KB ID 0000921
Problem
I first saw this problem a few years ago trying to get some Windows clients to auto enrol with server 2008, then this week my colleagues could not get new 2019 Domain Controller to enrol for a Kerberos certificate, and the this was caused by the same problem.
Symtoms (RPC Error)
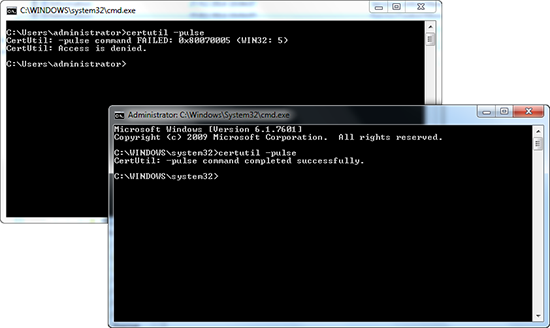
1. Test to make sure the client can see the CA, and is able to communicate with it, issue the following command;
certutil -pulse
As you can see above, the first time I ran the command I got the following error;
CertUtil: -pulse command FAILED: 0x80070005 (WIN32: 5)
CertUtil: Access is denied.
I then ran the command window ‘as administrator’ and it completed, this was the first inkling I had, that permissions were probably not right.
2. Run mmc on an affected machine, and add in the certificates (local computer*) snap-in. right click the ‘personal container’ > attempt to get the certificate you have published manually.
Problem seen on a Domain Controller (Attempting to get a Kerberos Certificate).
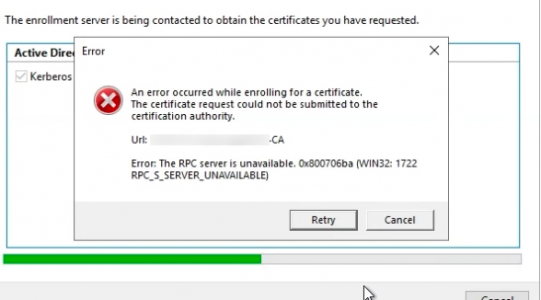
An error occurred while enrolling for a certificate.
The Certificate request could not be submitted to the certification authorityUrl: {CA Server Path}
Error: the RPC server is unavailable. 0x80076ba (WIN32: 1722
RPC_S_SERVER_UNAVAILABLE)
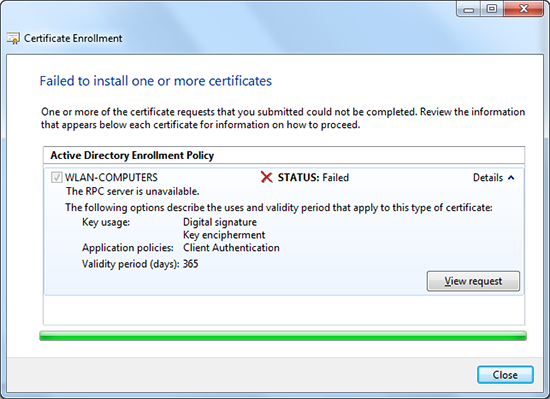
Problem seen on Windows Client (attempting to enrol for a Computer Certificate).
*Or local user if you are auto enrolling user certificates.
At that point I on the Windows cliebntgot this error;
Active Directory Enrollment Policy
STATUS: FailedThe RPC server is unavailable.
Resolution (Windows Certificate RPC Error)
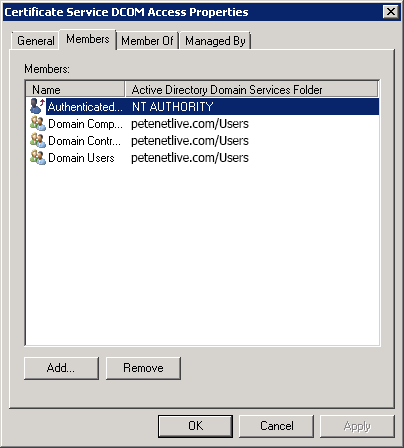
The most common cause for that error, is the membership of the ‘Certificate Service DCOM Access’ group is incorrect, check yours and make sure it matches the one below.
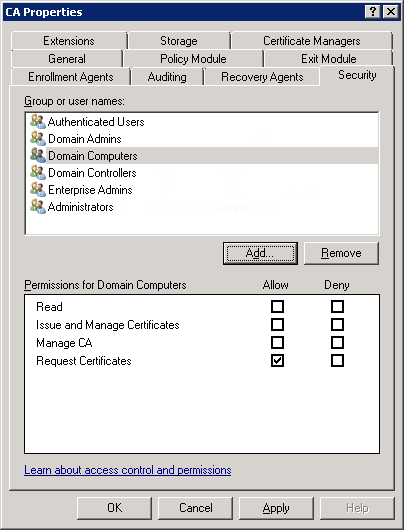
On the CA Server launch the Certification Authority management tool and look at the properties of the CA Server itself, on the security tab make sure yours looks like this, (Domain computer and domain controllers should have the ‘request certificates‘ rights).
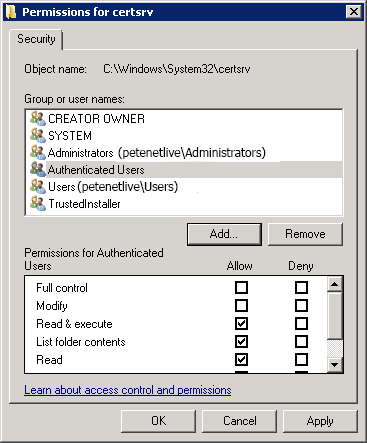
Still on the CA Server, check the permissions on the C:Windows\System 32\certsrv directory, authenticated users should have Read & Execute rights.
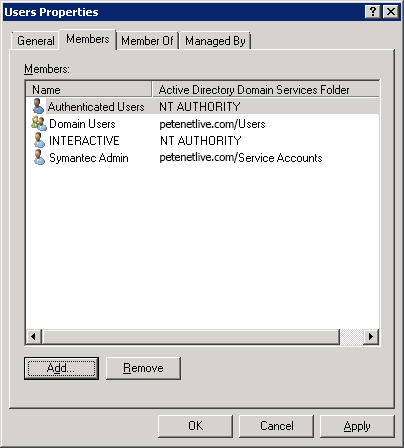
This is the change that finally fixed mine: In active directory users and computers, locate the Builtin container, within it there is a group called ‘Users’. Make sure it contains Authenticated Users and INTERACTIVE.
Run a ‘gpupdate /force’ on your test client, and/or reboot it.
Related Articles, References, Credits, or External Links
NA