KB ID 0000931
Problem
If you have a Cisco router that you have forgotten the password for, or have been given one, or simply bought one from ebay, you may not know the password. In fact many years ago an ISP was going to charge me a ridiculas amount of money to put an entry in a routers routing table, this procedure ‘ahem’ would have allowed to to do it myself, for free, and then reload the router.
Solution
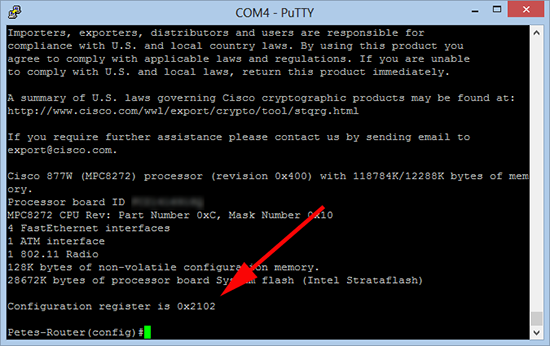
The reason you are able to do this is because of the router’s configuration register, this is the setting that decides how the system boots and how it operates. Usually it’s set to 0x2102 you can see this on a working router by running a ‘show version‘ command.
There are a number of different config register settings;
|
Configuration Register |
Router Behavior |
| 0x102 | Ignores break, 9600 console baud |
| 0x1202 | 1200 baud rate |
| 0x2101 | Boots into bootstrap, ignores break, Boots into ROM if initial boot fails, 9600 console baud rate |
| 0x2102 | Ignores break, Boots into ROM if initial boot fails, 9600 console baud rate default value for most platforms |
| 0x2120 | Boots into ROMmon, 19200 console speed |
| 0x2122 | Ignores break, Boots into ROM if initial boot fails, 19200 console baud rate |
| 0x2124 | NetBoot, Ignores break, Boots into ROM if initial boot fails, 19200 console speed |
| 0x2142 | Ignores break ,Boots into ROM if initial boot fails, 9600 console baud rate, Ignores the contents of Non-Volatile RAM (NVRAM) (ignores configuration) |
| 0x2902 | Ignores break, Boots into ROM if initial boot fails, 4800 console baud rate |
| 0x2922 | Ignores break, Boots into ROM if initial boot fails, 38400 console baud rate |
| 0x3122 | Ignores break, Boots into ROM if initial boot fails, 57600 console baud rate |
| 0x3902 | Ignores break, Boots into ROM if initial boot fails, 2400 console baud rate |
| 0x3922 | Ignores break, Boots into ROM if initial boot fails, 115200 console baud rate |
The one we are interested in I’ve emboldened above (0x2142), if we can boot the router, without loading the config, we can manually load the config whilst we have administrative access, which means we can do what we like, (including changing the passwords).
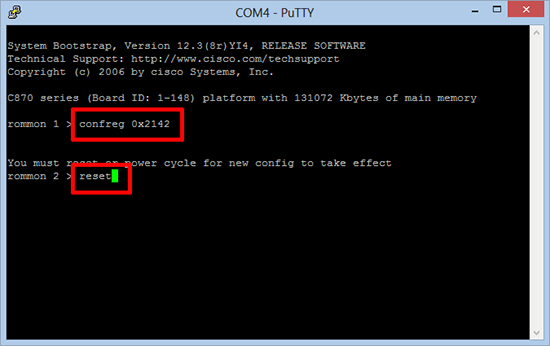
1. Connect a console cable to the router and connect to it using some terminal emulation software (like PuTTy)*. Power cycle the router and as it starts to boot press the ‘break’ key (on some keyboards press Ctrl+Break, on others you can simply press the Esc Key. You will know you are successful if the router boots into ROMMON mode. Issue the following commands;
rommon 1 > confreg 0x2142 rommon 2 > reset
*Typically at Baud 9600, 8 bits, 1 Stop Bit, No parity, No flow control.
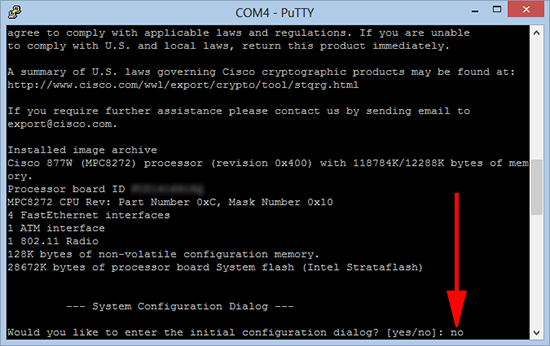
2. The router will reboot, when prompted select no to not enter the setup dialog. (Don’t panic your config is safe in NVRAM!).
3. Now you can go to enable mode without entering a password, and load the routers startup-configuration into memory.
Router> enable Router# copy startup-conig running-config Destination filename [running-config]? {Enter}
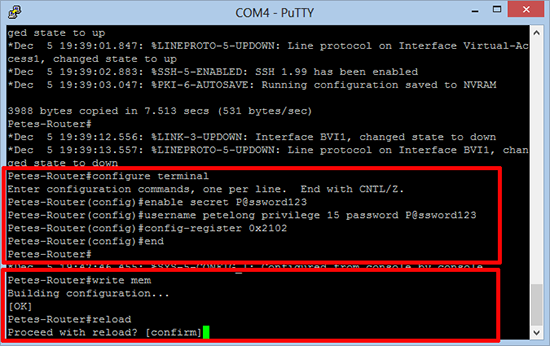
4. You can at this point make any changes you like, but we are here to change the passwords. On this router I want to reset the enable password, and I protect console access with a username and password, so I want to add a new one for myself. Set the configuration register back to its default setting of 0x2101, save the changes. Then reload the router and make sure you can now get access.
Petes-Router# configure terminal Enter configuration commands, one per line. End with CNTL/Z. Petes-Router(config)# enable secret P@ssword123 Petes-Router(config)# username petelong privilege 15 password P@ssword123 Petes-Router(config)# config-register 0x2102 Petes-Router(config)# end Petes-Router# write memory Petes-Router# reload Proceed with reload? [confirm] {Enter}
5. And we are in.
Related Articles, References, Credits, or External Links
Cisco Catalyst Password Recovery / Reset
Cisco ASA – Password Recovery / Reset
Cisco PIX (500 Series) Password Recovery / Reset