Audit GPO Changes KB ID 0001920
Problem
If you are reading this your either replanning ahead (bravo!) or there’s been an incident that you are concerned about. If that is the case its important to remember that “you cannot audit retrospectively”*
*Note: you can find out when GPOs were altered, but not by whom, with some simple PowerShell i.e. Get-GPO -All | Select-Object DisplayName, ModificationTime
Group Policies are your base level settings for security enforcement and compliance, its important to be aware of any changes (or attempt to change) those policies. for the following reasons.
Security Assurance: Both to limit internal threats, and to detect unauthorised changes.
Change Tracking and Accountability: Some changes are legitimate, and need to be tracked, when they were implemented, and who implemented them.
Root Cause Analysis: If things suddenly ‘go wrong’ as a result of a GPO change, tracking that change is important, to find that root cause and hopefully avoid a reoccurrence.
Change Management and Policy Control: Encourages correct change control procedure, and discourages changing policies “on the fly”.
Solution : Audit GPO Changes
There are essentially THREE places that you need to consider enabling auditing on, those are.
- Audit Directory Service Change.
- Audit Policy Change.
- Audit Authentication Policy Change.
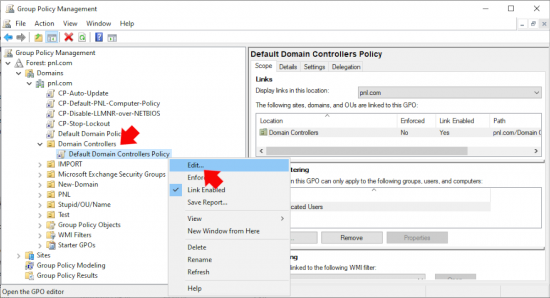
On a domain controller locate and edit ‘The Default Domain Controllers Policy” Or create a new GPO and link it to the domain controllers OU.
Then navigate to.
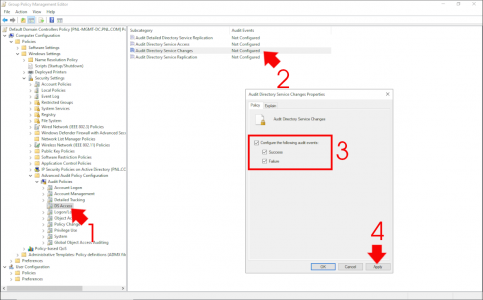
Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies > DS Access
Enable the policy and set it to success and failure.
Then navigate to.
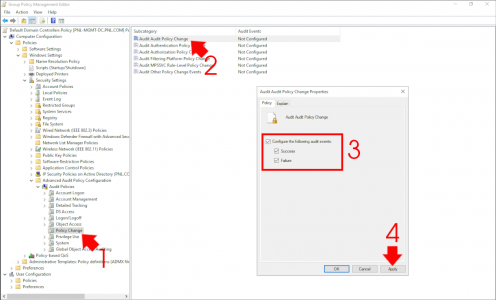
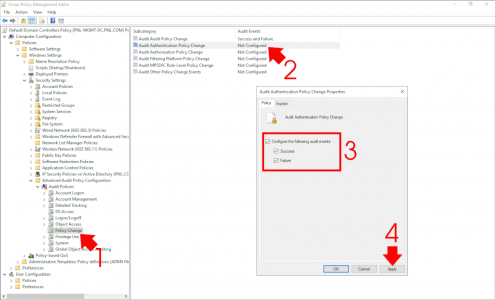
Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies > Policy Change
Locate the following policy Audit Audit Policy Change. Enable the policy and set it for success and failure.
Locate the following policy Audit Authentication Policy Change. Enable the policy and set it for success and failure.
Audit GPO Changes : Viewing Audited Events
Now events are being audited, to see the audited events, you need to look in the Event Viewers of the domain controllers.
| Event ID | Source | Description |
| 5136 | Directory Services | A directory object was modified (includes GPO changes). |
| 5137 | Directory Services | A directory object was created. |
| 5141 | Directory Services | A directory object was deleted. |
| 4719 | Security | System audit policy was changed. |
To specifically track GPO changes, look at Event ID 5136 with a CN=Policies object path. It includes:
- Who made the change (Subject: field)
- When it occurred
- What attribute was changed
Audit GPO Changes : With AGPM (Advance Group Policy Management)
To get AGPM you need access to the Microsoft Optimization Pack, it comes as two executables, the client and the server software, install the server software (can be installed on a DC).
Note: Support for AGPM (SP4) will end 14-04-26
During installation you will be asked for a location for it to store its backups in and a port on which it can be accesses (default is TCP 4600). Then deploy the client software to the client machines (annoyingly it’s an .exe and not an .msi).
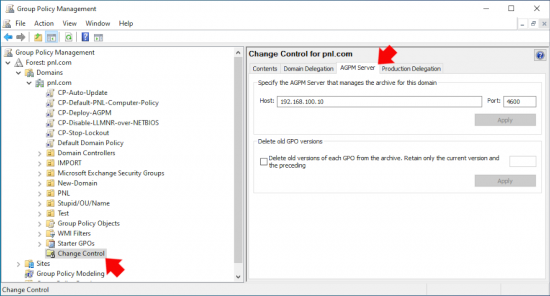
Once deployed open the group management console on your DC and locate ‘Change Control’ then in the right hand pane select the AGPM server (if you cannot see it right click change control and add it).
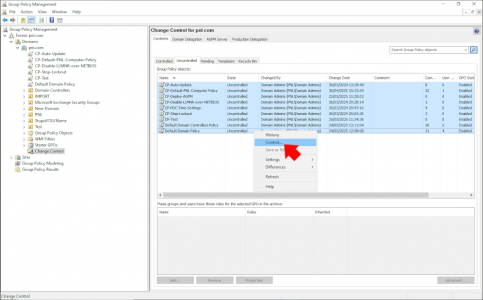
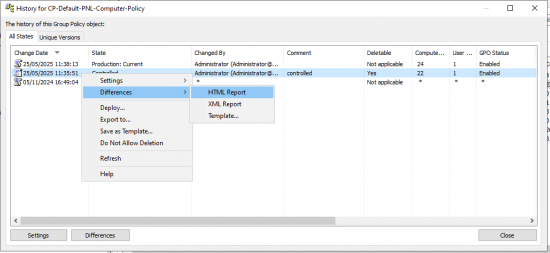
To make sure a GPO is audited you need to change its status to controlled. (they will all be listed as uncontrolled initially).
Then if GPOs are changed you can track the time of, and detail of that change.
Related Articles, References, Credits, or External Links
Advanced Group Policy Management