KB ID 0001077
Problem
Back in Part Two we configured the specific 802.1x policies in Cisco ISE. Remember with 802.1x it is a three tier system there is a supplicant, (a machine that wants to authenticate), the Authenticator, (the device the supplicant connect to, in our case a switch), and finally an Authentication server (Cisco ISE).
Below I will add our switch into ISE, as a RADIUS device and create some groups, and locations for good housekeeping.
Solution
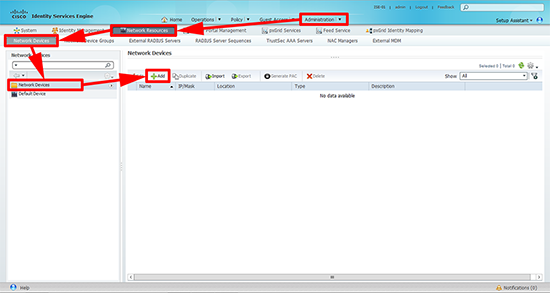
1. From within ISE > Authentication > Network Resources > Network Devices > Network Devices > Add.
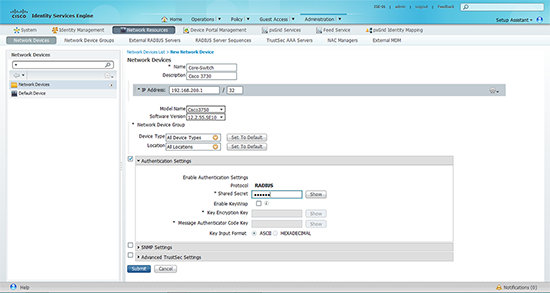
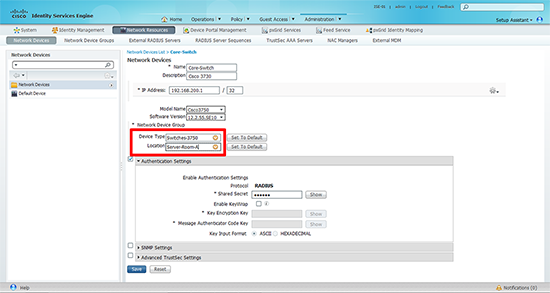
2. Specify a name and description for the device > Set its IP address > Set the device type and location (we will change these in a minute) > Under authentication settings select RADIUS and enter a shared secret, (you can set these up globally if you prefer).
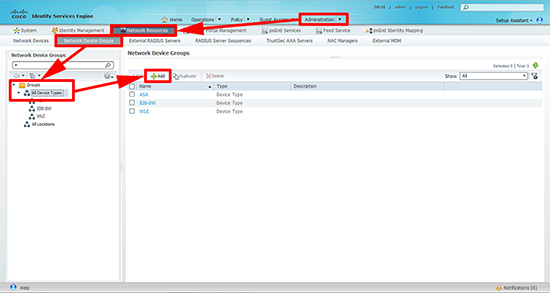
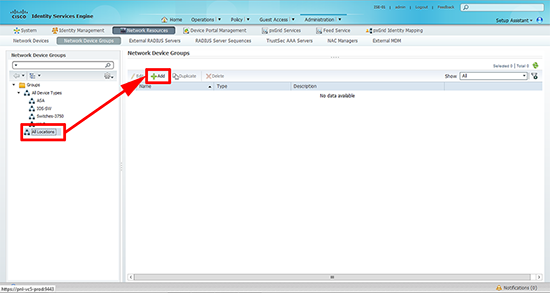
3. Create a Device Type: Administration > Network Devices > Network Device Groups > Groups > All Device Types > Add.
Note: You can have as many of these as you like to make managing your network easier, I’m just going to set one up for Cisco Switches.
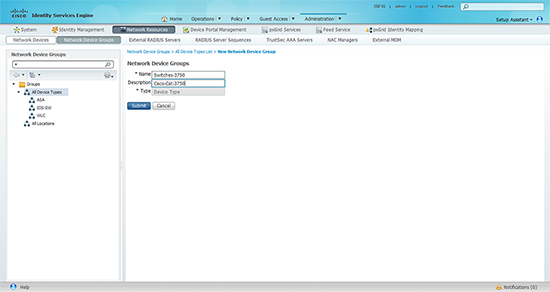
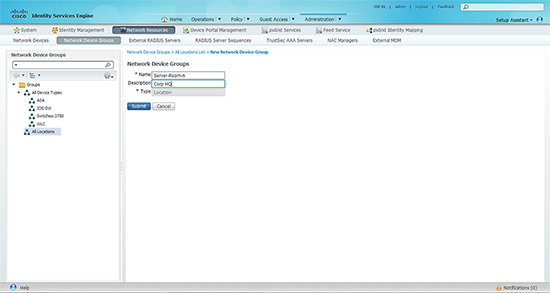
4. Give the group a name and description > Submit.
5. Create a Location: On the same page > All Locations > Add.
6. Give the location a name and description > Submit.
7. You can now go back to the network device you created earlier, and set the location and group accordingly.
8. Now you can configure the Cisco switch for RADIUS Authentication.
Note: 192.168.100.12 is the IP address of the ISE server, and 666999 is the shared secret we setup in step 2.
Petes-3750(config)#aaa new-model Petes-3750(config)#aaa group server radius ISE Petes-3750(config-sg-radius)#server-private 192.168.200.12 key 666999 Petes-3750(config-sg-radius)#exit Petes-3750(config)#aaa authentication dot1x default group ISE Petes-3750(config)#aaa authorization network default group ISE Petes-3750(config)#dot1x system-auth-control Petes-3750(config)#do write Building configuration... [OK] Petes-3750(config)#
9. To configure the port that our supplicant is going to connect to;
Note: I’m setting the host-mode to multi-host because my clients are all in VMware ESXi and are coming from a VMware vSwitch into the Cisco switch.
Petes-3750(config)#interface fastEthernet 1/0/4 Petes-3750(config-if)#authentication host-mode multi-host Petes-3750(config-if)# authentication port-control auto Petes-3750(config-if)# dot1x pae authenticator Petes-3750(config-if)#exit Petes-3750(config)#exit Petes-3750#write mem Building configuration... [OK] Petes-3750#
10. Once a supplicant has been authenticated you can check like so;
Petes-3750#show dot1x all summary
Interface PAE Client Status
--------------------------------------------------------
Fa1/0/4 AUTH 0050.56b1.5f5c AUTHORIZED
Petes-3750#
Related Articles, References, Credits, or External Links
Cisco ISE – Basic 802.1x With Windows – Part Four – Configuring The Windows Clients (Supplicants)