KB ID 0001143
Problem
Getting this article to completion has been a bit of a journey! This is the final post that will stitch together all the others I’ve posted over the last couple of weeks, that will enable you to publish your RemoteApps with ‘Remote Desktop Web Access’, and have that service presented securely from your DMZ. I’ll be using Active Directory Federation Services, (you don’t have to, but it’s more secure than simply using ‘pass-though’ security).
Solution
Prerequisites
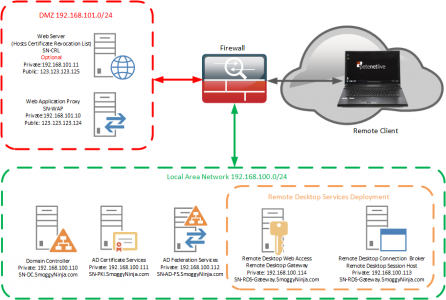
Topology: Simply getting your ‘ducks in a row’ will take a lot longer than actually deploying the service. Here is the topology that I’m going to deploy;
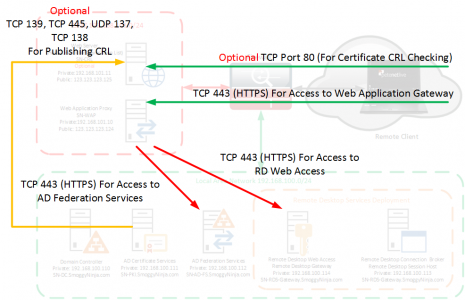
Firewall Rules: You will see I’ve labelled all the Certificate/CRL rules as optional, this is because you would only need them if you were using self signed certificates. In this example that’s what I am doing, this means that all my remote clients need the root certificate installing on them, so for production I suggest you purchase a publicly signed wildcard certificate for simplicity.
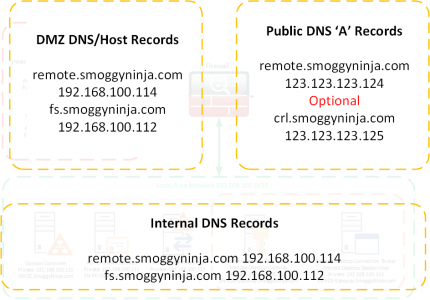
DNS Requirements: For your internal domain and the DMZ it’s simple enough but your external clients will need to be able to resolve your public URL (and the URL of your CRL is used).
Certificate Services (Optional): If you want to deploy self signed wildcard certificates you will need a PKI environment and a published CRL. See the following article;
Windows Certificate Services – Setting up a CRL
Once setup you will need to generate a self signed wildcard certificate. See the following article;
Certificate Services – Create a ‘Wildcard Certificate’
Active Directory Directory Services: You need to have your ADFS farm deployed and ready to add your relying trust to. See the following article;
Deploy Active Directory Federation Services
Web Application Proxy: The Role needs installing ready to have the publishing rule added for Remote Desktop Web Access. See the following article;
Deploying Windows ‘Web Application Proxy’
MAKE SURE: You have ran Windows updates on the WAP server, there are a number of bugs that have been fixed, ensure you have at least KB2975719, and in addition you need to have KB2983037 Hotfix installed.
Step 1: Add A Relying Trust To Active Directory Federation Services For Web Application Proxy
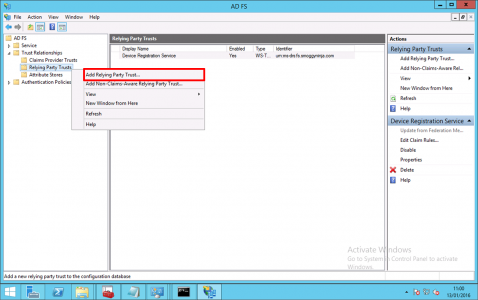
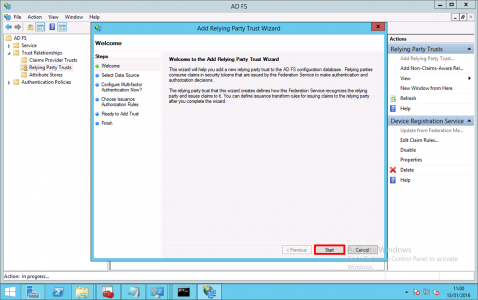
On your ADFS Server > Administrative Tools > AD FS Management > AD FS > Trust Relationships > Relying Party Trusts > Add Relying Party Trust.
Next.
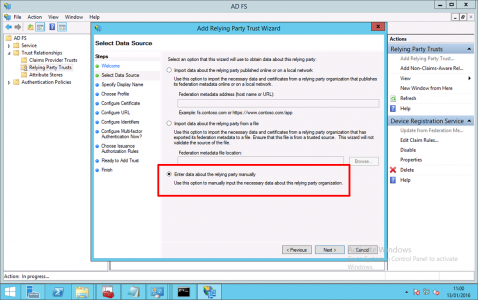
Enter data about relying party trust manually > Next.
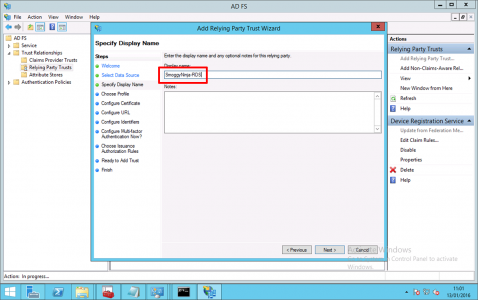
Give the trust a name > Next.
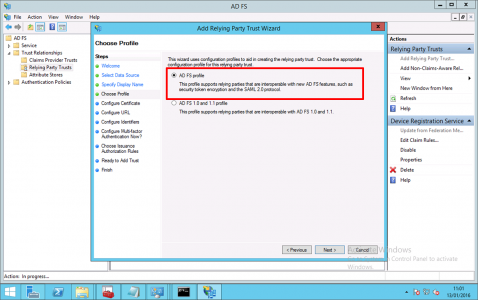
AD FS Profile > Next.
Next.
Next.
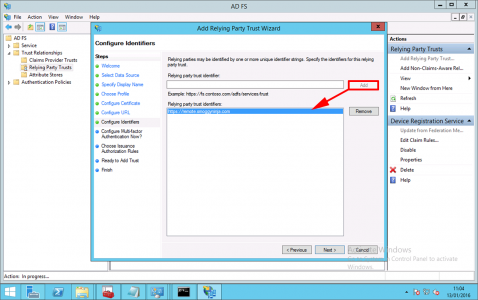
As an identifier, add in the UEL to access Remote Desktop Web Access > Next.
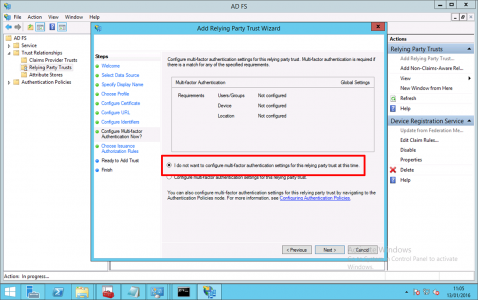
I do not want to configure multi-factor authentication settings for this relying party trust at this time > Next.
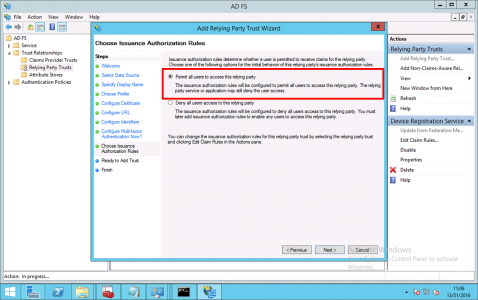
Permit all users to use this relying party > Next.
Next.
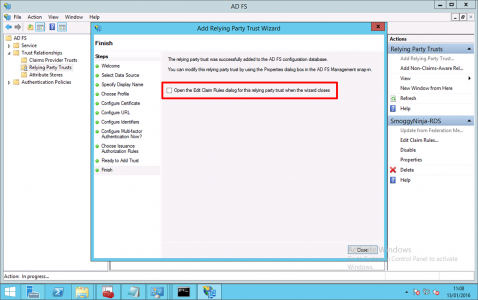
Untick “Open Edit Claim Rules dialog for this relying party trust when the wizard closes’ > Close.
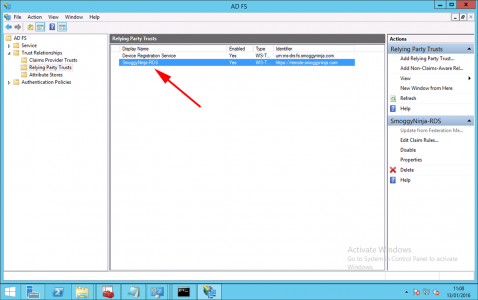
You should see your relying part trust listed, take note of its name.
Step 2: Configure Web Application Proxy To Publish Remote Desktop Web Access
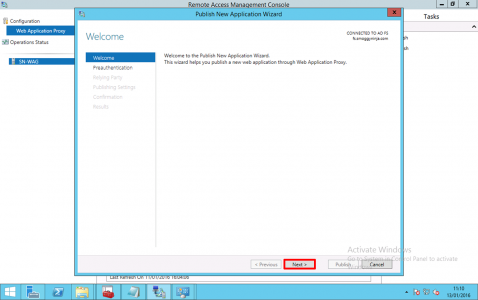
On the WAP Server > Administrative Tools > Remote Access Management > Select the Server > Publish.
Next.
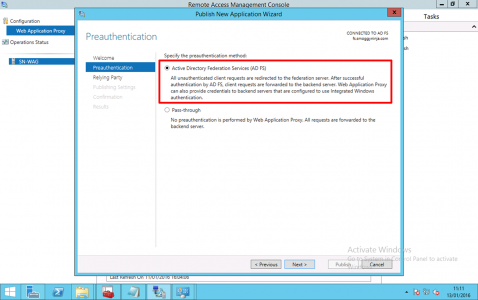
Select ‘Active Directory Federation Services (AD FS) > Next.
Note: As mentioned above, you can choose ‘pass-through’, then author authentication is done on the internal RD Web Access server (which is less secure).
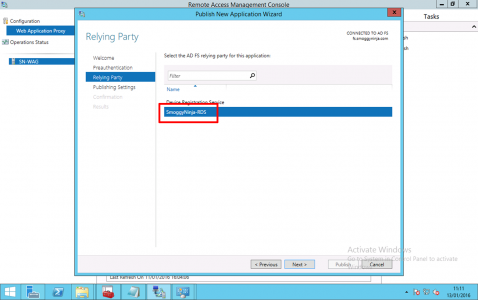
Select the relying trust you created above > Next. (If it’s not there check https is open, and you can resolve the AD FS service name) > Next.
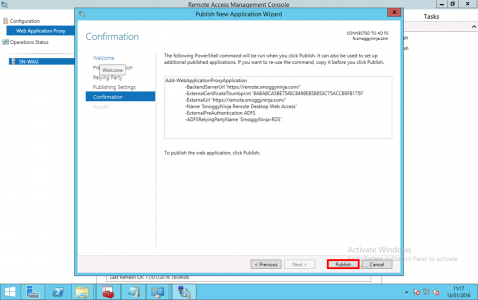
Give the publishing rule a name, and enter the URL the service will be published on, (this is usually the same inside and outside but does not have to be) > Select your wildcard certificate > Next.
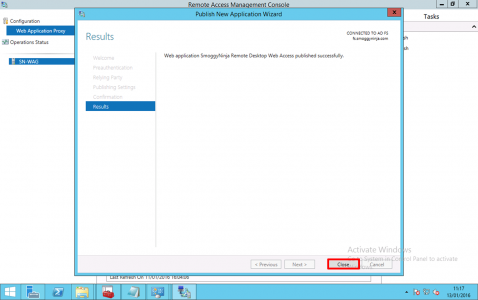
Publish.
Close
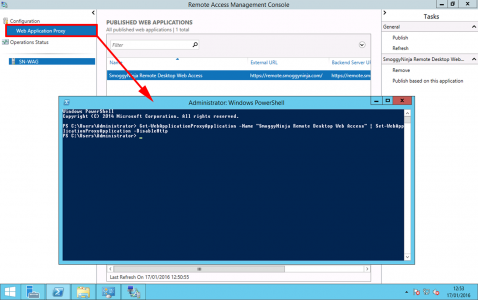
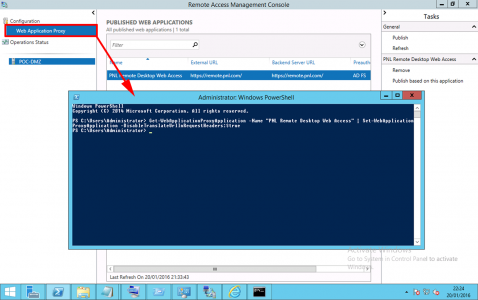
In PowerShell execute the following command;
Get-WebApplicationProxyApplication -Name “SmoggyNinja Remote Desktop Web Access” | Set-WebApplicationProxyApplication -DisableHttp
Then the following command;
Get-WebApplicationProxyApplication -Name “SmoggyNinja Remote Desktop Web Access” | Set-WebApplicationProxyApplication -DisableTranslateUrlInRequestHeaders:$true
Note: You only actually need this command if you’re using different URLs but let’s stick with a script that works.
Step 3: Additional Works.
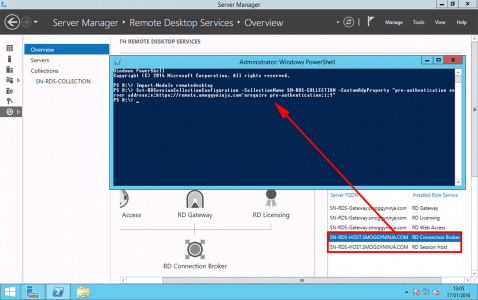
On the Remote Desktop Session Host Server run the following commands;
Import-Module Remote Desktop
Set-RDSessionCollectionConfiguration -CollectionName SN-RDS-COLLECTION -CustomRdpProperty “pre-authentication server address:s:https://remote.smoggyninja.com`nrequire pre-authentication:i:1″
Related Articles, References, Credits, or External Links
NA


04/04/2017
Hiya, great article thanks. What about WAP not supporting UDP though? I read that 2012 R2 RDS needs UDP and without it, there is a significant performance hit.
04/04/2017
It’s still not supported in 2016 either, and no word from M$ on the subject 🙁
Pete
13/02/2023
“The web client does support using Azure AD Application Proxy but does not support Web Application Proxy at all.”
https://learn.microsoft.com/en-us/windows-server/remote/remote-desktop-services/clients/remote-desktop-web-client-admin