KB ID 0000544
Problem
This method provides failover to a redundant ISP link should your primary network connection go down. IT IS NOT going to load balance the traffic across both interfaces. In this example I’ve also got a VPN to a remote site and some port forwarding to contend with as well.
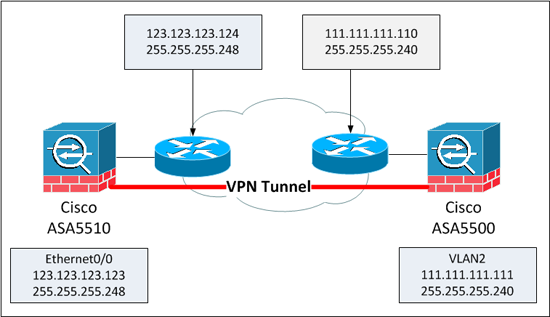
Where we are at the start.
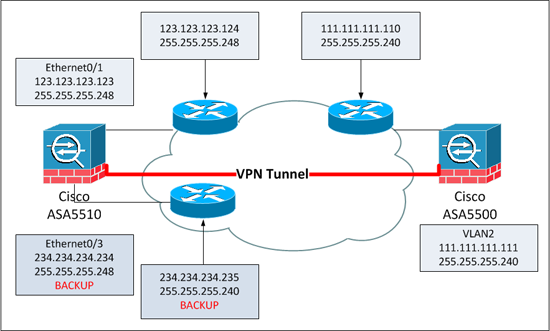
Where we want to be
Solution
Before you go any further the ASA that will have the backup ISP line, needs a Security Plus Licence or it’s not going to work.
Setup Backup ISP Links at the Main Site
1. Log into the firewall and setup the IP address on your backup interface.
PetesASA> PetesASA> en Password: ******* PetesASA# PetesASA# configure terminal PetesASA(config)# interface Ethernet0/3 PetesASA(config-if)# nameif backup PetesASA(config-if)# security-level 0 PetesASA(config-if)# ip address 234.234.234.234 255.255.255.248 PetesASA(config-if)# no shutdown PetesASA(config-if)# exit PetesASA(config)#
2. In a ‘Failed Over’ state your traffic needs to then be NATTED to the backup interface, then setup a new route for the outside interface, and finally one for the backup interface. Note: The new primary route will be “Tracked” based on an SLA we will configure in a minute.
Configure NAT for a firewall running an OS NEWER than 8.3 PetesASA(config)# object network obj_any-01 PetesASA(config-network-object)# subnet 0.0.0.0 0.0.0.0 PetesASA(config-network-object)# nat (inside,backup) dynamic interface Configure NAT for a firewall running an OS OLDER than 8.3 PetesASA(config)# global (backup) 1 interface INFO: backup interface address added to PAT pool Configure the Routes PetesASA(config)# route outside 0.0.0.0 0.0.0.0 123.123.123.124 1 track 1 PetesASA(config)# route backup 0.0.0.0 0.0.0.0 234.234.234.235 2
3. Now we are going to setup a new SLA that maintains connectivity to an IP address (In this case 4.2.2.2 via ICMP, then we are going to tie that SLA to “track 1”, )which you will remember is what keeps the default route on the Primary ISP), if that route fails, it swaps to the backup route.
PetesASA(config)# sla monitor 100 PetesASA(config-sla-monitor)# type echo protocol ipIcmpEcho 4.2.2.2 interface outside PetesASA(config-sla-monitor-echo)# num-packets 3 PetesASA(config-sla-monitor-echo)# frequency 10 PetesASA(config-sla-monitor-echo)# sla monitor schedule 100 life forever start-time now PetesASA(config)# track 1 rtr 100 reachability PetesASA(config)#
4. Any port forwarding getting done on the outside interface needs a mirror entry for the backup interface. and also will need matching ACL’s
PetesASA(config)# static (inside,backup) tcp interface www 10.0.0.5 www netmask 255.255.255.255 PetesASA(config)# static (inside,backup) tcp interface smtp 10.0.0.3 smtp netmask 255.255.255.255 PetesASA(config)# access-list backup permit tcp any interface backup eq www PetesASA(config)# access-list backup permit tcp any interface backup eq smtp PetesASA(config)# access-group backup in interface backup
5. Lets test it, issue a “show route” command, then disconnect your primary ISP then issue another “show route” command and it should have failed over like so;
PetesASA(config)# show route Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area * - candidate default, U - per-user static route, o - ODR P - periodic downloaded static route Gateway of last resort is 123.123.123.124 to network 0.0.0.0 C 234.234.234.0 255.255.255.248 is directly connected, backup C 123.123.123.0 255.255.255.240 is directly connected, outside C 10.0.0.0 255.255.255.0 is directly connected, inside S* 0.0.0.0 0.0.0.0 [1/0] via 123.123.123.124, outside PetesASA(config)# Now Disconnect the Primary line PetesASA(config)# show route Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area * - candidate default, U - per-user static route, o - ODR P - periodic downloaded static route Gateway of last resort is 234.234.234.235 to network 0.0.0.0 C 234.234.234.0 255.255.255.248 is directly connected, backup C 10.0.0.0 255.255.255.0 is directly connected, inside S* 0.0.0.0 0.0.0.0 [254/0] via 234.234.234.235, backup PetesASA(config)#
6. To enable this firewall to accept the existing VPN on its backup interface, you need to add the backup interface to that cryptomap (issue a show run crypto if your unsure). Then you need to enable ISAKMP on the backup Interface.
PetesASA(config)# crypto map outside_map interface backup PetesASA(config)# crypto isakmp enable backup
7. Save the changes with a write mem command.
PetesASA(config)# wr mem
Building configuration...
Cryptochecksum: 91d190ba 2a3eb9c4 244d8c88 0da54e36
10220 bytes copied in 3.740 secs (3406 bytes/sec)
[OK]
PetesASA(config)#Change the ASA at the Remote VPN Site
1. Connect to the firewall at the remote site, find the cryptomap that points to the main site (show run crypto). find the one that pointing to the IP at the main site, then add the new IP address as an alternate peer address.
RemoteSite(config)# crypto map outside_map 2 set peer 123.123.123.123 234.234.234.2342. Then create a tunnel group for the new backup address with the same shared secret as tunnel group to the primary IP.
RemoteSite(config)# tunnel-group 234.234.234.234 type ipsec-l2l RemoteSite(config)# tunnel-group 234.234.234.234 ipsec-attributes RemoteSite(config-tunnel-ipsec)# pre-shared-key 123456789
3. Save the changes with a “write mem” command.
RemoteSite(config-tunnel-ipsec)#write mem
Building configuration...
Cryptochecksum: 7a455ca7 3b637757 cd40aa82 7f3a22d8
7842 bytes copied in 1.530 secs (7842 bytes/sec)
[OK]
RemoteSite(config-tunnel-ipsec)#To test the VPN fails over, at the remote site issue a “show cry isa” command, then get someone at the primary site to disconnect the primary ISP, wait a few seconds and then re-issue a “show cry isa” command and it should have flipped over.
Failover-FWall# show cry isa Active SA: 1 Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey) Total IKE SA: 1 1 IKE Peer: 123.123.123.123 Type : L2L Role : responder Rekey : no State : MM_ACTIVE Now Disconnect the Primary line at the Main site Failover-FWall# show cry isa Active SA: 1 Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey) Total IKE SA: 1 1 IKE Peer: 234.234.234.234 Type : L2L Role : responder Rekey : no State : MM_ACTIVE
Related Articles, References, Credits, or External Links
Original article written 12/12/11