KB ID 0001042
Problem
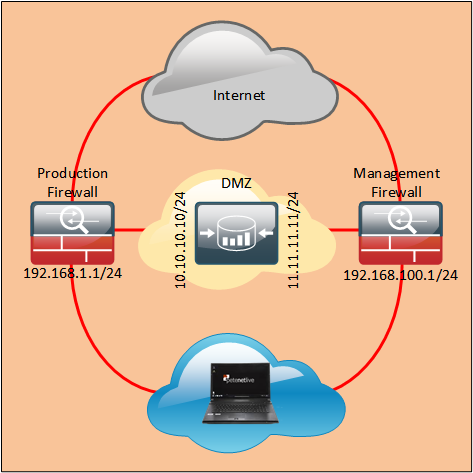
I’ve been working on a large firewall deployment for a client, each of their DMZ’s have both a production and a management network. nothing particularly strange about that, but each of their DMZ’s has its own firewalled management network and it’s routable from the LAN.
So If I’m an admin and I want to talk to a Linux appliance in their DMZ via its management interface, my traffic leaves the LAN through the management firewall, but the appliance sees my source IP as being on the LAN, and routes the traffic back to me via the clients production firewall.
Now the simplest way to fix it would be to put a static route on the appliance to route my traffic back via the management firewall, which is fine, BUT what if that appliance is the proxy server? Now I can administer it, but I cant get on the Internet!
Note: I’m NOT performing NAT anywhere in this scenario!
Solution
Well I could simply PAT the network my laptop is on, lets say its 172.16.1.0/16 to the DMZ interface of the management firewall.
object network Admin_PCs subnet 172.16.1.10 255.255.0.0 nat (inside,dmz) dynamic interface
The problem with that is it will translate all traffic from my laptop’s subnet going into this DMZ and I might not want to do that.
Solution Pre ASA 8.3
We used to have a really simple way of solving this problem, ‘policy based nat’, you specify a set of conditions with an ACL then anything that meets that ACL is tied to a specific NAT rule.
access-list POLICY-NAT permit ip host 172.16.1.10 11.11.11.11 255.255.255.0 ! static (inside,outside) interface access-list POLICY-NAT
Solution Post 8.3
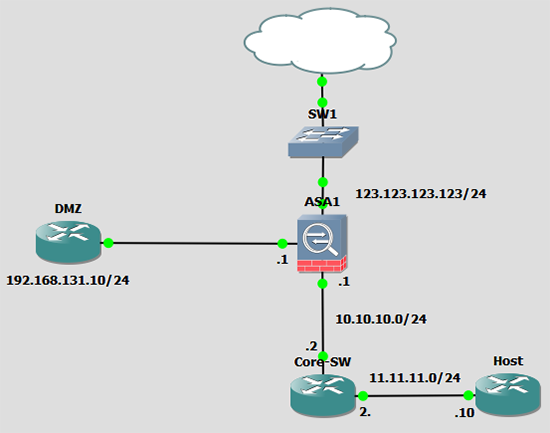
To do the same now the syntax is a little different. To demonstrate I have built a small lab in GNS3 to demonstrate. If I want the internal host to talk to the DMZ host, I want the traffic when it gets there to ‘appear’ to have come from 192.168.131.1
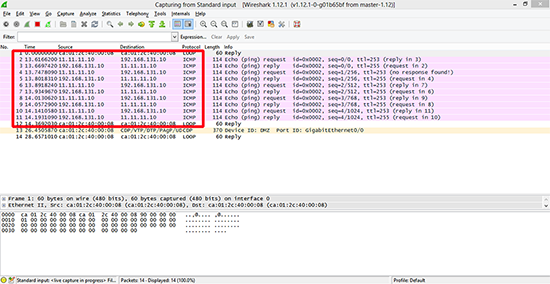
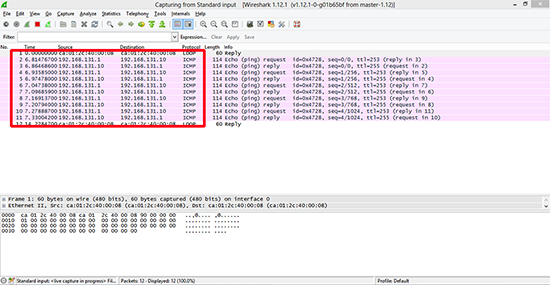
To demonstrate, if I ‘ping’ the DMZ router from the Host router, and Wireshark the traffic when it gets there, I see its coming from its actual IP address.
To NAT this traffic use the following commands;
For a Single IP object network obj-Host host 11.11.11.10 ! object network obj-DMZ host 192.168.131.10 nat (inside,DMZ) source static obj-Host interface destination static obj-DMZ obj-DMZ For the Entire Subnet object network obj-Host-LAN subnet 11.11.11.0 255.255.255.0 ! object network obj-DMZ-LAN host 192.168.131.10 nat (inside,DMZ) source dynamic obj-Host-LAN interface destination static obj-DMZ obj-DMZ
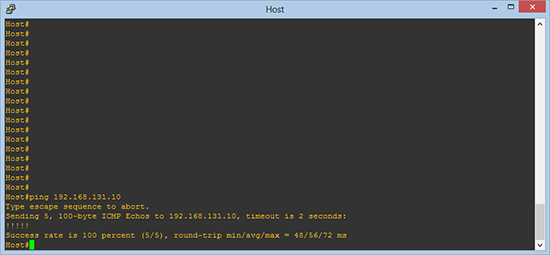
Now if we repeat the process, and ping the DMZ host.
Now when I capture the traffic, the source IP has changed accordingly.
Related Articles, References, Credits, or External Links
NA