KB ID 0001175
Problem
I always forget the syntax for this, and I’ve been meaning to publish this for a while so here you go. If you have AAA setup and people can’t log in, then the ability to test authentication against a user’s username and password is a good troubleshooting step!
Usually I’m on a Cisco ASA but I’ll tag on the syntax for IOS as well.
Solution
Cisco ASA Test AAA Authentication From Command Line
You will need to know the server group and the server you are going to query, below the ASA is using LDAP, but the process is the same for RADIUS, Kerberos, TACACS+, etc.
Petes-ASA# show run | begin aaa
aaa-server TEST-LDAP-SERVER protocol ldap
aaa-server TEST-LDAP-SERVER (inside) host 192.168.110.10
ldap-base-dn dc=TEST,dc=net
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password *****
ldap-login-dn cn=asa,OU=Users,OU=Test-Corp,dc=TEST,dc=net
server-type auto-detect
To test your user, (username: ttester password: Password123);
Petes-ASA# test aaa-server authentication TEST-LDAP-SERVER host 192.168.110.10 username ttester password Password123
INFO: Attempting Authentication test to IP address (timeout: 12 seconds)
INFO: Authentication Successful
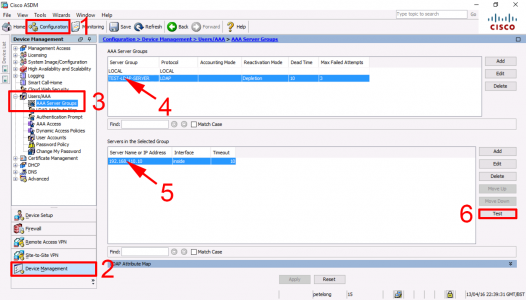
Cisco ASA Test AAA Authentication From ASDM
Log into the ADSM > Configuration > Device Management > Users/AAA > Select the Server Group > Select the Server > Test.
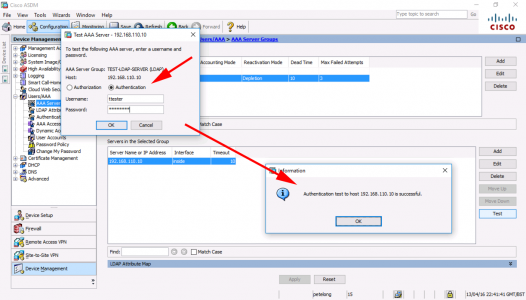
Select ‘Authentication’ > Enter Username/Password > OK.
Cisco IOS Test AAA Authentication From Command Line
As above, you need to know which server group, and server, you are going to test authentication against;
Petes-Router#show run aaa
!
aaa authentication login default local
aaa authorization exec default local
!
aaa group server radius RADIUS-GROUP
server-private 192.168.110.10 key 666999
!
aaa new-model
aaa session-id common
!
Text
Petes-Router#test aaa group RADIUS-GROUP tester Password123 legacy Attempting authentication test to server-group RADIUS-GROUP using radius User was successfully authenticated. OR Petes-Router#test aaa group RADIUS-GROUP tester Password123 new-code User successfully authenticated USER ATTRIBUTES Framed-Protocol 0 1 [PPP] service-type 0 2 [Framed] noescape 0 True autocmd 0 " ppp negotiate" Petes-Router#
Related Articles, References, Credits, or External Links
Cisco ASA – AnyConnect Authentication via LDAP and Domain User Groups
Windows Server 2012 – Configure RADIUS for Cisco ASA 5500 Authentication
Windows Server 2008 R2 – Configure RADIUS for Cisco ASA 5500 Authentication
Cisco ASA 5500 Client VPN Access Via Kerberos (From CLI)
Set Cisco ASA for Kerberos Authentication


29/10/2016
Thanks Pete. Would you be able to post the entire config please? I’m trying to learn RADIUS with a Server 2008 R2 computer and a Cisco AP 1142N. Having a fun time trying to get my head around it.
Matt.
29/10/2016
Hi Matt
Thanks, it’s covered in another article, do a search (top right) for Server 2008 RADIUS.
Pete
31/10/2016
Thanks Pete, will do.
31/08/2021
I have been trying to make this work for the last 2 days but the authentication fails because ISE says 15024 “PAP is not allowed”. I dont see where there is an option to select the protocot to use.
11/01/2022
Better late than never!
It can be found under “Policy -> Policy Elements -> Results”, Left menu “Authentication -> Allowed Protocols”. Here are the Allowed profiles configured, that are bound to the authentication part of an policy set. by default PAP is disabled.