KB ID 0001059
Problem
Microsoft have released the Local Administrator Password Solution (LAPS). What is does is automatically change the load administrator password on workstations, (and servers if required) periodically. It then keeps those passwords securely in AD. Microsoft tried to mitigate attacks from the local admin account back in the days of Windows Vista by shipping with this account disabled, which is fine, but most large deployments I’ve worked on, I’ve been specifically asked to enable the local administrator account and set its password on deployment.
Some organisations create a different account and leave the local administrator account disabled, but they still suffer from the same problem, (all the machines have the same local admin password), and it gets known, if you have a disgruntled ex-employee they may know this password. Yes you can change them all periodically but it’s a bit of a faff. Note: LAPS can manage local accounts that are admin accounts but not necessarily the ‘administrator’ account.
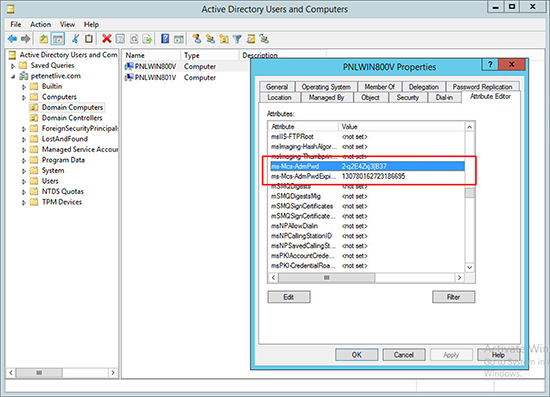
The LAPS solution works by creating some new attributes on the computer object, ms-MCS-AdmPwd which actually stores the password, and ms-MCS-AdmPwdExpirationTime which is the time stamp for the password expiration. What LAPS sets out to do, is provide a random complex password for the local administrator account, and protect that password in AD by use of an AD ACL. In doing so it will protect your machines from a ‘Pass the Hash’ attack which can use common local administrators passwords to compromise a network.
Solution
Microsoft LAPS – Step 1 Setup a Management Machine
1. On a management machine download and install the LAPS software, Things will be easier if this machine is also running RSAT tools for Active Directory, and the Group Policy Management Console as well.
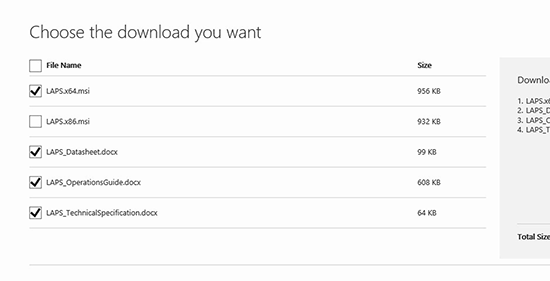
2. Be aware you get the documentation form the download page as well. Make sure you get the appropriate x86 or x64 bit version (LAPS supports Server 2003 SP1 and above).
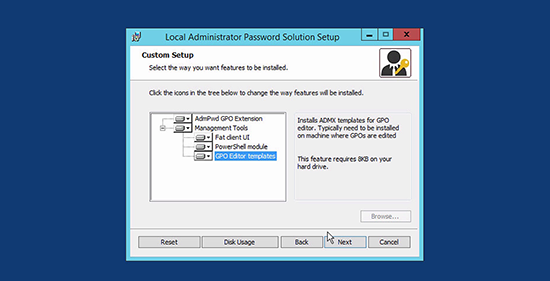
3. Install the software and install ALL the options. (if you apply the defaults it will only install the GPO Extensions), which is what you would want on the ‘controlled machines’ but you want everything on the ‘controlling machine’.
Microsoft LAPS – Step 2 Deploy the software to the machines to be controlled.
1. To be honest this could not be simpler, I just sent the software out as a standard software package via GPO, (watch the video above if you don’t know how to do that). You can script the install and it will also manually install with a /quiet switch to avoid any user interaction. But if you have any amount of machines, GPO is the way to go.
To manually install quietly;
msiexec /i \\Server\Share\laps.x64.msi /quiet or simply msiexec /i c:\laps.x64.msi /quiet
2. To check if the client has received the LAPS software, look in Add/Remove programs and you should see it listed (Run > appwiz.cpl {Enter}).
Microsoft LAPS – Step 3 Extend Active Directory Schema
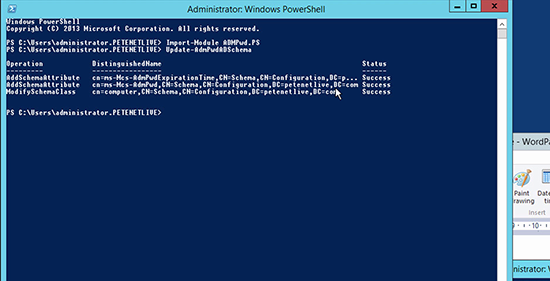
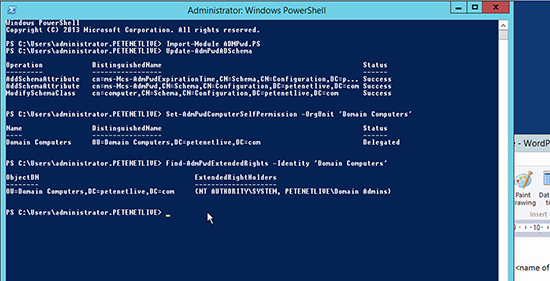
1. It goes without saying that to do this you need to be a member of ‘Schema Admins’. On the management machine run the following two PowerShell commands, to add the two new attributes mentioned above;
Import-Module AdmPwd.PS Update-AdmPwdADSchema
Microsoft LAPS – Step 4 Check/Set Permissions to Read Local Admin Passwords
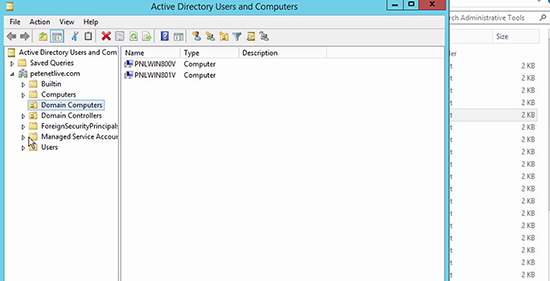
1. On my test network below you can see I’ve got a couple of test Windows 8 machines in an OU called ‘Domain Computers’, this is the OU that I will be working with.
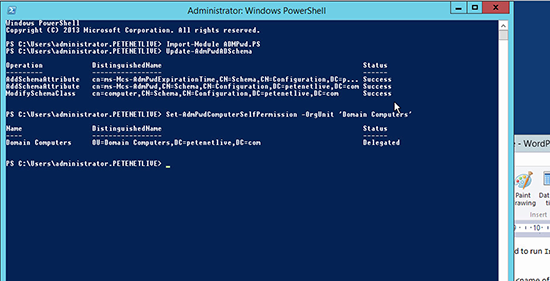
2. The first thing I need to do is grant the rights to the computers themselves to be able to update the password in Active Directory. (If you have nested OU’s, simply apply on the top level OU). Change the value in red to suit your own OU/OU’s.
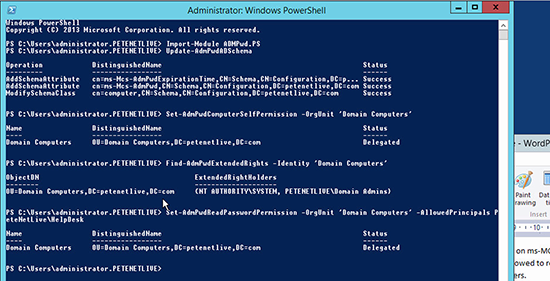
3. To see who has rights to view the passwords in AD (for a given OU), use the following command. Below you can see the default of SYSTEM and Domain Admins is displayed.
4. To grant read password permissions to a particular group, use the following syntax, below I have an AD group called HelpDesk setup and I’m adding them into the AD ACL to be able to read local administrator passwords for the Domain Computers OU.
Note: If you have multiple groups you can separate/delimit them with a comma.
Microsoft LAPS – Step 5 – Deploy the GPO Extensions to ‘Controlled’ Machines.
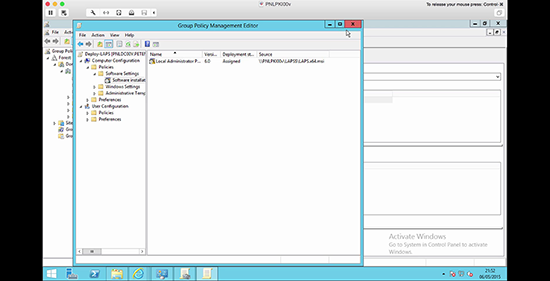
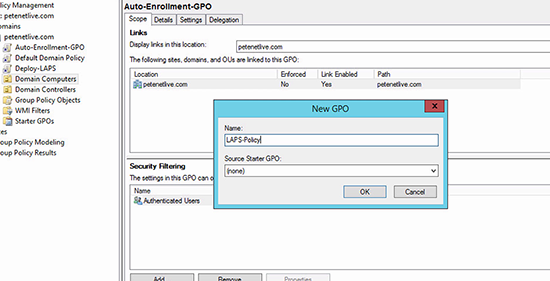
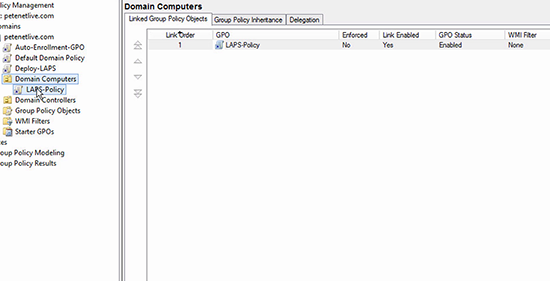
1. On the management machine, create a new GPO object, and link it to the OU containing the computers/servers you want to apply the password settings to.
2. Edit the GPO.
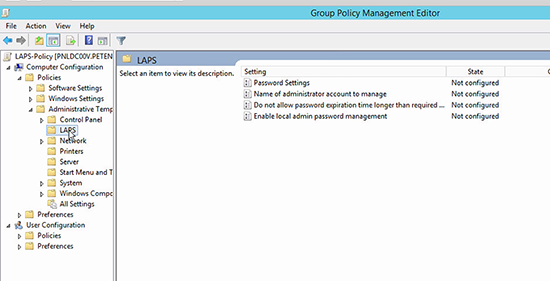
3. Navigate to;
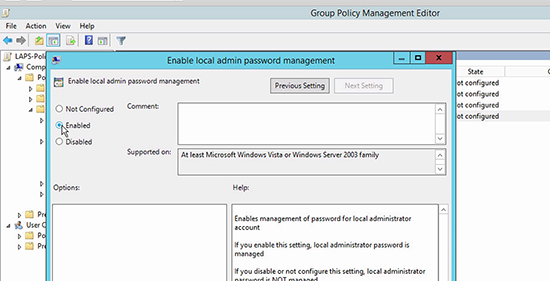
4. The policy that turns LAPS on is the last one ‘Enable local admin password management’ > Enable it.
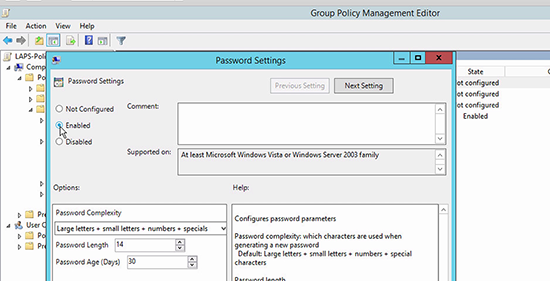
5. The actual complexity and age of the password is set in the ‘Password Settings’ policy, > Enable it and accept the defaults.
Note: the other two policies are;
Name of the administrator account to manage: Use if you you have manually created another common admin account on all your machines NOT if you have renamed the local administrator account.
Do not allow password expiration time longer than required by policy: Set to Enabled.
Microsoft LAPS – Step 6 – View the Local Admin Passwords for Controlled Machines.
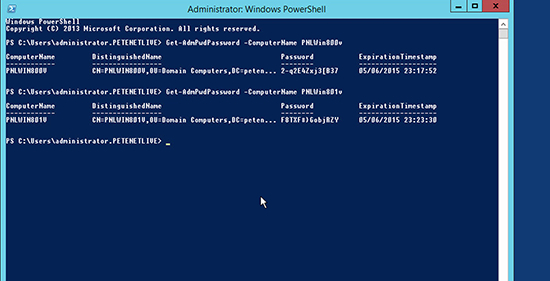
1. You can do this from PowerShell with the following command;
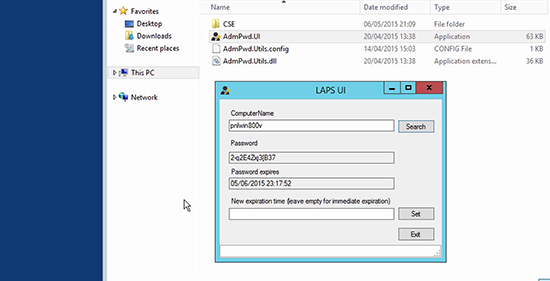
2. Or if you have installed the Fat client, you can launch that from;
3. Or as it’s an AD object attribute, you can view it on the Computers AD object.
Related Articles, References, Credits, or External Links
NA