KB ID 0001001
Problem
If you have one client that’s taking all your bandwidth, or a server that’s getting a lot of connections from external IP addresses, and that’s causing you performance problems, you can ‘throttle’ traffic from/to that client by ‘policing’ its traffic.
Solution
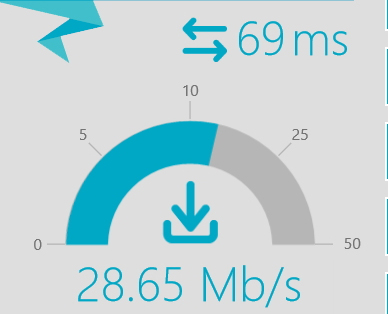
To demonstrate, I have a 30Mb connection at home, when I run a test on the download connection speed from my desktop PC this is what I get;
So I’m going to throttle traffic to that IP address (10.254.254.90), so that it can only use 1Mb of the connection.
1. Create an ACL for traffic to and from the IP address you want to throttle. (Note: If your firewall is running a version older than 8.3, and you are throttling an IP that has a public IP address, use its public IP address not its private one).
User Access Verification
Password:******* Type help or ‘?’ for a list of available commands. PetesASA> enable Password: ******** PetesASA# configure terminal PetesASA(config)# access-list ACL-THROTTLE extended permit ip host 10.254.254.90 any PetesASA(config)# access-list ACL-THROTTLE extended permit ip any host 10.254.254.90
2. Now create a class-map that will match all traffic in that ACL, (so all traffic to and from 10.254.254.90).
PetesASA(config)# class-map CM-THROTTLE PetesASA(config-cmap)# match access-list ACL-THROTTLE PetesASA(config-cmap)# exit
3. Then create a policy-map, that takes all traffic identified in your class map, and rate limits the traffic to 1000000 bps (1Mbps) with a ‘burst-rate’ of 2000bps.
PetesASA(config)# policy-map PM-THROTTLE PetesASA(config-pmap)# class CM-THROTTLE PetesASA(config-pmap-c)# police output 1000000 2000 PetesASA(config-pmap-c)# police input 1000000 2000 PetesASA(config-pmap-c)# exit PetesASA(config-pmap)# exit
4. Now apply that policy-map with a service policy. (Note: Generally you apply the policy to the interface closest to where the traffic is coming from, as this is an internal host, I’m applying it to the inside interface. If you were throttling traffic from outside it would be better to apply the service-policy to the outside interface).
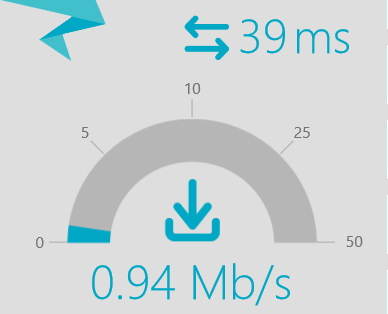
PetesASA(config)# service-policy PM-THROTTLE interface inside5. Let’s run our test again.
6. Looks good!
Related Articles, References, Credits, or External Links
NA