KB ID 0000312
Problem
DNS resolves intermittently, and your Exchange outbound mail may fail and give the following error:
The following recipient(s) could not be reached: user@domain.com on (Date Time). There was a SMTP communication problem with the recipient’s email server. Please contact your system administrator. <(Domain.com) #5.5.0 smtp;550-Domain does not recognize your computer (xx.xx.xxx.xxx) as connecting from an Domainconnection. If this is in error, please contact technical support.>
Seen on Server 2003 and Server 2008 R2 DNS Servers, caused by Extension Mechanisms for DNS (EDNS0), this allows the use of UDP packets that are larger than 512 bytes. Some firewall systems do not like this and will drop the traffic.
Solution
Solution 1
The best way to cure the problem is to ensure any upstream devices either understand EDNS, or allow packets over 512 bytes. Check with your firewall vendor.
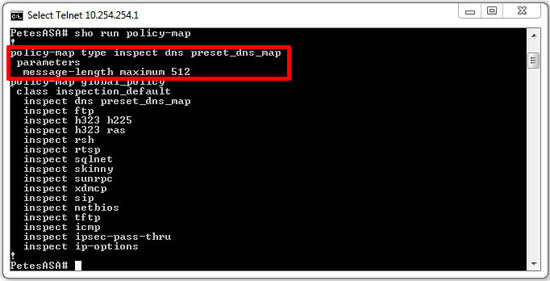
On a Cisco ASA, the default inspection map is defined as follows (maximum of 512 bytes), this was defined in RFC 1035 that’s why it’s there.
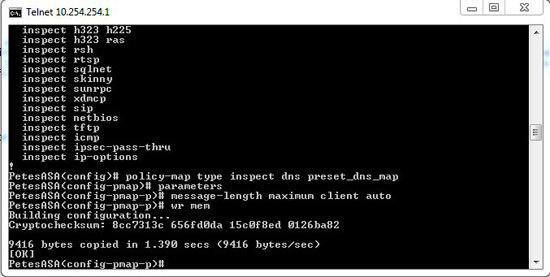
This value can be increased to 65535, however the higher the number the more susceptible you are to a DNS amplification attack, most blogs and forums I’ve read suggest setting a value of 4096 (though I’d suggest 1024). EDNS is fully supported on ASA firewalls running 8.2(2) and above. If you are running 8.2(2) or above you can simply use the following command:
Note: For Cisco PIX Version 6 and lower use the following:
?
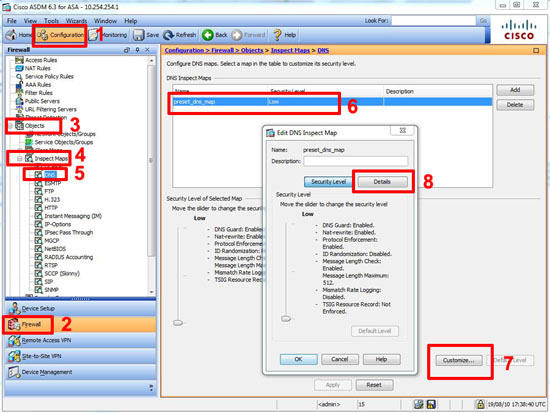
To raise the value in the ASDM
1. Connect to the ASDM > Configuration > Firewall >Objects >Inspection Maps > DNS > default_dns_map > Customise > Details.
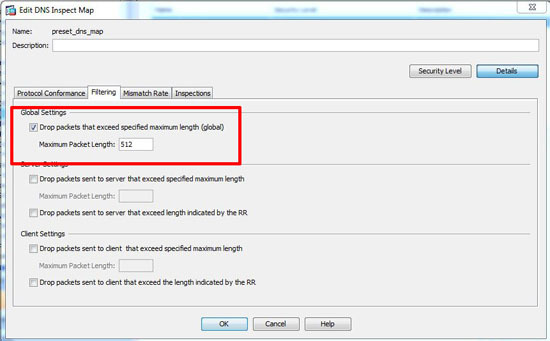
2. Under global settings change as required > OK > Apply > File > Save running configuration to flash.
Solution 2
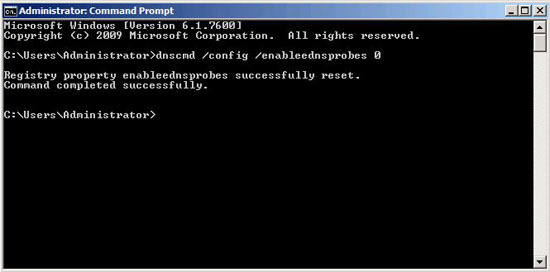
Disable EDNS on the DNS Server from command (No restart of DNS service is required).
1. On the Server Start > Run > cmd {enter}
2. Execute the following command:
Note: dnscmd is NOT installed by default on Server 2003 you need to install it from the support tools.
Solution 3
Disable EDNS via the registry (Requires a restart of the DNS Server Service).
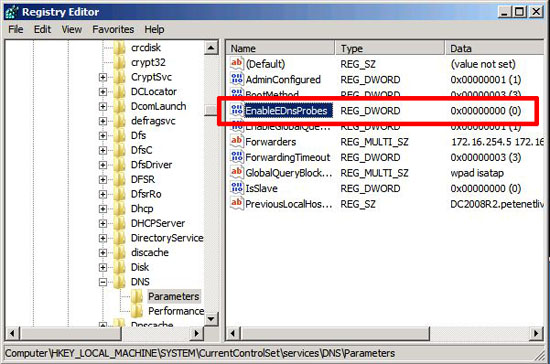
1. Start > Run > regedit {enter}
2. Navigate to HKEY_LOCAL_MACHINESYSTEMCurrentControlSetservicesDNSParameters.
3. Create or Modify the REG_DWORD value EnableEDNSProbes and set it to 0 (Decimal).
Or
Import this registry key, or download and merge this one.
Windows Registry Editor Version 5.00 <p>[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetservicesDNSParameters]<br /> "EnableEDnsProbes"=dword:00000000
Related Articles, References, Credits, or External Links
NA