Cisco FireSIGHT – Enable Active Directory (LDAP) Authentication
KB ID 0001102
WARNING this is for older versions of the FirePOWER Management Platform, go to the following link for newer versions
Cisco FirePOWER Management Appliance – Allowing Domain Authentication
Problem
To save you creating multiple users on your FireSIGHT appliance, and assigning roles to them you can utilise your existing Active Directory. In fact FireSIGHT does a good job of enabling granular administration based on AD Groups, by assigning them to ‘roles’ on the appliance.
Below I’m just going to create one AD group and assign the administrator role to that group,as you would in a small organisation. but I will point out how to enable RBAC on the appliance.
I had to work out how to do this, because the official documentation just does not work? Or at least it did not work for me with my 2012 R2 domain controller.
Solution
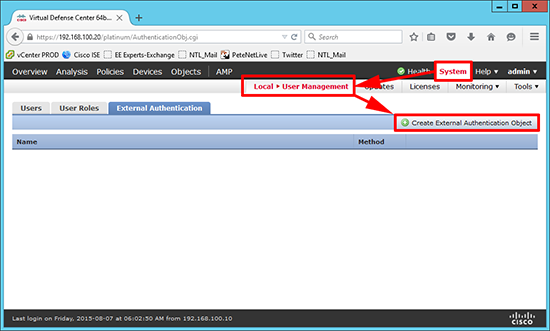
1. Log into FireSIGHT > System > Local > User Management > Create External Authentication Object.
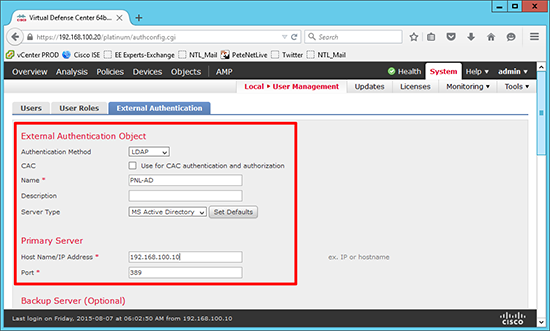
2. Authentication Method = LDAP > Name = Something descriptive > Description = {optional} > Primary Server IP = IP of you Domain Controller > Port = 389.
Note: If you change the authentication method below to SSL the port will automatically change to 636 (LDAPS).
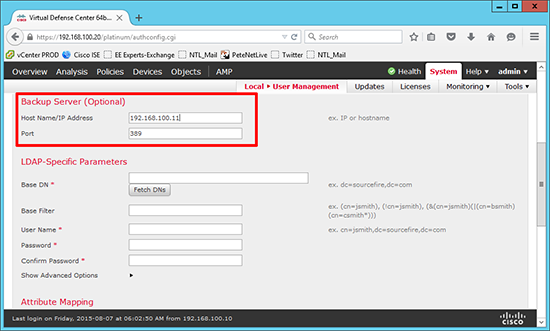
3. Enter a secondary domain controller IP if you have one.
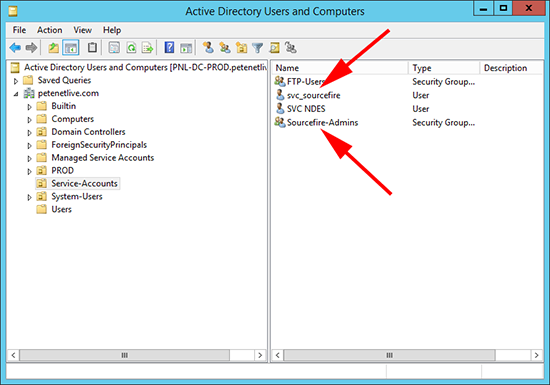
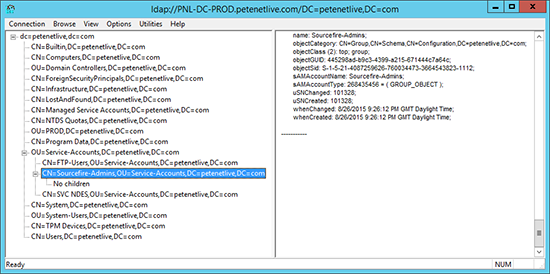
4. In my AD I’ve created a user for the appliance to connect to AD with (svc_sourcefire), and a group called Sourcefire-Admins that I’ve put my administrative users in.
5. In the FireSIGHT console you have to enter domain objects by their DN. If you’re unused to using DN notation, on the domain controller run LDP (Connection > Connect > Server=Localhost > OK > Connection > Bind > OK > View > Tree > OK) In the left window you can expand and navigate up and down your domain tree. When you find th group/user you want right click copy DN, Then you can paste it into FireSIGHT without having to write it out.
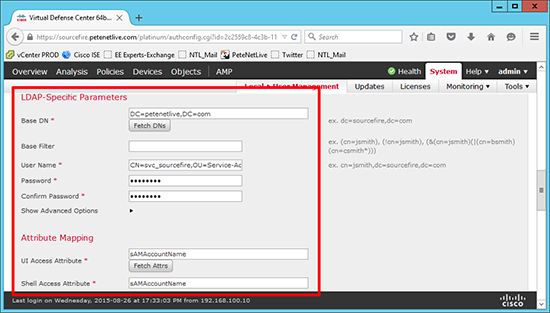
6. Set the Base DN (usually the root of the domain) e.g.
Enter the DN for the user the appliance will use to bind to Active Directory, e.g.
Enter the user (above) password. Set the UIAccess Attribute and the Shell Access Attribute to;
Note: The drop down arrow unlocks the advanced options if you wanted to use LDAPS then this is where you would select it and upload the root CA certificate.
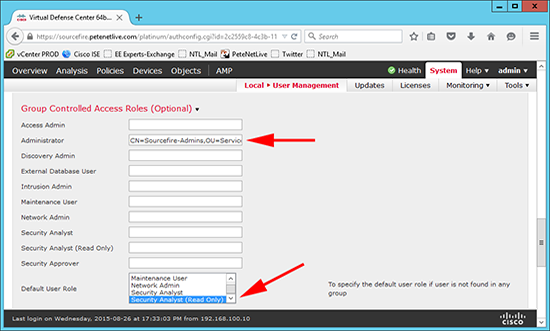
7. Expand Group Controlled Access Roles (Optional) > Enter your AD group against the role you want to assign to it e.g.
Note: These are the built in roles, you can clone and create new ones. (System > Local > User Management > User Roles).
Set the Default user role to ‘Security Analyst (Read Only)’.
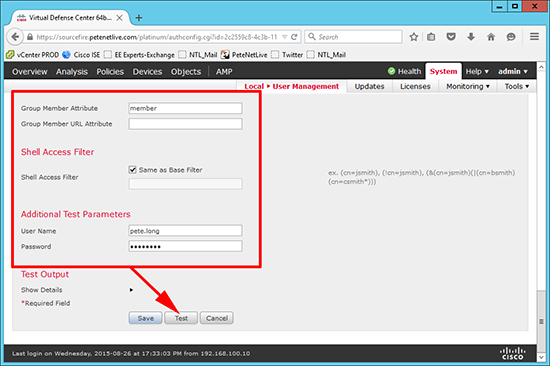
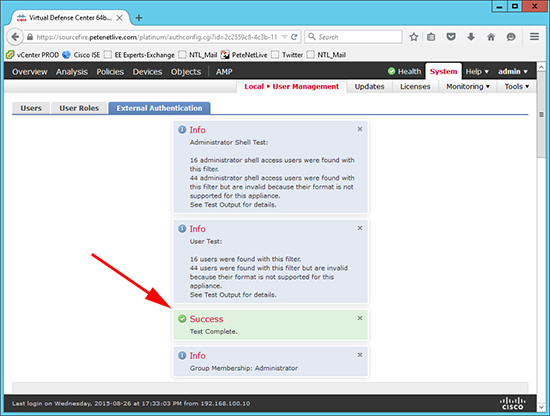
8. Group Member attribute = member > Shell Access Filter = ‘Same as Base Filter’ > Username enter an administrative username form the group you specified above > Password = password for the user you are testing > Test.
Note: Shell Access Filter wont actually do anything in this instance.
9.You will get a lot of info, but hopefully you will see ‘Success’.
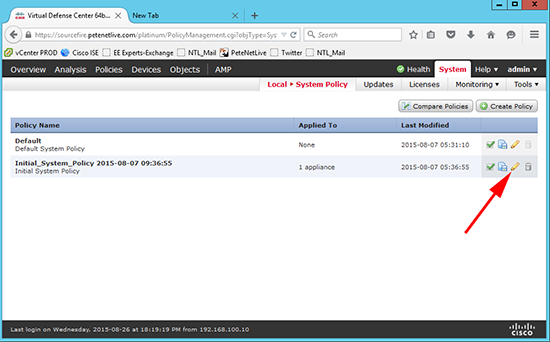
10. Now you need to use this authentication method for the appliance. System > Local > System Policy > Select the policy in use > Edit, (pencil icon).
11. External Authentication > Status = Enabled > Default User Role = Security Analyst (read Only), No I don’t know why you do this twice > Change the ‘slider button’ to enabled > Save Policy and Exit.
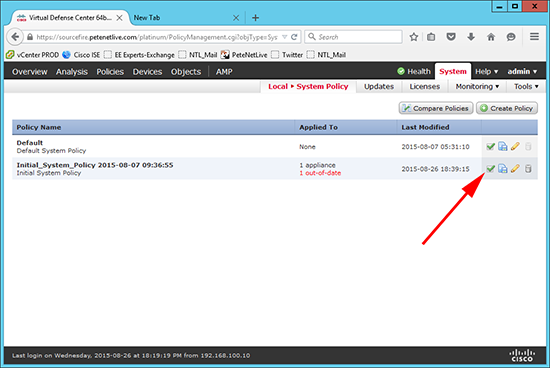
12. Because the policy has changed and not updated > Update.
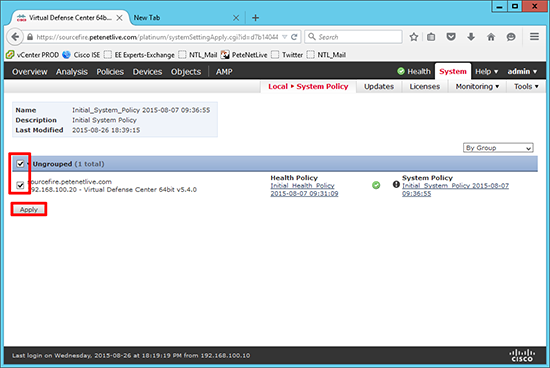
13. Select All > Apply.
14. Success.
15. You can not log in with your administrative AD accounts.
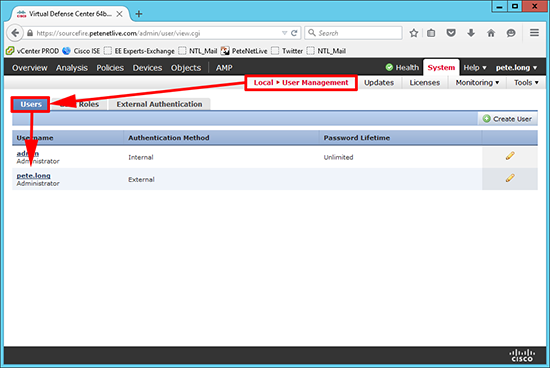
16. You will also notice the users appear under local user management > Users.
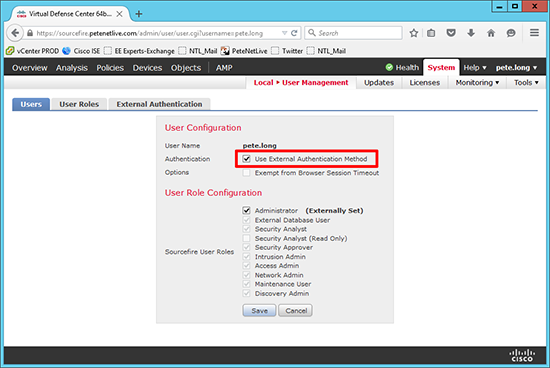
17. You could, (if you wished) Untick the ‘Use External Authentication Method’ option and turn this user into a ‘local’ user.
Related Articles, References, Credits, or External Links
NA