Port Translation
KB ID 0001087
Problem
Note: This is for Cisco ASA 5500, 5500-x, and Cisco Firepower devices running ASA Code.
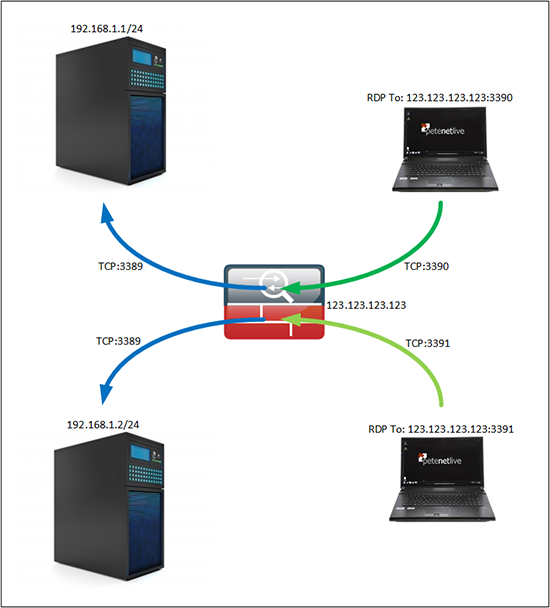
A very long time ago I wrote an article about how to port forward from a public IP address to multiple servers for RDP. Basically you would connect to the firewall using various different ports, and the firewall would change the port to the correct one for RDP (TCP port 3389, unless you changed it on the machine). Then send it to the correct server, so you could manage multiple servers from the same public IP.
Now that was so long ago it was before the version 8.3 NAT changes. This week I was working on a problem where every change I made that had to be tested meant I had to swap VPNs, and reconnect to servers and test comms. This was getting a bit time consuming so I needed a public server to jump on for testing. I didn’t want to expose RDP to my server, so I planned to use a different port and translate that port on the firewall. But how to do that with modern ASA code?
Solution
1. Create the objects and NAT Rules;
Petes-ASA> enable Password: ******** Petes-ASA# configure terminal Petes-ASA(config)# object network Internal_RDP_Server-1 Petes-ASA(config-network-object)# host 192.168.1.1 Petes-ASA(config-network-object)# nat (inside,outside) static interface service tcp 3389 3390 Petes-ASA(config-network-object)# exit Petes-ASA(config)# object network Internal_RDP_Server-2 Petes-ASA(config-network-object)# host 192.168.1.2 Petes-ASA(config-network-object)# nat (inside,outside) static interface service tcp 3389 3391 Petes-ASA(config-network-object)# exit
Whole Code
object network Internal_RDP_Server-1 host 192.168.1.1 nat (inside,outside) static interface service tcp 3389 3390 object network Internal_RDP_Server-2 host 192.168.1.2 nat (inside,outside) static interface service tcp 3389 3391 ! access-list inbound permit tcp any object Internal_RDP_Server-1 eq 3389 access-list inbound permit tcp any object Internal_RDP_Server-2 eq 3389 ! access-group inbound in interface outside
OLD (Pre version 8.3) Port Forwarding to a Different port
So (as above), I’ll connect to the first server on port 3390, and the second on port 3391.
Petes-ASA> enable Password: ********* Petes-ASA#configure terminal Petes-ASA(config)# access-list inbound extended permit tcp any interface outside eq 3390 Petes-ASA(config)#access-list inbound extended permit tcp any interface outside eq 3391
Then Port Forward AND TRANSLATE those ports to the correct internal servers.
Petes-ASA(config)# static (inside,outside) tcp interface 3390 192.168.1.1 3389 netmask 255.255.255.255 Petes-ASA(config)# static (inside,outside) tcp interface 3391 192.168.1.2 3389 netmask 255.255.255.255
Related Articles, References, Credits, or External Links
NA