KB ID 0000733
Problem
You have two ASA firewalls deployed in Active/Standby failover configuration, and need to upgrade either the operating system or the ASDM. As you already have a high availability solution you do not want any downtime.
Before we start, we need to make sure we know the difference between primary, secondary, active and standby.
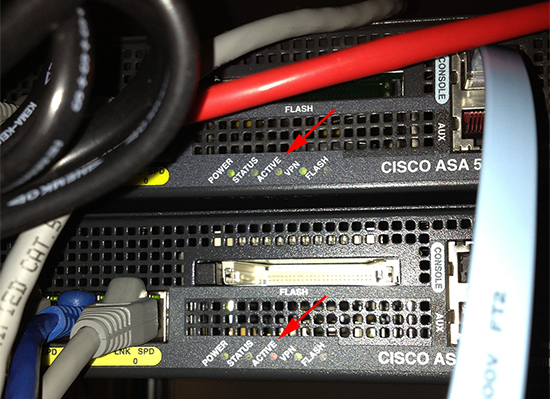
From the rear (Active=Green, Standby=Amber)
The Primary and Secondary firewalls are physical firewalls, the primary will always be the primary, and the secondary will always be the secondary. (Unless you manually change the configuration to force things otherwise!).
The Active firewall will be the firewall that’s passing traffic and in operation, and the Standby firewall is sat waiting to take over, each physical firewall can be either active or standby.
Solution
To get updates from Cisco you need to have a valid support agreement for your firewalls and a Cisco CCO account to log in with. (download link)
In this example, I’m going to upgrade both the firewalls from 8.4(5) to 9.1(1), and the ASDM from version 7.1(1) to 7.1(1)-52. When we start, the primary firewall is the active firewall.
In the past I’ve upgraded from 8.2(5) to 8.4(5), and (here) 8.4(5) to 9.1(1). I’ve never had a problem HOWEVER, DO NOT ATTEMPT an upgrade until you have a good backup of the config.
Backup and Restore a Cisco Firewall
1. First you need to upload the software to the flash memory on BOTH firewalls, you can either connect to the ASA via command line and TFTP them there, or connect to the ASDM and upload them from your PC/Laptop. If you have an AnyConnect XML profile take a backup of that also (I’ve seen them disappear).
Install and Use a TFTP Server
Upload via Command Line
UPLOAD THE OPERATING SYSTEM Petes-ASA> enable Password:********* Petes-ASA#copy tftp flash Address or name of remote host []? 10.0.0.127 Source filename []? asa911-k8.bin Destination filename [disk0]? asa911-k8.bin Accessing tftp://10.1.0.127/asa911-k8.bin.. !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! <<<<Removed lots for the sake of Space>>>> !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! Writing file disk0:asa911-k8.bin... !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!! <<<<Removed lots for the sake of Space>>>> !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! 27260928 bytes copied in 49.250 secs (556345 bytes/sec) UPLOAD THE ASDM SOFTWARE Petes-ASA#copy tftp flash Address or name of remote host []? 10.0.0.127 Source filename []? asdm-711-52.bin Destination filename [disk0]? asdm-711-52.bin Accessing tftp://10.1.0.127/asdm-711-52.bin.. !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! <<<<Removed lots for the sake of Space>>>> !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! Writing file disk0:asdm-711-52.bin... !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!! <<<<Removed lots for the sake of Space>>>> !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! 17790720 bytes copied in 32.200 secs (555960 bytes/sec)
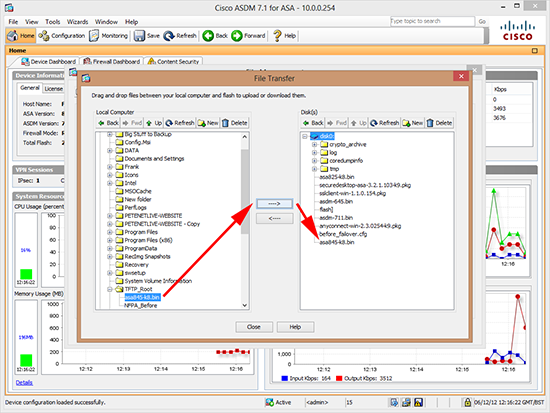
REMEMBER TO DO THIS FOR BOTH FIREWALLS! Note: You can copy the file to the standby firewall’s flash memory, from the primary firewall, using the following syntax (though I usually just swap the console cable over!).
Petes-ASA(config)# failover exec mate copy tftp://10.0.0.115/asa911-k8.bin disk0:/asa911-k8.bin2. On the Primary Active Firewall, set the new OS as the default, below I check to see what file the ASA will boot from, then I change it to the new one, finally I remove the link to the old file. You don’t need to carry out the last step, but I like to leave things tidy.
Petes-ASA# show running-config boot system boot system disk0:/asa845-k8.bin Petes-ASA# configure terminal Petes-ASA(config)# boot system disk0:/asa911-k8.bin Petes-ASA(config)# no boot system disk0:/asa845-k8.bin Petes-ASA# show running-config boot system boot system disk0:/asa911-k8.bin
3. If you are also upgrading the ASDM, you need to set the new one as the default image.
Petes-ASA(config)# asdm image disk0:/asdm-711-52.bin Petes-ASA(config)# show run asdm image asdm image disk0:/asdm-711-52.bin no asdm history enable
4. Save the changes.
Petes-ASA(config)# write mem
Building configuration...
Cryptochecksum: e150e036 036082e0 6d054a3d 1c7fd9fa
16257 bytes copied in 3.350 secs (5419 bytes/sec) [OK]5. Whilst still on the primary active firewall, you need to reboot the secondary standby firewall with the following command:
Petes-ASA(config)# failover reload-standby
YOU MAY SEE A WARNING LIKE THE FOLLOWING - THIS IS OK
************WARNING****WARNING****WARNING********************************
Mate version 9.1(1) is not identical with ours 8.4(5)
************WARNING****WARNING****WARNING********************************
Beginning configuration replication: Sending to mate. End Configuration Replication to mate
Petes-ASA(config)#
6. This may take a little while, remember it has to reboot, and depending on the version you are upgrading to, may need to change some of the config i.e. in this case of upgrading pasr 8.3 (and newer) all the NAT rules need to be changed. You can check to see if it’s back online by issuing a ‘show failover command (whilst still on the primary firewall). You will know when the secondary firewall is up and ready as you will see ‘Secondary – Standby Ready’.
Note: If you can see the status lights on the standby firewall watch for them to be green,green,amber,green,off (ASA5510).
Warning: Due to the limitations of HTML, your output will be formatted a little differently, you will see the output displayed like this, but the text is the same.
Petes-ASA(config)# show failover Failover On Failover unit Primary Failover LAN Interface: failover Management0/0 (up) Unit Poll frequency 1 seconds, holdtime 3 seconds Interface Poll frequency 3 seconds, holdtime 15 seconds Interface Policy 1 Monitored Interfaces 3 of 110 maximum Version: Ours 8.4(5), Mate 9.1(1) Last Failover at: 13:25:54 GMT/BST Dec 6 2012 This host: Primary - Active Active time: 350 (sec) slot 0: ASA5510 hw/sw rev (2.0/8.4(5)) status (Up Sys) Interface outside (123.123.123.123): Normal (Monitored) Interface inside (10.0.0.254): Normal (Monitored) Interface backup (234.234.234.235): Normal (Monitored) slot 1: ASA-SSM-10 hw/sw rev (1.0/CSC SSM 6.2.1599.0) status (Up/Up) Logging port IP: 10.0.0.252/24 CSC SSM, 6.2.1599.0, Up Other host: Secondary - Standby Ready <<<<<< Here we go! Active time: 326 (sec) slot 0: ASA5510 hw/sw rev (2.0/9.1(1)) status (Up Sys) Interface outside (123.123.123.124): Normal (Monitored) Interface inside (10.0.0.249): Normal (Monitored) Interface backup (234.234.234.234): Normal (Monitored) slot 1: ASA-SSM-10 hw/sw rev (1.0/CSC SSM 6.3.1172.0) status (Up/Up) Logging port IP: 10.0.0.248/24 CSC SSM, 6.3.1172.0, Up Stateful Failover Logical Update Statistics Link : failover Management0/0 (up) Stateful Obj xmit xerr rcv rerr General 1709 0 491 49 sys cmd 58 0 58 0 up time 0 0 0 0 RPC services 0 0 0 0 TCP conn 896 0 244 48 UDP conn 280 0 45 1 ARP tbl 474 0 141 0 Xlate_Timeout 0 0 0 0 IPv6 ND tbl 0 0 0 0 VPN IKEv1 SA 0 0 1 0 VPN IKEv1 P2 1 0 1 0 VPN IKEv2 SA 0 0 0 0 VPN IKEv2 P2 0 0 0 0 VPN CTCP upd 0 0 0 0 VPN SDI upd 0 0 0 0 VPN DHCP upd 0 0 0 0 SIP Session 0 0 0 0 Route Session 0 0 0 0 User-Identity 0 0 1 0 Logical Update Queue Information Cur Max Total Recv Q: 0 24 2101 Xmit Q: 0 1 2311 Petes-ASA(config)#
7. Now you need to force a failover to the secondary firewall, (again do this on the primary active firewall).
Petes-ASA(config)# no failover active
Petes-ASA(config)#
Switching to Standby
8. Now reboot the primary firewall and that should boot to its new operating system.
Petes-ASA(config)# reload Proceed with reload? [confirm] {Enter}
9. Once complete, log back in and you can make the primary firewall active once more.
Petes-ASA> Detected an Active mate Beginning configuration replication from mate. Petes-ASA> End configuration replication from mate. Petes-ASA> en Password:********* Petes-ASA# configure terminal **** WARNING **** Configuration Replication is NOT performed from Standby unit to Active unit. Configurations are no longer synchronized. Petes-ASA(config)# failover active Switching to Active
Related Articles, References, Credits, or External Links
Deploy Cisco ASA 55xx in Active / Standby Failover
Cisco ASA5500 Update System and ASDM (From CLI)