KB ID 0001111
Note: This is for Cisco ASA 5500, 5500-x, and Cisco Firepower devices running ASA Code.
This comes up on forums a lot, some applications and most phone systems require a ‘LOT’ of ports to be open. Normally thats fine you just give the internal IP a static public IP and open the ports. But what if you don’t have a spare public IP? I’ve already covered port forwarding before.
Cisco PIX / ASA Port Forwarding
Until version 8.4 you couldn’t even do this, you needed to create a translation for each port! Note: There is a bug in versions 9.0 and 9.1 that can stop this working, so check your OS with a ‘Show Ver’ command to be sure.
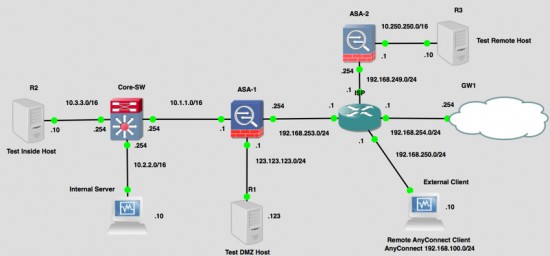
As I said this come up a lot on forums so when it asked on EE the other day, I fired up GNS3 and works out how to do it. Here is my topology;
So I will setup ‘port forwarding’ from the outside interface of ASA-1 for TCP ports 1000 to 2000 to then Internal Server (10.2.2.10).
1. Setup object groups for your internal server and for the range of ports you are going to forward.
! object network Obj-Internal-Server host 10.2.2.10 ! object service Obj-Ports-Range service tcp destination range 1000 2000 !
2. Then allow the traffic in with an ACL See MY WARNING before doing this.
! access-list inbound extended permit tcp any host 10.2.2.10 range 1000 2000 ! access-group inbound in interface outside !
3. Perform the PAT translation from the outside interface to the internal server.
! nat (outside,inside) source static any any destination static interface Obj-Internal-Server service Obj-Ports-Range Obj-Ports-Range !
Note: A lot of people ask to ‘port forward’ a range of ports when they actually mean ‘I would like to open a range of ports to an internal IP address’. Thats essentially just a one-to-one static NAT. I’ve already covered that before, but in our example i use a spare public ip 192.168.253.100.
! object network Obj-External-Server host 192.168.253.100 ! object network Obj-Internal-Server host 10.2.2.10 nat (inside,outside) static Obj-External-Server ! access-list inbound permit tcp any host 10.2.2.10 range 1000 2000 ! access-group inbound in interface outside

06/10/2017
Pete – How do you do port forwarding for multiple services to one inside host?
07/10/2017
Hi Tibby – what services?
P
11/08/2019
I have a requirement
I have one Internal Server 10.10.10.23 & I configured static PAT with interface. But the same server is listening on multiple Ports .in that case how to provide access for it
18/07/2018
ERROR: NAT unable to reserve ports.
18/07/2018
Usually seen if you have HTTPS or SSH in the list, the firewall has these reserved?
Pete
20/08/2018
I’m on version 8.2 and unable to upgrade to a later version due to expired support contract with Cisco. to make things worse, the customer has only one usable public IP froma /30 public IP network. so there are only 2 usable and the ISP uses one for their router already as our gateway. All the Cisco docs on 8.2 state that a range cannot be used adding the Static PAT rules, and the answer is to one-to-one it to an unused IP in the public block, which we don’t have. All we have is the same IP that is used for SNAT. I seem to remember some CCIE coming in and saving the day on a similar issue several years ago on 8.2, but I can’t recall exactly what they did. any suggestions? Cisco is saying we have to map each RTP port with it’s own statement for udp 10000 – 20000..but that’s 10001 separate NAT statements! That can’t be right. We had a real UTM device in there that got zapped last week and have had to fall back onto an old ASA 5520 with cli 8.3
22/08/2018
Cisco are correct thats how it used to be done! Your code is ten years old, you need a new firewall.
07/09/2018
Thanks so much for this post as it really helped me resolve a problem on a 5506-x with 9.x. One question for you that got me. I originally build the nats with the port ranges like so which I found on a cisco article here: https://www.cisco.com/c/en/us/support/docs/ip/network-address-translation-nat/118996-config-asa-00.html
nat (inside,outside) source static obj_host interface service obj_port_range obj_port_range
This was a valid nat but the outside interface didn’t seem to relay the ports as intended.
Once I created it with your example outside,inside it started working as intended. I think the thing that confused me this that when you do a NAT at the network object level it seems to work fine on a standard port map but it didn’t work this way building it as a normal nat rule.
10/09/2018
Thank for the feedback, I’ve struggled with this myself in the past, (hence the post). I just hammered away at it until it worked!
Regards,
Pete
05/05/2022
Hey Pete,
Quick question. With respect to the command:
nat (outside,inside) source static any any destination static interface Obj-Internal-Server service Obj-Ports-Range Obj-Ports-Range
Is that applied to the “Obj-Internal-Server” or the “object service Obj-Ports-Range” object? I’m guessing the latter since the interfaces are reversed from what I normally use when applied to a host rather than a service.
Thanks,
Don
05/05/2022
Both really! so it works like, map the outside interface to obj-internal-server, but only for the ports included in obj-ports-range
Does that make more sense?