KB ID 0001058
Problem
A few days ago I wrote about disabling SSL v3.0 to force your clients to connect with the more secure TLS v1.0. But what if your AnyConnect clients chose to connect with a weaker encryption cipher? The ciphers your firewall offer (by default) will vary depending on what OS your ASA is running.
Solution
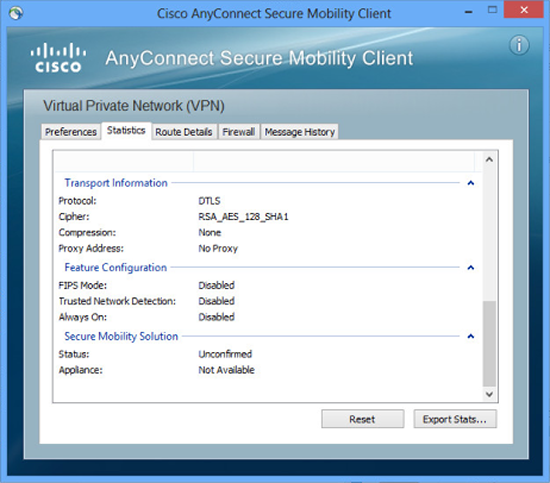
1. To see what your cipher you are connected with look on the statistics tab, below we are connecting with the AES 128 encryption protocol and using SHA1 for hashing.
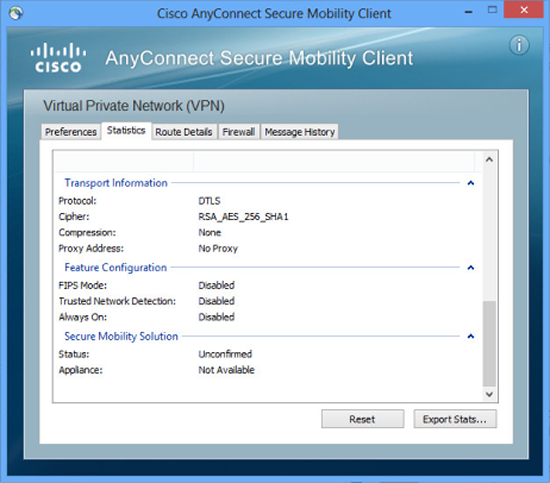
2. Where as here we are connecting with the more secure AES 256 and using SHA1 for hashing.
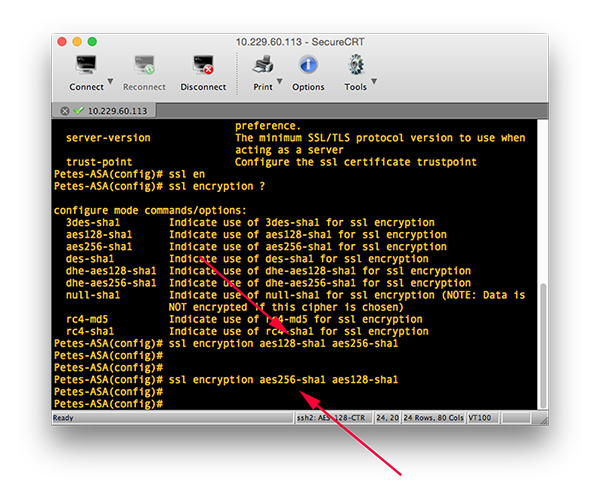
2. I force this by use of the ‘ssl encryption {option 1} {option 2} {etc.}’ approach. Below the first command indicated had AES 128 as the first encryption cipher, and the second command has AES 256, by specifying which order, you specify the order that the ASA offers the remote AnyConnect client.
WARNING: Removing ciphers can cause problems connecting to ASDM see this article.
Ciphers supported by AnyConnect 4
TLS 1.3 is supported in the software, but not supported on ASA until version 9.3(2)
- DHE-RSA-AES256-SHA256
- DHE-RSA-AES128-SHA256
- AES256-SHA256
- AES128-SHA256
Related Articles, References, Credits, or External Links
NA