KB ID 0001255
Problem
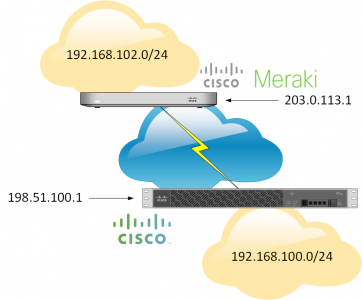
This was surprisingly easier than I was expecting! Special thanks to Steve for letting me loose on his test network for the Meraki end of the tunnel. Here I’m using an MX 64 Security appliance, and a Cisco ASA 5510.
Note: The Meraki device will need a static IP.
Solution
Configuring Meraki MX Device for VPN to a Cisco ASA
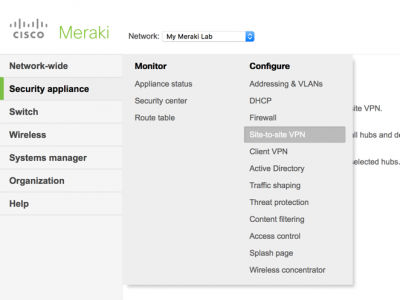
From your Meraki dashboard > Security Appliance > Site To Site VPN.
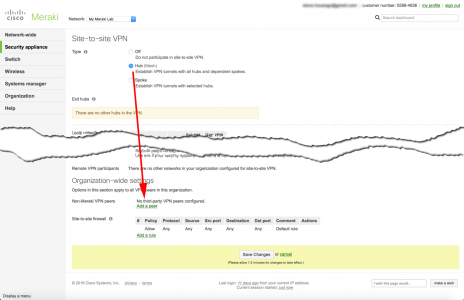
If you have no VPNs setup then you will need to select ‘Hub’, then scroll down to ‘Non-Meraki VPN Peers’ > Add a peer.
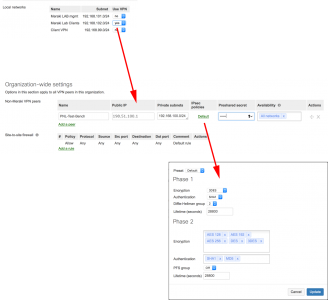
Give the tunnel a name > Public IP is the address of the ASA > Private Subnets is the network(s) behind the ASA > Preshare secret is a shared key you will enter on the ASA (below). Above select all the networks you have behind the Meraki that you want to participate in the VPN and set their ‘Use VPN’ Status to ‘Yes’
Note: If you click the IPSEC policy you will see what it wants to use for phase 1 and phase 2 of the VPN tunnel. BE AWARE: By default PFS (Perfect Forward Secrecy) is disabled. If you setup your AS VPN from within the ASDM wizard this may be enabled on the ASA. More reason to use the command line options I give you below!
If you don’t know the public IP of your Meraki device, here is where to find it (so you can use it when configuring the ASA).
Configuring Cisco ASA5500 for VPN to a Meraki MX Device
To make things simple, change the values in RED below then you can paste in the command to your Cisco ASA.
WARNING: Below I use a crypto map called CRYPTO-MAP If you already have one then CHANGE the name to match your existing one (‘show run crypto map‘ will show you). e.g. if yours is called outside_map then change the entries below to outside_map 2.
Note: This config uses newer (post 8.3) NAT commands.
! crypto ikev1 enable outside crypto ikev1 policy 10 authentication pre-share encryption 3des hash sha group 2 lifetime 12800 ! object network OBJ-This-Site subnet 192.168.100.0 255.255.255.0 object network OBJ-Meraki-Site subnet 192.168.102.0 255.255.255.0 ! access-list MERAKI-INTERESTING-TRAFFIC extended permit ip object OBJ-This-Site object OBJ-Meraki-Site nat (inside,outside) source static OBJ-This-Site OBJ-This-Site destination static OBJ-Meraki-Site OBJ-Meraki-Site no-proxy-arp route-lookup ! tunnel-group 203.0.113.1 type ipsec-l2l tunnel-group 203.0.113.1 ipsec-attributes pre-shared-key 123456 isakmp keepalive threshold 10 retry 2 ! crypto ipsec ikev1 transform-set MERAKI-TRANSFORM esp-aes-256 esp-sha-hmac ! crypto map CRYPTO-MAP 1 match address MERAKI-INTERESTING-TRAFFIC crypto map CRYPTO-MAP 1 set peer 203.0.113.1 crypto map CRYPTO-MAP 1 set ikev1 transform-set MERAKI-TRANSFORM crypto map CRYPTO-MAP interface outside !
Related Articles, References, Credits, or External Links
NA

06/04/2018
should change the lifetime 28800
09/04/2018
Lifetimes are specified by the initiator (usually).
P
10/08/2018
How to do this if the Meraki is on a DHCP-assigned external address (e.g. SOHO)?
Doesn’t look like Meraki can connect via EZVPN.
12/08/2018
You don’t! If your Meraki has a DHCP public address then you need a Meraki at both ends to form a VPN. EXVPN is a Cisco solution, Meraki might be owned by Cisco, but its a completely different product set.
07/09/2018
Hi Pete,
is it not possible to have a dynamic map at the ASA site? or is the meraki only reporting its Public IP as the identifier?
07/09/2018
The Meraki does not support EZVPN, it needs a static IP (if it’s taking to an ASA) you would need a Meraki at both ends to achieve this.
Pete
07/09/2018
Hi P,
Is it possible for the Meraki to identify itself with its hostname instead of IP adres, in that case u should be able to create a Dynamic crypto map at the ASA site, correct?
best regard,
Yoeri
19/09/2019
Does it support GRE instead IPSEC?
19/09/2019
The ASA certainly does (with a modern OS installed on it!), but I’ve waited 15 years for that, so I’d be amazed if the Meraki does, that’s designed for the ‘point and click generation’. 🙂
06/11/2020
hello Pete,
I am wondering if the no-nat of the vpn traffic happens by default on the Meraki. I can see that you set it up on the ASA side, but it seems like none of that happens on the Meraki, so I am wondering how it works. Also, I am reading on other forums, it looks like the No-NAT feature was in beta at the time of your writing of this article. Could you please comment on this?
06/11/2020
It’s been such a long tome since I worked on Meraki I could not comment, I’ll open it up for the other visitors to comment.