KB ID 0000743
Problem
This got asked on Experts Exchange today, the poster specifically asked for an ASDM solution, so here goes. However I will also do the commands as well.
Solution
Block an IP via ASDM
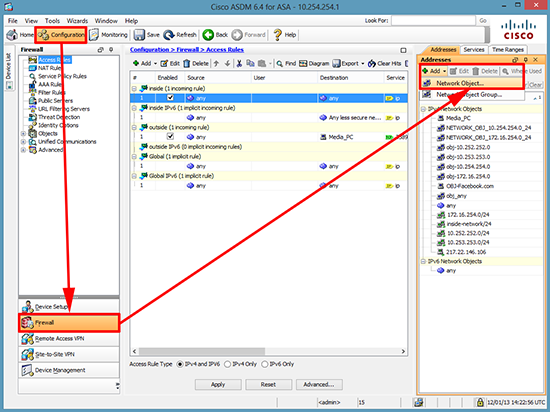
1. Connect to the ASDM > Configuration > Firewall > Add ‘Network Object’.
Note: You could create a Network Object Group, then add a Network Object to that group. This is handy if there are liable to be more IP addresses you want to block in the future. In that case you would then simply add the new Network Objects to the existing group.
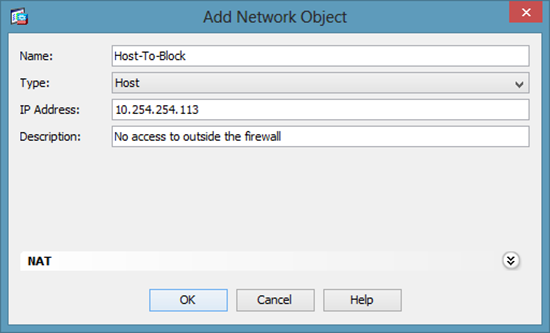
2. Give the host a name, set its type to ‘Host’ > Enter the IP > The description is not mandatory.
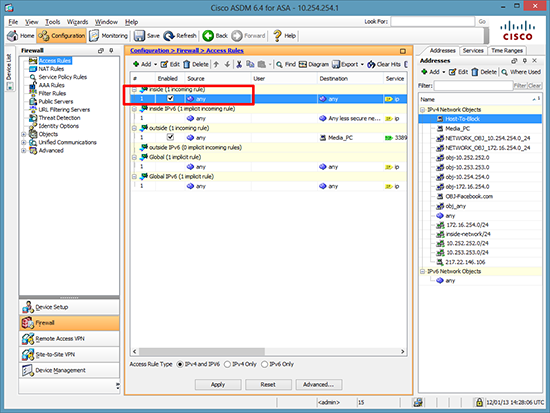
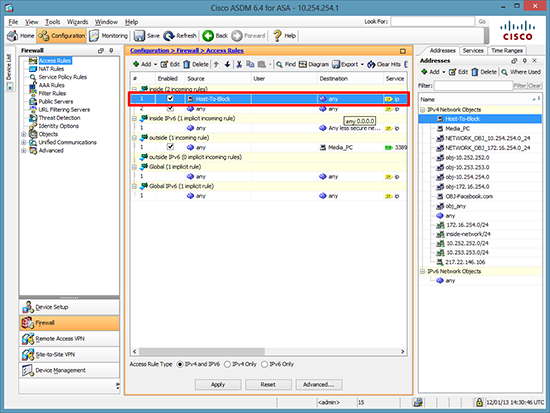
3. Locate the rules that are applied to the inside interface (incoming), select the first one.
Note: I refer to these as ‘Outbound’ rules, they apply to traffic flowing IN through the INSIDE interface.
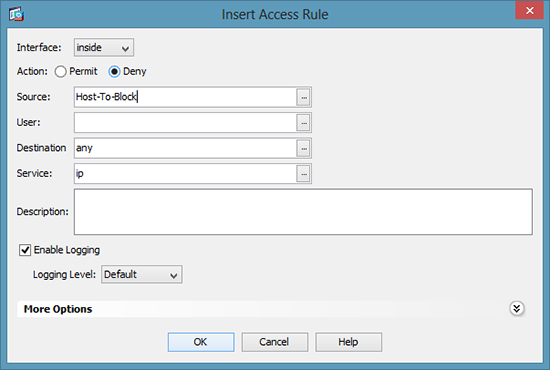
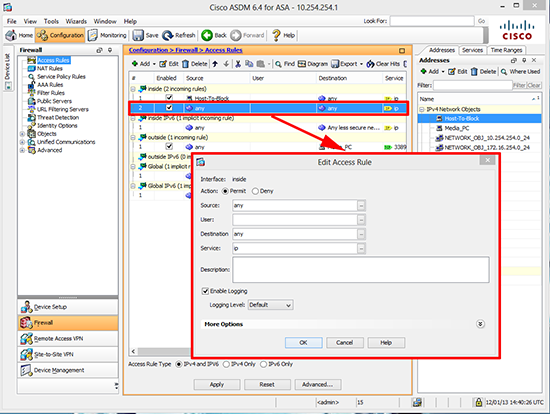
4. Add a new access rule > Set to Deny > Select the source as the host (or group) you have just created > OK.
5. Make sure your new rule is at the TOP > Click Apply.
6. Warning: Below your ‘deny’ rule you need to ‘allow’ the traffic that should be allowed, or all other traffic will get blocked.
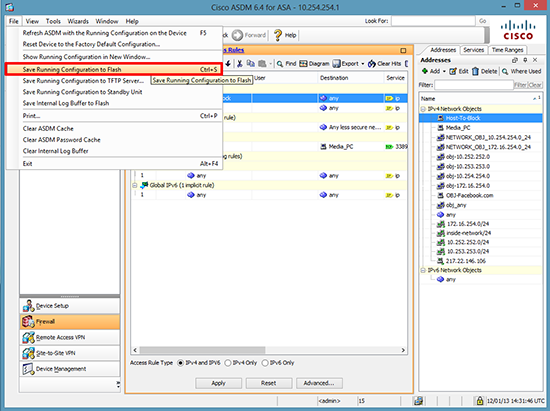
7. Save the changes to memory > File > Save Running Configuration to Flash.
Block an IP via Command
Note: This assumes you do NOT have an outbound ACL (Issue a show acess-group command to find out), if you do it will say access-group {name} in interface inside, Simply replace the word outbound below for the name of yours and DONT issue the command that starts access-group.
User Access Verification
Password: Type help or ‘?’ for a list of available commands. PetesASA> enable Password: ******** PetesASA# configure terminal PetesASA# access-list line 1 outbound deny ip host 10.254.254.113 any PetesASA# access-list line 2 outbound permit ip any any PetesASA# access-group outbound in interface inside PetesASA(config)# write mem Building configuration… Cryptochecksum: b984ffbc dd77cdbf f2cd8d86 0b8f3f96
3965 bytes copied in 1.490 secs (3965 bytes/sec) [OK]
Related Articles, References, Credits, or External Links
NA