KB ID 0001057
Problem
I was in the PIX/ASA area at EE last night, and a poster asked if they could perform NAT on a couple of internal IP addresses to a spare public IP that they had. I had done this for a client some time last year when I performed and upgrade from 8.2. Anyone who has ever done a large upgrade on an ASA to the ‘new’ NAT system, will appreciate this is usually the area where the upgrade has a problem. So at the time ran through all the NAT/PAT rules on their firewall and worked out how to do the same with the new NAT code. That way if the upgrade failed I’d have all the new NAT rules per-written, (time spent on reconnaissance is seldom wasted!) Anyway when this question was asked I could not find the config I’d written so I ran up GNS3 and tested it.
Solution
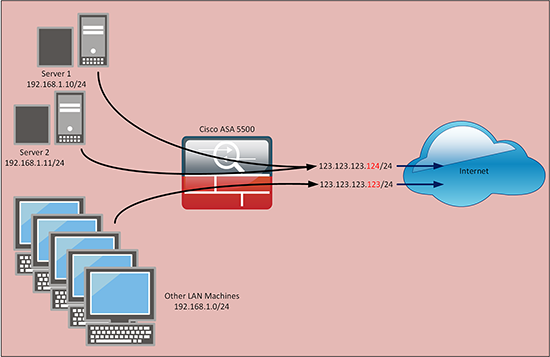
In the example (above), I’m going to PAT both the internal servers to a public IP address of 123.123.123.124. The firewall already translates all other outgoing traffic to its external IP of 123.123.123.123. Note: I’m just translating two internal IP addresses, but you can translate as many internal hosts to this rule as you like.
1. Create a ‘group’ for your internal IP addresses;
2. Create an ‘object’ for the spare public IP address;
3. Finally tie the two together with a NAT rule (that PAT’s the internal IP addresses to the spare public IP address). Remember this is a PAT not a NAT, hence the reason I use the ‘dynamic’ keyword below, and I don’t use ‘static’ as I would have done for a one-to-one NAT.
Note: The reason there’s a number ‘1’ in the command, is to put it at the top of the NAT processing order, so this rule will ‘fire’ before the global PAT rule I already have on the firewall.
4. At this point your internal servers may already have some NAT/PAT information cached on the firewall, before we test it let’s clear that out;
5. Now give it a test, you can check your public IP with the tool at the top of our ‘index page’, press the button that says ‘What’s is my IP‘. Once you are happy everything is working, save the changes on the firewall with a ‘write mem‘ command.
Related Articles, References, Credits, or External Links
NA