VPN Client Internet Access KB ID 0000977
Problem
I have answered a lot of questions in forums, that are worded something like, “When I have a remote client connected to my firewall VPN they lose Internet access!” Traditionally that’s exactly what the ‘default’ remote VPN Internet access (IPSEC or AnyConnect) gave you.
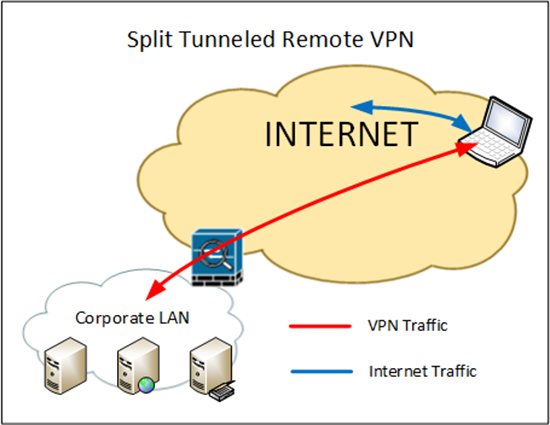
To ensure your remote VPN clients can access the Internet you have two options. The first (and most common) way is to enable ‘Split Tunneling’ this lets the user access the Internet form their LOCAL Internet connection.
Or you can provide Internet connection via the ASA’s public Internet connection, this is known as a ‘Tunnel All’ solution.
Solution : VPN Internet Access
At this point I’m assuming you have a remote VPN setup and working, if not you need to do that first, here are some walk-throughs I’ve already done to help you set that up.
Cisco ASA 5500 AnyConnect Setup From Command Line
Note: Split tunneling is covered in this article.
Cisco ASA 5500 IPSEC VPN Setup
Note: Split tunneling is covered in this article.
Option 1 (Split Tunneling) VPN Client Internet Access
Rather than re-invent the wheel, I’ve already covered this before in the following article.
Cisco ASA – Enable Split Tunnel for IPSEC / SSLVPN / WEBVPN Clients
Option 2 (Tunnel All Split Tunneling) VPN Client Internet Access
1. Connect to the ASA > Go to enable mode > Then to global configuration mode.
Type help or '?' for a list of available commands. PetesASA> enable Password: ****** PetesASA# configure terminal
2. Now you need to create an object group for your remote VPN clients (show run ip local pool should tell you what subnet you are using). And create a NAT rule for traffic originating on the remote client and going back out of the ASA’s outside interface.
PeteASA(config)# object network VPN_Pool PeteASA(config-network-object)# subnet 10.0.0.0 255.255.255.0 PeteASA(config-network-object)# nat (outside,outside) after-auto source dynamic VPN_Pool interface
3. Now as traffic is going to come in through the outside interface, turn around, and go back out of the same interface we need to allow that.
PeteASA(config)# same-security-traffic permit intra-interface4. Add the ‘tunnel all’, and force the remote client to use your DNS servers, to the policy you are using for your remote VPN, (if you are unsure issue a show run group-policy).
PeteASA(config)# group-policy SSL_Policy attributes PeteASA(config-group-policy)# split-tunnel-policy tunnelall PeteASA(config-group-policy)# split-tunnel-all-dns enable PeteASA(config-group-policy)# exit PeteASA(config)#
5. Save the changes.
PeteASA(config)# write mem
Building configuration...
Cryptochecksum: cb28eeb2 3d203272 eda92e1c a3b70d09
3166 bytes copied in 0.890 secs [OK] PeteASA(config)#
Related Articles, References, Credits, or External Links
Configure Secure Client with Split Tunneling on an ASA