KB ID 0000753
Problem
I’d always assumed that as Tracert uses ICMP, and that simply adding ICMP inspection on the ASA would let Tracert commands work. A client of mine is having some comms problems and wanted to test comms from his remote DR site, he had enabled time-exceeded and unreachable on the ASA (for inbound traffic) and that had worked. I checked the default inspection map and found inspect ICMP was there?
As it turns out Tracert does NOT NEED ICMP inspection, though there are a few tweaks you need to do to make it run correctly.
Solution
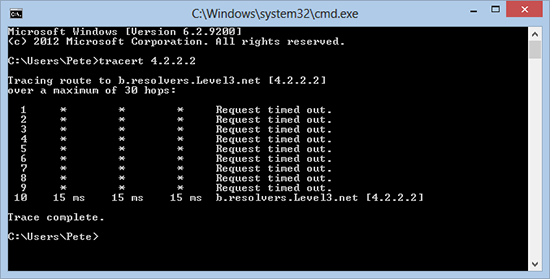
1. From a Windows client if I try and Tracert to an external IP address, this is what I would see.
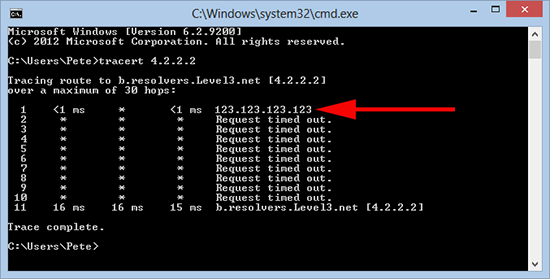
2. My first task is to get the ASA itself to reply to me, unlike most network devices the ASA does not decrease the ‘hop count’ as traffic passes through it, to rectify this we need to make a small change to the global inspection policy like so;
Sent username "pix" Type help or '?' for a list of available commands. Petes-ASA> Petes-ASA> enable Password: ******* Petes-ASA# configure terminal Petes-ASA(config)# policy-map global_policy Petes-ASA(config-pmap)# class class-default Petes-ASA(config-pmap-c)# set connection decrement-ttl Petes-ASA(config-pmap-c)# exit Petes-ASA(config-pmap)# exit Petes-ASA(config)#
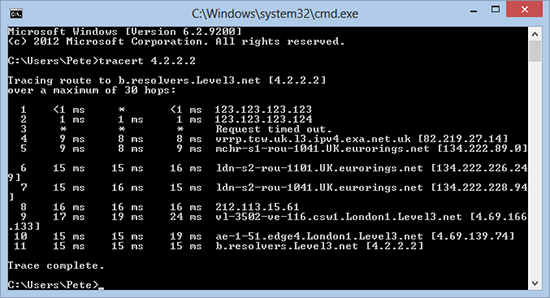
3. Now when we re-run our Tracert we see the ASA now responds, nothing else does though, to rectify that we need to allow IN some ICMP traffic.
4. Before you can add an ACL you need to see if you already have one. We are applying an ACL to the outside interface for traffic going in (I call this inbound for obvious reasons). To see if you already have an ACL applied, issue the following command;
Petes-ASA# show run access-group
access-group inbound in interface outside
access-group outbound in interface insideNote: In the example above we have an ACL called inbound that we MUST use. (If you added a new one, all the access list entries for the old one get ‘Un-applied’). If yours has a different name (e.g. outside_access_in then use that instead of the ACL name I’m using here). If you DONT have an access-group entry for inbound traffic then we will do that at the end!
5. At this point you should know if you have an ACL, mines called inbound so I need to add two lines to it like so;
Petes-ASA(config)# access-list inbound extended permit icmp any any time-exceeded Petes-ASA(config)# access-list inbound extended permit icmp any any unreachable
Then: Only carry out the following command if you DO NOT HAVE an ACL applied for incoming traffic.
Petes-ASA(config)# access-group inbound in interface outside6. Try your Tracert again.
7. Don’t forget to save the changes on the ASA.
Petes-ASA(config)# write mem Building configuration… Cryptochecksum: b984ffbc dd77cdbf f2cd8d86 0b8f3f96
3965 bytes copied in 1.490 secs (3965 bytes/sec) [OK]