KB ID 0000970
Problem
I’ve covered setting up NDES at length in the past, but what happens when your issued certificates expire? If you are using them for all your VPNs what then? Well thankfully you can get your devices to automatically re-enroll and before they expire, for example to renew the cert at 80% of its lifetime you would use the following;
crypto pki trustpoint PNL-TRUSTPOINT enrollment url http://123.123.123.130/CertSrv/mscep/mscep.dll usage ike serial-number ip-address 123.123.123.90 enrollment mode ra revocation-check none enrollment retry count 100 enrollment retry period 5 fqdn RTR2hr.testbench.local rsakeypair PNL-TRUSTPOINT 2048 auto-enroll 80 regenerate
However, there is a problem, if you are using Server 2008 there’s a hot-fix (and you need to make the following change as well) I’m on Server 2012 and mine was failing.
Solution
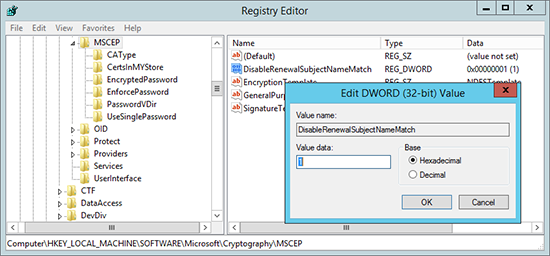
1. On the server running the NDES Server role > Open the registry editor and navigate to;
Create a new 32bit DWORD Value called DisableRenewalSubjectNameMatch and set its value to 1 (one).
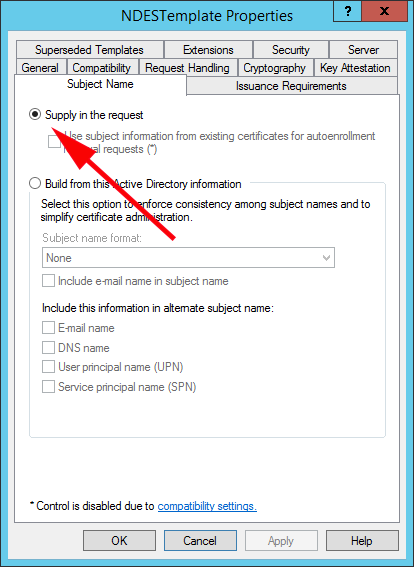
2. Also ensure the certificate that you are using or NDES, has the following settings, here I’m using a custom template called NDESTemplete, If you are using the default one it will be called ‘IPSec (Offline request)‘. On the Subject Name tab make sure ‘Supply in the request’ is selected.
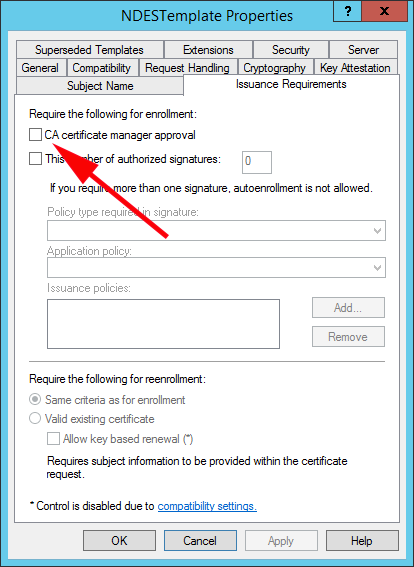
3. On the ‘Issuance Requirements’ tab, ensure ‘CA certificate manager approval’ is NOT selected.
Related Articles, References, Credits, or External Links
NA