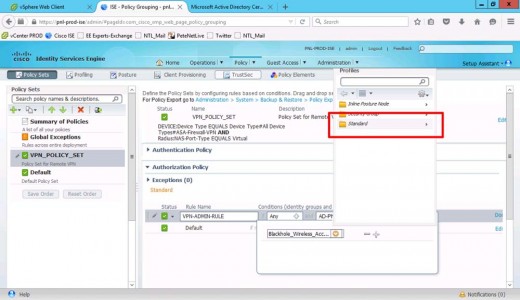
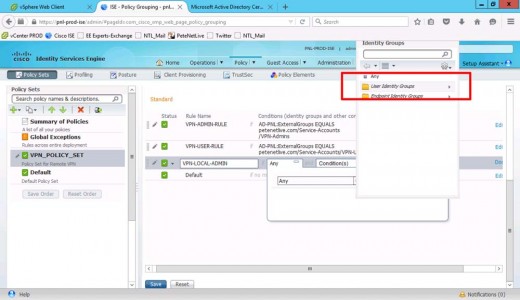
Authorisation Policy > Insert New Rule Above.
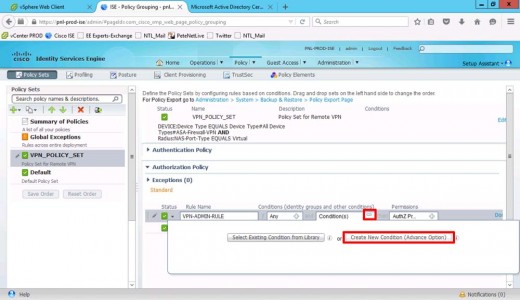
Give it a Name i.e. VPN-ADMIN-RULE > Create New Condition.
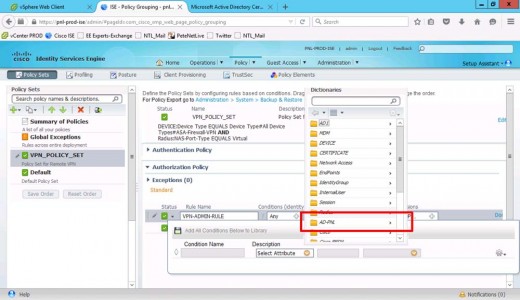
Set Description to your Active Directory.
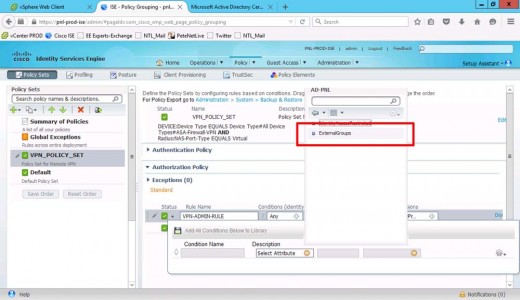
External Groups.
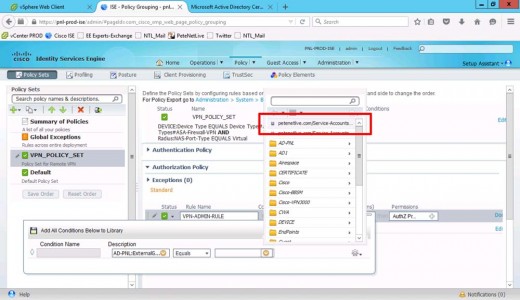
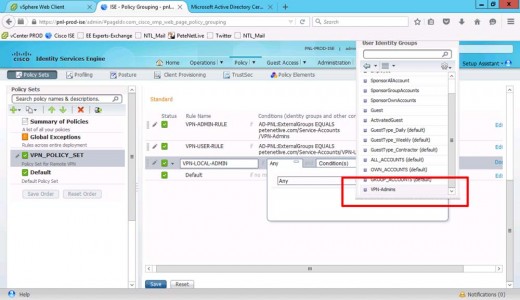
Select your AD group (VPN-Admins).
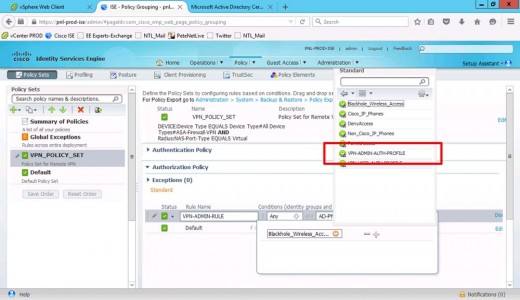
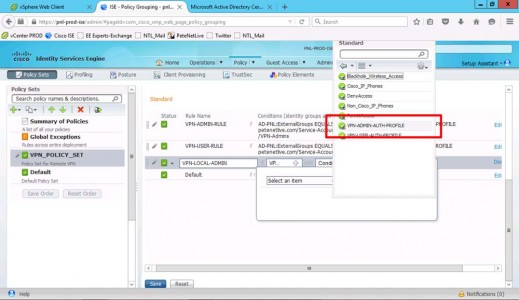
Set Permissions to Standard.
Select your VPN-Admins authorisation profile.
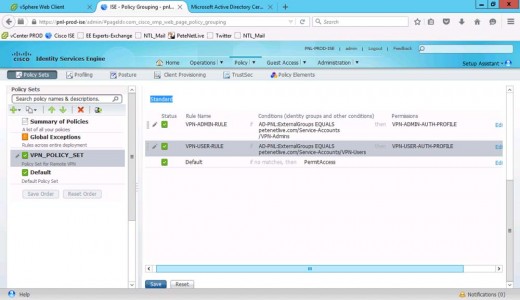
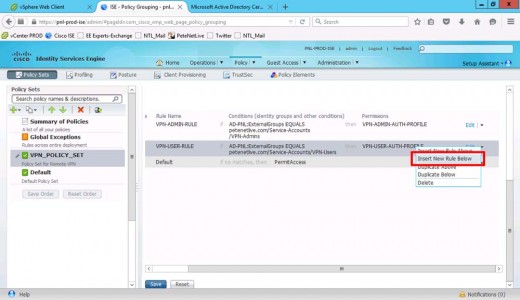
Add another rule (directly below) of your VPN-Users and set this one to use the user profile.
Add a further rule (below that) for your LOCAL admin in the ISE database.
Set User Identity Groups to VPN-Admins.
Note: this is the LOCAL group in ISE, NOT the domain security group.
Again use the admin authorisation profile.
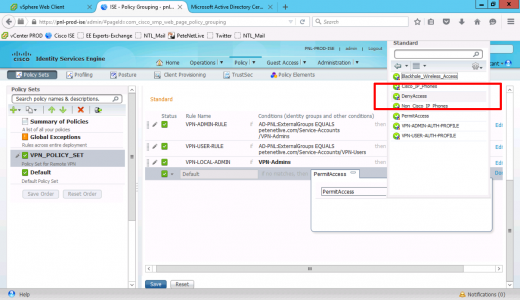
Finally you need to change the ‘Default’ rule to ‘Deny Access’, (or they will just hit the default allow and get in anyway!)
Now you can test.
Related Articles, References, Credits, or External Links
AnyConnect Group Authentication With Cisco ISE and Downloadable ACLs (Part 1)

14/03/2020
Great article!
Thanks!
26/10/2020
Great Article, Is it possible to add Azure MFA using cloud based MFA server or alike to Any Connect VPN tunnel group for vpn-admins and vpn-users.I do see few articles that have attached Any connect to azure MFA, but i need authorization to be finally Cisco ISE based.
26/10/2020
Azure MFA is easy enough, But I dont know about combing that with ISE Im afraid.