KB ID 0000948
Problem
To get your Cisco Router or Switch to enroll, and obtain a certificate from a Windows Server running NDES, this is the procedure you need to follow.
Solution
When dealing with certificates, it’s important that your device is maintaining the correct time. You can set this manually, but I’d recommend setting up NTP.
Setting IOS Time (Manually and via NTP)
1. Choose either of the options below, (as applicable). Note: I’m in the UK so my time is GMT, and I need to allow for daylight saving time, (so your settings ma vary depending on your locale).
Setting Time Manually Petes-RTR(config)#clock timezone GMT 0 Petes-RTR(config)#clock summer-time BST recurring last Sunday March 01:00 last Sunday October 01:00 Petes-RTR(config)#exit Petes-RTR#clock set 10:47:00 Apr 30 2014 Petes-RTR#show clock 10:47:05.499 BST Wed Apr 30 2014 Petes-RTR# Setting Time via NTP Petes-RTR#show clock *15:36:38.383 PCTime Mon Feb 16 2009 Petes-RTR#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Petes-RTR(config)#ntp server 87.124.126.49 APPLY THE 'CUP Of COFFEE RULE' Petes-RTR#show clock 10:09:52.437 PCTime Wed Apr 30 2014 Petes-RTR#
Enrolling via NDES
1. Make sure the device can contact the NDES server, (simply pinging it should suffice). Then set a hostname and domain name. These are required to generate an RSA Key-pair on the device before we start.
R1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. R1(config)#hostname RTR-1 RTR-1(config)#ip domain-name testbench.local RTR-1(config)#crypto key generate rsa modulus 2048 The name for the keys will be: RTR-1.testbench.local % The key modulus size is 2048 bits % Generating 2048 bit RSA keys, keys will be non-exportable...[OK] RTR-1(config)# *Mar 1 01:01:47.491: %SSH-5-ENABLED: SSH 1.99 has been enabled
2. Create a set of CA settings (a trustpoint), then authenticate to it.
RTR-1(config)#crypto pki trustpoint PNL-TRUSTPOINT RTR-1(ca-trustpoint)# enrollment url http://192.168.80.130/CertSrv/mscep/mscep.dll RTR-1(ca-trustpoint)#enrollment mode ra RTR-1(ca-trustpoint)#revocation-check crl RTR-1(ca-trustpoint)#enrollment retry count 3 RTR-1(ca-trustpoint)#enrollment retry period 5 RTR-1(ca-trustpoint)#fqdn RTR-1.testbench.local RTR-1(ca-trustpoint)#exit RTR-1(config)#crypto pki authenticate PNL-TRUSTPOINT Certificate has the following attributes: Fingerprint MD5: 0454B8F4 73374DE8 2FB034CB B887B1D4 Fingerprint SHA1: 2A542238 0CF3856B D0EF3E1A CBB57003 21C114F5 % Do you accept this certificate? [yes/no]: yes Trustpoint CA certificate accepted. RTR-1(config)#
3. If your NDES Server requires a password you can embed that.
NDES Server Removing or Enforcing Passwords
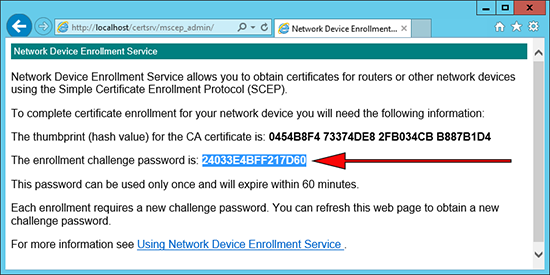
If you require a password you can obtain it from the NDES Server using the following URL.
http://{IP-or-name-of-NDES-server}/CertSrv/mscep_admin
This is the password you need to enter.
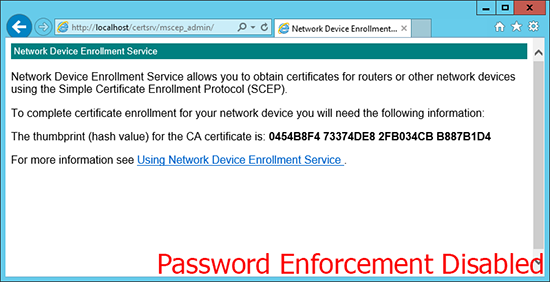
If it looks like (below), then password enforcement has been disabled, and you can skip the next step.
Firewall(config)# crypto ca trustpoint PNL-TRUSTPOINT Firewall(config-ca-trustpoint)# password 24033E4BFF217D60
4. Enroll for a certificate.
RTR-1(config)#crypto pki enroll PNL-TRUSTPOINT % % Start certificate enrollment .. % The subject name in the certificate will include: RTR-1.testbench.local % Include the router serial number in the subject name? [yes/no]: yes % The serial number in the certificate will be: FTX0945W0MY % Include an IP address in the subject name? [no]: no Request certificate from CA? [yes/no]: yes % Certificate request sent to Certificate Authority % The 'show crypto ca certificate PNL-TRUSTPOINT verbose' commandwill show the fingerprint. RTR-1(config)# May 14 10:46:46.479: CRYPTO_PKI: Certificate Request Fingerprint MD5: 25E06B18 2BF6E2B7 780AA427 89AB9A15 May 14 10:46:46.483: CRYPTO_PKI: Certificate Request Fingerprint SHA1: 044725E7 B34F6AF8 EFB4C28B 8E7CE192 230BDC9E RTR-1(config)# May 14 10:46:47.875: %PKI-6-CERTRET: Certificate received from Certificate Authority RTR-1(config)#
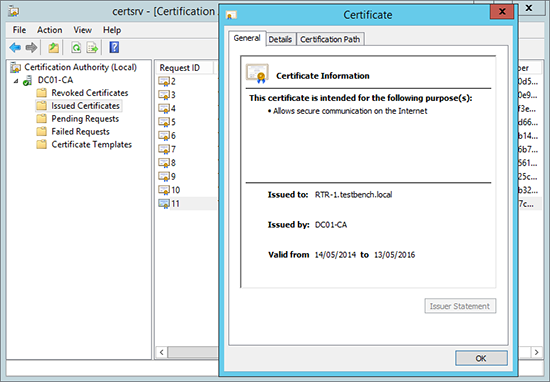
5. If you have a look on the Certificate Server you will also see that the certificate has been issued.
Oh Crap! It went wrong?
Possible errors you might see;
Error 1
RTR-1(config)#crypto key generate rsa modulus 2048 % Please define a domain-name first.
To be honest, it couldn’t be more descriptive! You can’t generate an RSA key-pair without a hostname, and a domain name.
R1(config)#hostname RTR-1 RTR-1(config)#ip domain-name testbench.local
Error 2
RTR-1(config)#crypto pki authenticate PNL-TRUSTPOINT % Error in saving certificate: status = FAIL RTR-1(config)#%CRYPTO_PKI: Cert not yet valid or is expired - start date: 13:18:46 UTC May 12 2014 end date: 13:28:46 UTC May 12 2019
Certificates are time specific, make sure the device has its clock set correctly, (preferably via NTP). And the time on the Certificate Services Server is set correctly.
Remember: We set the device to check the Certificate Servers CRL, make sure that’s setup properly, and the device can resolve its name.
Windows Certificate Services – Setting up a CRL
Related Articles, References, Credits, or External Links
Windows Server 2012 – Install and Configure NDES