ESX Certificate KB ID 0000974
Problem
ESXi comes with a self-signed certificate, and for most people that’s fine, but some clients want to have a ‘Trusted’ certificate on theirs, and have their own PKI infrastructure for issuing them.
Below I will generate a new certificate for my ESXi server using the Active Directory Certificate Services role on Windows Server 2012. Then replace the self-signed certificate with my new one.
WARNING: This is for ESX servers that are NOT managed by vCenter – IF you want to carry out this procedure on a manged ESX then remove it from the vCenter update the certificate and then add it back into the inventory (and make sure it’s not running vCenter!)
Solution : Replace ESX Certificate
Generating a ESX Certificate Request
1. Before we start there are a couple of hoops to jump through, and a Windows machine (it does not matter which one), install the following TWO pieces of software.
Microsoft Visual C++ 2008 Redistributable Package (x86) and Shining Light Productions installer for OpenSSL x86 version 0.98r (or later)
Accept all the defaults and it should install to C:\Program Files (x86)\OpenSSL-Win32\bin go there and make a backup of the openssl.cfg file.
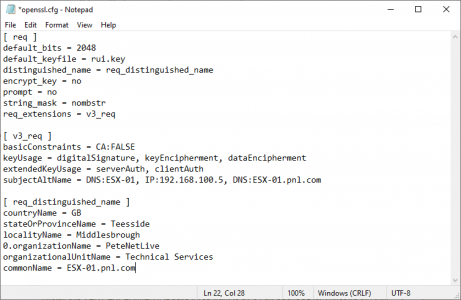
2. Open the original openssl.cfg file and delete everything out of it, then paste in the following text, replace the values in red with your own, and save the file.
[ req ] default_bits = 2048 default_keyfile = rui.key distinguished_name = req_distinguished_name encrypt_key = no prompt = no string_mask = nombstr req_extensions = v3_req [ v3_req ] basicConstraints = CA:FALSE keyUsage = digitalSignature, keyEncipherment, dataEncipherment extendedKeyUsage = serverAuth, clientAuth subjectAltName = DNS:ESX-01, IP:192.168.100.5, DNS:ESX-01.pnl.com [ req_distinguished_name ] countryName = GB stateOrProvinceName = Teesside localityName = Middlesbrough 0.organizationName = PeteNetLive organizationalUnitName = Technical Services commonName = ESX-01.pnl.com
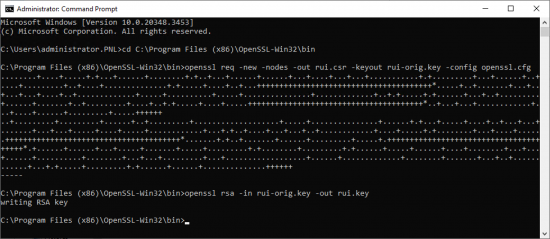
3. Open a command window and execute the following three commands.
cd C:\Program Files (x86)\OpenSSL-Win32\bin openssl req -new -nodes -out rui.csr -keyout rui-orig.key -config openssl.cfg openssl rsa -in rui-orig.key -out rui.key
You will notice rui.csr has been created in the bin directory this is the file you need to request your certificate, if you open the file with Notepad you can copy the text.
Submit the ESX Certificate Request and Get an ESX Certificate From a Windows CA
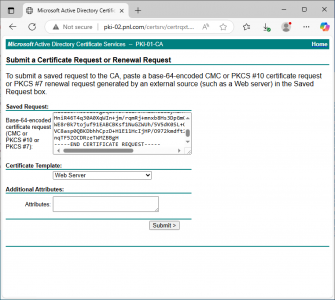
Open the web console of your certificate services server (it needs to be running the Certification Authority Web Enrolment role). The URL is usually http://{servers IP or Name}/Certsrv. Select ‘Request a certificate’ > Advanced certificate request., if you open the file with Notepad, you can copy the text.
Paste in the text from your csr file (with no extra spaces!). Set the Certificate Template to ‘Web Server’ (the default lifetime for the Web Server template is 2 years. If you require longer, I suggest you clone the Web Server Template, change the lifetime and republish it in Active Directory Certificate Services).
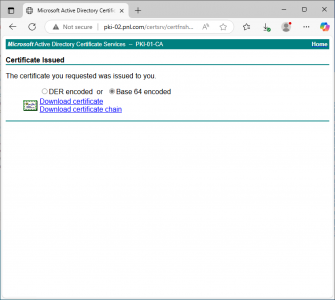
Base 64 encoded> Download certificate.
Save the file as rui.cer and put it in the bin directory.
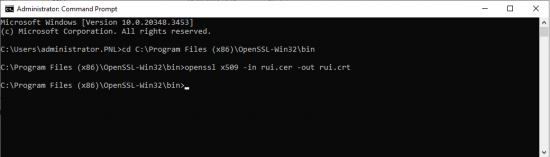
ESX needs the certificate to be in x509 format, so open a command window and execute the following commands.
cd C:\Program Files (x86)\OpenSSL-Win32\bin openssl x509 -in rui.cer -out rui.crt
11. Enable SSH on your ESX Host.
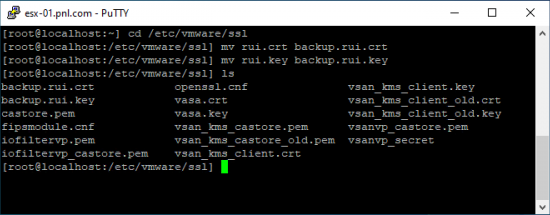
Connect to the ESX host via SSH, and make a backup of the current keys (just in case).
cd /etc/vmware/ssl mv rui.crt backup.rui.crt mv rui.key backup.rui.key
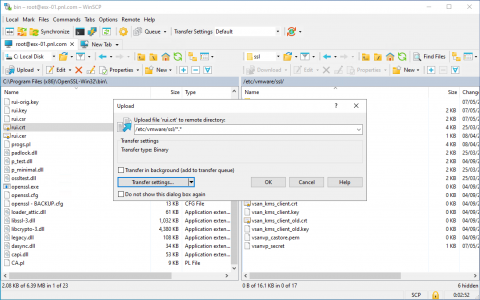
Using WinSCP copy the rui.crt and the rui.key files from the bin directory, to the /etc/vmware/ssl directory on your ESX host. WARNING: Set the copy type to ‘Text’ or ASCII or you may get some strange results.
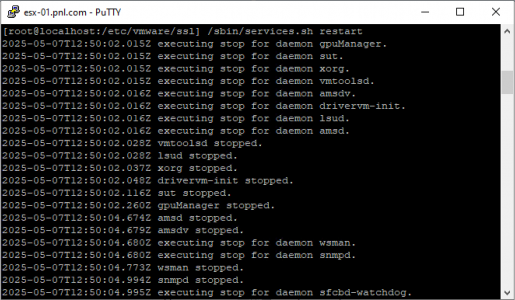
Then either restart the management agents, or from your SSH session execute the following command.
/sbin/services.sh restart
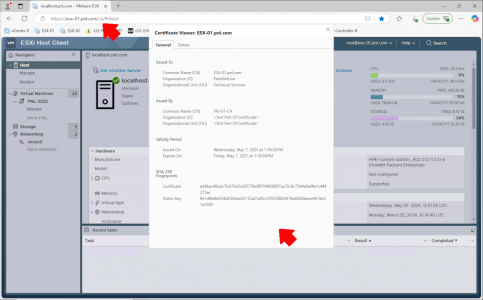
The simplest way to check is browse to the FQDN or your ESX host (the same name you used as the common name in step 2), and take a look at the certificate.
Related Articles, References, Credits, or External Links
Configuring CA signed certificates for ESXi hosts