KB ID 0001650
Problem
I was asked if I’d ever set this up the other week. Surprisingly I had not, I’d deployed Duo for other things, but not for Cisco AnyConnect. As I had some other ‘Duo’ related tasks coming up, I was deploying it on the test bench, then adding in my Cisco ASA and AnyConnect wasn’t much more work!
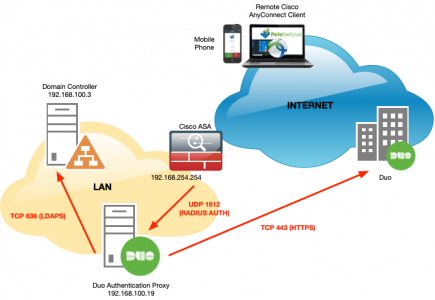
Here’s my topology;
- My ASA is running version 9.1
- My Duo Authentication Proxy is installed on Windows 2019
- I’m running Cisco AnyConnect Version 4.8
Cisco AnyConnect Duo Pre-Requisites
I already have a Duo Authentication Proxy server setup and my users are enrolled, you will need to set this up first. See the following article;
Duo: ADSync and Enroll Users via SMS
Also I’m using LDAPS, if you have not set that up (it’s easy) then see the following article;
Get Ready for LDAPS Channel Binding
I would also setup AnyConnect and have it working with LOCAL authentication before migrating to Duo/2FA Authentication;
Cisco ASA 5500 AnyConnect Setup From Command Line
Duo: Deploy Cisco RADIUS VPN
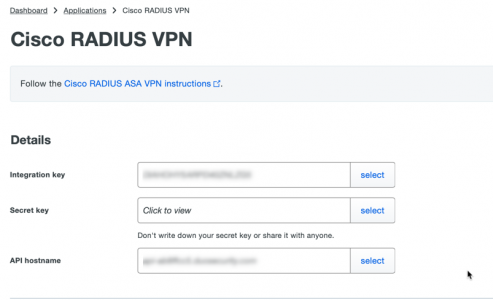
Log into the the Duo Admin Portal > Applications > Protect an Application > Search for and select Cisco RADIUS VPN > Copy the Integration Key, Secret Key and the API hostname to notepad.
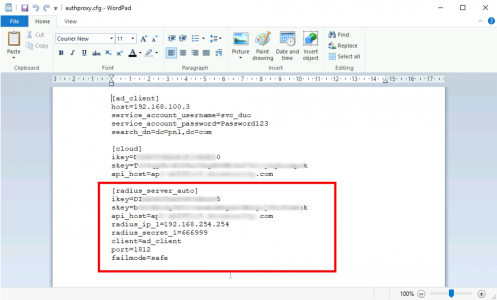
Back on your Duo Authentication Proxy, (because you completed the pre-requisites) add the following to the bottom of your authproxy.cfg file;
[radius_server_auto] ikey=XXXXXXXXXXXXXXXXXXXX skey=XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX api_host=XXXXXXXXXXXXXXXXXXXXXXXXXXXX radius_ip_1=192.168.254.254 radius_secret_1=666999 client=ad_client port=1812 failmode=safe
Note: 192.168.254.254 is the inside interface of the Cisco ASA, and 666999 is the shared secret we will enter on the firewall in a moment. I’m not sure you have to, but at this point I’d restart the Duo Auth Proxy service as well.
Configure Cisco ASA for Duo RADIUS
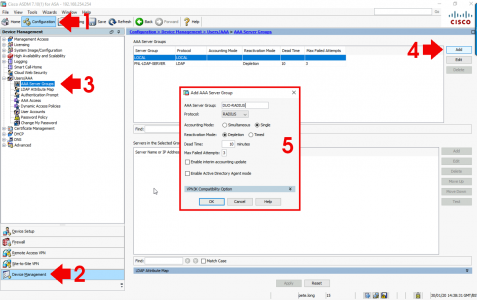
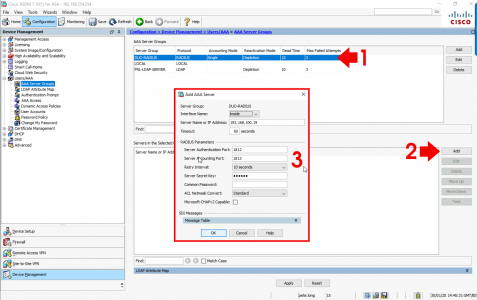
Log into the ASDM > Configuration > Device Management > Users/AAA > AAA Server Groups > Add.
You only need to add the name of the server group i.e DUO-RADIUS, and ensure protocol is set to RADIUS > OK > Apply.
Now select the DUO-RADIUS group in the top window, and click ‘Add’ in the bottom window > Specify the interface that’s facing the Duo Auth Proxy Server > Add its IP address > Change the Timeout to 60 seconds > Set the Server Authentication port to 1812 > Set the Server Accounting Port to 1813, (though it will NOT do accounting) > Type in the Secret Key you specified above > Untick Microsoft CHAPv2 Capable > OK.
Testing Cisco ASA Duo 2FA Authentication
I’ve written about testing AAA before in the following article;
Cisco – Testing AAA Authentication (Cisco ASA and IOS)
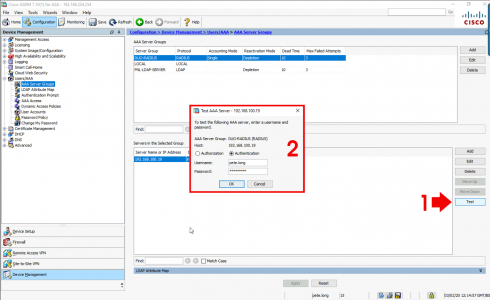
But essentially with the SERVER selected > Test > Select Authentication > Enter the username and password for a user.
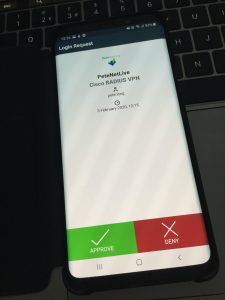
What about passcodes and 2FA? This will send a push notification to the users Duo Authenticator (phone), you can enter the password then a comma, then the passcode from the Duo App if you wish, I just prefer the push notification).
Like so! Approve the request.
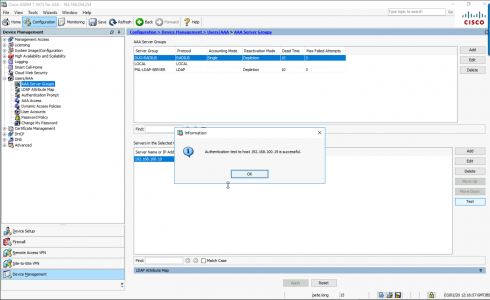
Authentication should be successful.
Change AnyConnect To Use Duo 2FA (AAA)
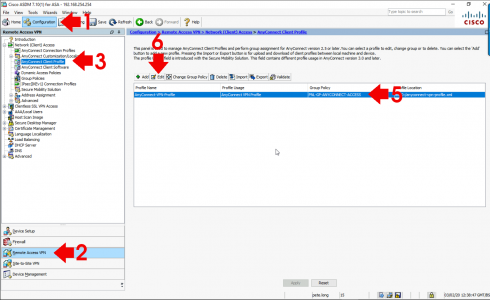
Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Client Profile > Select yours > Edit.
I don’t have one! OK Create one and link to your AnyConnect Profile.
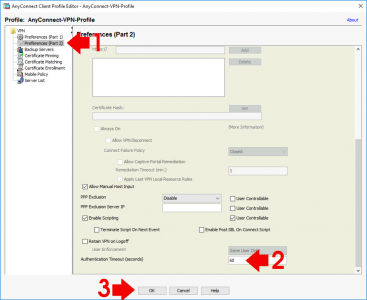
Preference (Part 2) > Scroll to the bottom > Change Authentication Timeout to 60 seconds > OK > Apply.
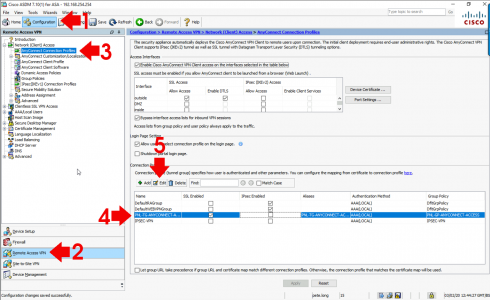
Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Connection Profiles > Select the one used for your AnyConnect > Edit.
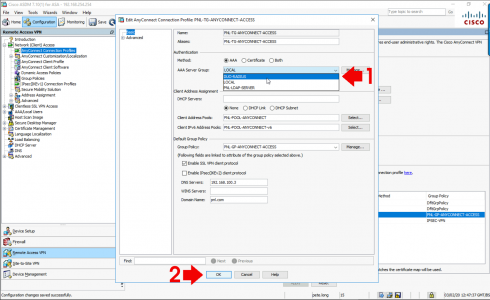
Change AAA Server Group to DUO-RADIUS > OK > Apply.
Give it a test, Don’t forget to save the changes when you are happy (File > Save Running To Flash.)
Related Articles, References, Credits, or External Links
NA

18/09/2020
I’m looking into duo with anyconnect. But since we apply different ACL to different user groups we need to map those. Do you have any experience?
I’ve read the documentation and it looks like I have to run NPS and then point the DUO proxy to my NPS. Duo needs to be configured to pass-through radius attributes.
Also since we use ldap to the ASA we need to establish an NPS config that does map the groups to ACL assignments. Another tricky bit is that we allow for a user to be part of multiple ACl-groups.
21/09/2020
If ever I need to apply different ACLs to different user groups I use DAP, or NPS – I’ve outlined both approaches elsewhere on the site.
06/10/2020
I need a solution for the same approach. How did you configure DUO proxy for this? I already have working NPS, just need to add DUO to it.
06/10/2020
You would need to enable Duo as the ‘Secondary Authentication’, in your AAA settings.
05/06/2022
Great post again Pete, simple, straight forward and very educating. Thanks!