KB ID 0000545
Problem
To access VMware View though a firewall you need the following ports to be open;
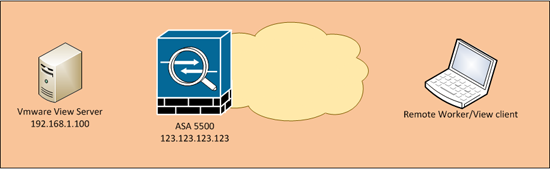
In the following example I’m using 192.168.1.100 as the internal IP address of the View Server and the public IP address of the firewall is 123.123.123.123.
Which solution you use, depends on weather you are allowing access via a dedicated public IP that you will assign to the VMware View server, or if you do not have a spare public IP, you will need to use port forwarding.
Option 1 – You have a public IP that you want to assign to the VMware View Server
Option 2 – You want to use Port Forwarding (And your ASA is pre version 8.3)
Option 3 – You want to use Port Forwarding (And your ASA is version 8.3 or newer)
Solution
Option 1 – You have a public IP that you want to assign to the VMware View Server
As I’m using 123.123.123.123 on the outside of my ASA I’m going to use another public IP address for the VMware View server (123.123.123.124) and I will statically map that to its internal IP address. Then I allow the ports to that IP address, and finally apply the access-list (ACL) that I’ve used to the outside interface (where the VMware View traffic will be coming from).
Warning: The last command (starting access-group, applies the access-list ‘inbound’ in the inbound direction on the outside interface, you may already have an access-list applied to this interface (the ‘show run access-group’ command will tell you) If you do have another ACL simply substitute the name of yours for the work inbound in my example below).
Option 2 – You want to use Port Forwarding (And your ASA is pre version 8.3)
Below I’m creating a static PAT entry for all the ports required, then allowing the traffic with an access-list, and finally applying the access-list (ACL) that I’ve used to the outside interface (where the VMware View traffic will be coming from)
Warning: The last command (starting access-group, applies the access-list ‘inbound’ in the inbound direction on the outside interface, you may already have an access-list applied to this interface (the ‘show run access-group’ command will tell you) If you do have another ACL simply substitute the name of yours for the work inbound in my example below).
Note: If you port forward https on the outside interface, as I’m doing here, you will not be able to access the ASDM from outside – unless you put it on another port. The following two commands would change the ASDM to port 2345 for example:
no http server enable
http server enable 2345
Option 3 – You want to use Port Forwarding (And your ASA is version 8.3 or newer)
Below I’m creating a network object for all the ports required and statically NATTING the ports required to them, then I’m allowing the traffic to reach that network object, and finally applying the access-list (ACL) that I’ve used to the outside interface (where the VMware View traffic will be coming from)
Warning: The last command (starting access-group, applies the access-list ‘inbound’ in the inbound direction on the outside interface, you may already have an access-list applied to this interface (the ‘show run access-group’ command will tell you) If you do have another ACL simply substitute the name of yours for the work inbound in my example below).
Note: If you port forward https on the outside interface, as I’m doing here, you will not be able to access the ASDM from outside – unless you put it on another port: The following two commands would change the ASDM to port 2345 for example:
no http server enable
http server enable 2345
Related Articles, References, Credits, or External Links
Cisco PIX / ASA Port Forwarding Using Command Line, ASDM and PDM