KB ID 0001091
Problem
Given the amount of ASA work I do it’s surprising that the first time I saw an ASA 5506-X was last week (I’ve been working on larger firewalls for a while). I’m probably going to have to do a few of these over the next couple of years so I’ll update this article as things surface.
Solution
Q: Can I just copy the config from an ASA 5505 to an ASA 5506-X?
A: No, that would be nice, truth be told if the 5505 is running an OS newer than 8.3, about 90% of the config can be copy/pasted if you know what you are doing.
The ASA 5506 Interfaces are different.
- Unlike its predecessor (and just about all other Cisco equipment), the interfaces start at number 1 (the 5505 starts at 0).
- The 5506 Interfaces are the opposite way round (left to right).
- The 5506 has IP addresses applied to its physical interfaces. Where as the 5505 had IP addresses applied to VLANs and then the physical interfaces were added to the appropriate VLAN. Note: the 5506 still supports VLANs, (5 or 30 with a security plus license).*
*UPDATE: After version 9.7 This has changed (on the 5506-X) See the following article for an explanation;
Cisco ASA 5506-X: Bridged BVI Interface
So let’s say your 5505 has three interfaces called inside, outside, and DMZ, (yours might have different names, and you may only have two,) the relevant parts of the 5505 config would be;
ASA 5505 VLAN and Physical Interface configuration interface Vlan1 nameif inside security-level 100 ip address 192.168.10.254 255.255.255.0 ! interface Vlan2 nameif outside security-level 0 ip address 123.123.123.123 255.255.255.252 ! interface Vlan3 nameif DMZ security-level 50 ip address 10.0.0.1 255.0.0.0 ! interface Ethernet0/0 switchport access vlan 2 ! interface Ethernet0/1 ! interface Ethernet0/2 switchport access vlan 3 ! interface Ethernet0/3 ! interface Ethernet0/4 ! interface Ethernet0/5 ! interface Ethernet0/6 ! interface Ethernet0/7 !
VLAN Note: You might be wondering why no ports have been put into VLAN 1? By default all ports are in VLAN 1, So above, ports 0/1 and 0/3 to 0/7 are all in VLAN 1.
Outside IP Note: Yours may say ‘dhcp setroute’ if it does not have a static IP , that’s fine.
To convert that (Assuming you are NOT going to use the BVI interface, (see link above!);
ASA 5506-X Physical Interface configuration interface GigabitEthernet1/1 nameif outside security-level 0 ip address 123.123.123.123 255.255.255.252 ! interface GigabitEthernet1/2 nameif inside security-level 100 ip address 192.168.10.254 255.255.255.0 ! interface GigabitEthernet1/3 nameif DMZ security-level 50 ip address 10.0.0.1 255.0.0.0 !
AnyConnect Has Changed
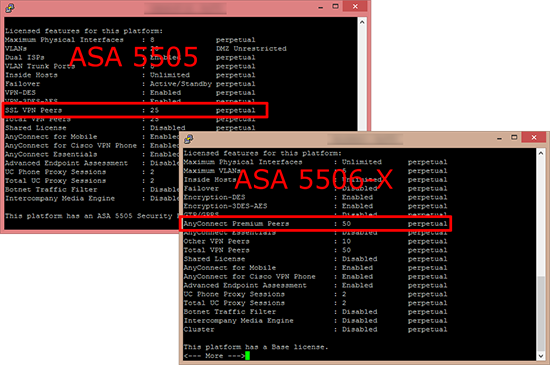
If you use AnyConnect then prepare for a little hand wringing. The 5505 could support up to 25 SSL VPN connections. On a 5506 they are actually called AnyConnect now, and it supports up to 50.
There is no Essentials license for a 5506-X! Don’t bother looking, you need to get your head into AnyConnect 4 licensing, I’ve already written about that at length.
AnyConnect 4 – Plus and Apex Licensing Explained
Q: Does this mean I can’t use my AnyConnect 3 (or earlier) packages in the new 5506?
A: Yes you can, but you will only get two connections, unless you purchase additional Apex/Plus licensing.
I’m working on the assumption that we are going to load in the AnyConnect 4 packages and use those. With that in mind if anyone manages to get them added to their Cisco profile without the ‘Additional Entitlement Required’ then contact me, and let me know how, (link at bottom). I have to ring Cisco and use my employers partner status to get the client software 🙁
In addition to getting new AnyConnect Packages and loading them into the new 5506. If you have an anyconnect XML profile, that will also need copying into the new firewalls flash drive before you can paste the AnyConnect settings in.
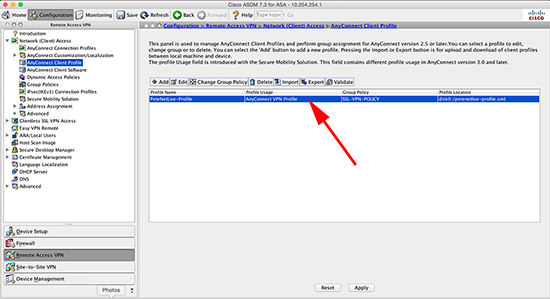
Below you can see I’ve got a profile on my 5505.
Tools > File Transfer > File Transfer > Between Local PC and Flash. (Do the reverse to get the file(s) into the new 5506).
Note: You can also do this from CLI by copying the file to a TFTP server.
Below is a typical AnyConnect config from an ASA 5505, I’ve highlighted the lines that will cause you problems.
ip local pool ANYCONNECT-POOL 192.168.100.1-192.168.100.254 mask 255.255.255.0 object network OBJ-ANYCONNECT-SUBNET subnet 192.168.100.0 255.255.255.0 ! webvpn enable outside anyconnect-essentials <-REMOVE THIS IT'S OBSOLETE anyconnect-win-3.1.05152-k9.pkg 1 <-REPLACE WITH ANYCONNECT 4 anyconnect image disk0:/anyconnect-macosx-i386-3.1.04063-k9.pkg 2 <-REPLACE WITH ANYCONNECT 4 anyconnect profiles SSL-VPN-POLICY disk0:/PeteNetLive-Profile.xml <-COPY OVER FIRST anyconnect enable tunnel-group-list enable ! access-list SPLIT-TUNNEL standard permit 10.0.0.0 255.255.255.0 ! group-policy GroupPolicy_ANYCONNECT-PROFILE internal group-policy GroupPolicy_ANYCONNECT-PROFILE attributes vpn-tunnel-protocol ssl-client dns-server value 10.0.0.10 10.0.0.11 wins-server none split-tunnel-policy tunnelspecified split-tunnel-network-list value SPLIT-TUNNEL default-domain value petenetlive.com split-tunnel-all-dns enable webvpn anyconnect profiles value SSL-VPN-POLICY type user ! tunnel-group ANYCONNECT-PROFILE type remote-access tunnel-group ANYCONNECT-PROFILE general-attributes default-group-policy GroupPolicy_ANYCONNECT-PROFILE address-pool ANYCONNECT-POOL tunnel-group ANYCONNECT-PROFILE webvpn-attributes group-alias ANYCONNECT-PROFILE enable ! nat (inside,outside) 2 source static any any destination static OBJ-ANYCONNECT-SUBNET OBJ-ANYCONNECT-SUBNET no-proxy-arp route-lookup !
ASA Transferring Certificates From One ASA to Another
I appreciate a lot of you wont be using certificates, and even if you use AnyConnect you just put up with the certificate error. That’s fine, but do me a favor? Before you do anything else go and generate the RSA keys on your new 5506 before you do anything else, (people forgetting to do this has cause me a LOT of grief over the years). So set the host name, domain-name, and then generate the keys like so;
ciscoasa# configure terminal Petes-ASA(config)# hostname Petes-ASA Petes-ASA(config)# domain-name petenetlive.com Petes-ASA(config)# crypto key generate rsa modulus 2048 INFO: The name for the keys will be: <Default-RSA-Key> Keypair generation process begin. Please wait... Petes-ASA(config)#
OK, so if you are still reading this section, then you have at least one certificate, that you need to move to the new firewall. For each scenario here’s what I recommend you do;
Self Signed Certificate from your own PKI / CA Server : Just generate a new cert for the new firewall and import it the same as you did on the old firewall
Externally / Publicly signed certificate that you have paid for: This we will need to export then import onto the new 5506. (Note: If there’s not much time left to run on the validity, it may be easier to get onto the certificate vendor and have a new one reissued to save you having to replace it in a couple of months – just a thought).
If you have purchased a certificate you will have already gone though the process below;
Cisco ASA 5500 – Using a Third Party Digital Certificate
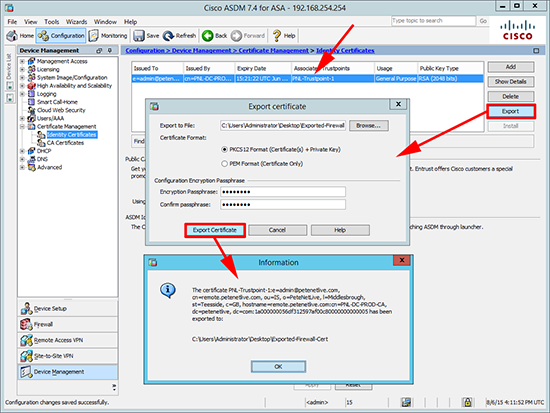
The easiest option for you is to go where you purchased the cert, download it again, and import it into the new firewall. But here’s where you find out you forgot the username and password you used, or the guy who sorted this out has left the company etc. If that is the case all is not lost. You can export an identity certificate, either from the ADSM;
Cisco ASA Export Certificates From ASDM
Configuration > Device Management > Certificate Management > Identity Certificates > Select the certificate > Export > Choose a location and a ‘pass-phrase’.
Cisco ASA Export Certificates From Command Line.
To do the same at CLI the procedure is as follows;
Get Your Trustpoint(s) Names Petes-ASA# show crypto ca trustpoints Trustpoint ASDM_TrustPoint0: Not authenticated. Trustpoint PNL-Trustpoint-1: Subject Name: cn=PNL-DC-PROD-CA dc=petenetlive dc=com Serial Number: 5ec427e4910fa2bf47e1269e7fdd7081 Certificate configured. Then Export the Certificate(s) for that Trustpoint Petes-ASA# configure terminal Petes-ASA(config)# crypto ca export PNL-Trustpoint-1 pkcs12 Password123 Exported pkcs12 follows: -----BEGIN PKCS12----- MIISXwIBAzCCEhkGCSqGSIb3DQEHAaCCEgoEghIGMIISAjCCEf4GCSqGSIb3DQEH BqCCEe8wghHrAgEAMIIR5AYJKoZIhvcNAQcBMBsGCiqGSIb3DQEMAQMwDQQId/f5 {{{{{{{LOTS OF OUTPUT REMOVED FOR THE SAKE OF BREVITY}}}}}}}}}}} mLt/6QKDVig6ofxrnvP0tbh9Jmjwe4NkTsJUb+H+7JGvJoUsMD0wITAJBgUrDgMC GgUABBRCPROoZsdSBfIpwVmvfSSoOxzNCAQUWJ/J9hTkuNd92u4Z3owgrrO3cYIC AgQA -----END PKCS12----- Petes-ASA(config)#
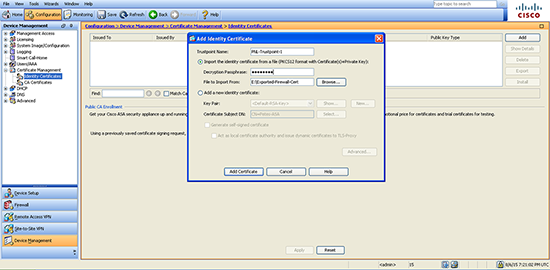
Cisco ASA Import Certificates From ASDM
Configuration > Device Management > Certificate Management > Identity Certificates > Add > Use the same Trustpoint name as the source firewall > Browse the file you exported earlier > Enter the passphrase > Add Certificate.
Cisco ASA Import Certificates From Command Line.
To do the same at CLI the procedure is as follows, Note: You need to paste in the text from the output.
Petes-ASA# configure terminal Petes-ASA(config)# crypto ca import PNL-Trustpoint-1 pkcs12 Password123 Enter the base 64 encoded pkcs12. End with the word "quit" on a line by itself: -----BEGIN PKCS12----- MIISXwIBAzCCEhkGCSqGSIb3DQEHAaCCEgoEghIGMIISAjCCEf4GCSqGSIb3DQEH BqCCEe8wghHrAgEAMIIR5AYJKoZIhvcNAQcBMBsGCiqGSIb3DQEMAQMwDQQId/f5 {{{{{{{LOTS OF OUTPUT REMOVED FOR THE SAKE OF BREVITY}}}}}}}}}}} mLt/6QKDVig6ofxrnvP0tbh9Jmjwe4NkTsJUb+H+7JGvJoUsMD0wITAJBgUrDgMC GgUABBRCPROoZsdSBfIpwVmvfSSoOxzNCAQUWJ/J9hTkuNd92u4Z3owgrrO3cYIC AgQA -----END PKCS12----- quit INFO: Import PKCS12 operation completed successfully Petes-ASA(config)#
Assorted Firewall Migration ‘Gotchas’
Time (Clock Setting)
If you do any AAA via Kerberos or LDAP, then not having the time correct on the new ASA might get you locked out of it. I would always suggest setting up NTP so do that before you restart.
Cisco ASA – Configuring for NTP
ARP Cache
Not on the ASA, but on the devices the ASA is connecting to, (routers and switches etc). Unplug an ASA 5505 and plug in an ASA 5506, and nine times out of ten you will not get comms. This is because the device you are connecting to has cached the MAC address of the old firewall in its ARP cache. So either reboot the device, (or it thats not practical, lower the ARP cache to about 30 seconds).
ASA 5505 to 5506 Config To Copy And Paste
Below I’ll put a full config for an ASA 5505. If the text is normal,the commands can be copy and pasted directly into the new firewall. If the text is RED, then you can NOT, and I will have outlined the problems above.
hostname Petes-ASA domain-name petenetlive.com enable password H4ejVQF2DI/W9sLZ encrypted xlate per-session deny tcp any4 any4 xlate per-session deny tcp any4 any6 xlate per-session deny tcp any6 any4 xlate per-session deny tcp any6 any6 xlate per-session deny udp any4 any4 eq domain xlate per-session deny udp any4 any6 eq domain xlate per-session deny udp any6 any4 eq domain xlate per-session deny udp any6 any6 eq domain passwd 2GFQnbJIdI.2KYOU encrypted names ! interface Ethernet0/0 switchport access vlan 2 ! interface Ethernet0/1 ! interface Ethernet0/2 switchport access vlan 12 ! interface Ethernet0/3 ! interface Ethernet0/4 ! interface Ethernet0/5 ! interface Ethernet0/6 ! interface Ethernet0/7< ! interface Vlan1 nameif inside security-level 100 ip address 192.168.1.1 255.255.255.0 ! interface Vlan2 nameif outside security-level 0 ip address 123.123.123.123 255.255.255.252 ! DONT COPY OVER THE BOOT SYSTEM PATHS FROM THE OLD FIREWALL ! boot system disk0:/asa903-6-k8.bin boot system disk0:/asa902-k8.bin ! ftp mode passive clock timezone GMT/BST 0 clock summer-time GMT/BDT recurring last Sun Mar 1:00 last Sun Oct 2:00 dns server-group DefaultDNS domain-name petenetlive.com same-security-traffic permit inter-interface same-security-traffic permit intra-interface ! NOTE ALL THE OBJECTS AND OBJECT GROUPS CAN BE COPIED OVER ! object network obj_any subnet 0.0.0.0 0.0.0.0 object network Obj-INT-Server1 host 192.168.1.10 object network Obj-Ext-Public_1 host 123.123.123.124 object network VPN_Pool subnet 10.253.253.0 255.255.255.0 object service Obj-ApplicationX-Ports-TCP service tcp destination eq 1234 object-group icmp-type Obj-ICMP icmp-object echo-reply icmp-object time-exceeded icmp-object unreachable ! NOTE ALL THE ACCESS-LISTS CAN BE COPIED OVER ! access-list inbound remark traffic allowed to Server1 access-list inbound extended permit tcp any object Obj-INT-Server1 object-group Obj-ApplicationX-Ports-TCP access-list inbound extended deny ip any any log disable access-list outbound remark traffic allowed from Server1 access-list outbound extended permit ip object Obj-INT-Server1 any access-list outbound extended deny ip any any log disable ! no pager logging enable logging asdm debugging logging mail critical logging from-address netalerts@petenetlive.com logging recipient-address externalalert@petenetlive.com level critical mtu inside 1500 mtu outside 1500 ip local VPN-POOL 10.253.253.1-10.253.253.50 mask 255.255.255.128 ! IF YOU EXECUTE A NO FAILOVER IT WILL COMPLAIN IF YOU DON'T HAVE A FAILOVER LICENCE ! no failover ! icmp unreachable rate-limit 50 burst-size 10 icmp permit any inside icmp permit any outside no asdm history enable arp timeout 14400 no arp permit-nonconnected ! NAT COMMANDS ARE FINE IF THE SOURCE IS NEWER THAN VERSION 8.3 ! nat (inside,outside) source static any any destination static VPN_Pool VPN_Pool no-proxy-arp route-lookup ! object network obj_any nat (inside,outside) dynamic interface object network Obj-INT-Server1 nat (inside,outside) static Obj-Ext-Public_1 ! access-group inbound in interface inside access-group outbound in interface outside< ! route outside 0.0.0.0 0.0.0.0 123.123.123.124 1 route inside 192.168.1.0 255.255.255.0 192.168.1.50 1 timeout xlate 3:00:00 timeout pat-xlate 0:00:30 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute timeout tcp-proxy-reassembly 0:01:00 timeout floating-conn 0:00:00 dynamic-access-policy-record DfltAccessPolicy ! aaa-server AD protocol kerberos aaa-server AD (Inside) host 192.168.1.10 kerberos-realm PETENETLIVE.COM aaa-server AD (Inside) host 192.168.1.11 kerberos-realm PETENETLIVE.COM aaa-server AD-LDAP protocol ldap aaa-server AD-LDAP (Inside) host 192.168.1.10 server-port 636 ldap-base-dn OU=Users, OU=PETENETLIVE, DC=com ldap-scope subtree ldap-naming-attribute sAMAccountName ldap-login-password Password123 ldap-login-dn cn=ciscoasa, OU=Service Accounts, OU=Service, DC=petenetlive, DC=com ldap-over-ssl enable server-type microsoft ! user-identity default-domain LOCAL aaa authentication enable console LOCAL aaa authentication http console LOCAL aaa authentication ssh console LOCAL aaa authentication telnet console LOCAL aaa authentication serial console LOCAL http server enable 2456 http 192.168.1.0 255.255.255.0 inside http 245.245.245.0 255.255.255.0 outside no snmp-server location no snmp-server contact snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart sysopt noproxyarp inside sysopt connection tcpmss 0 crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac crypto ipsec ikev2 ipsec-proposal AES256 protocol esp encryption aes-256 protocol esp integrity sha-1 md5 crypto ipsec ikev2 ipsec-proposal AES192 protocol esp encryption aes-192 protocol esp integrity sha-1 md5 crypto ipsec ikev2 ipsec-proposal AES protocol esp encryption aes protocol esp integrity sha-1 md5 crypto ipsec ikev2 ipsec-proposal 3DES protocol esp encryption 3des protocol esp integrity sha-1 md5 crypto ipsec ikev2 ipsec-proposal DES protocol esp encryption des protocol esp integrity sha-1 md5 crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5 crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP crypto map outside_map interface outside crypto ikev2 policy 1 encryption aes-256 integrity sha group 5 2 prf sha lifetime seconds 86400 crypto ikev2 policy 10 encryption aes-192 integrity sha group 5 2 prf sha lifetime seconds 86400 crypto ikev2 policy 20 encryption aes integrity sha group 5 2 prf sha lifetime seconds 86400 crypto ikev2 policy 30 encryption 3des integrity sha group 5 2 prf sha lifetime seconds 86400 crypto ikev2 policy 40 encryption des integrity sha group 5 2 prf sha lifetime seconds 86400 crypto ikev2 enable outside client-services port 443 crypto ikev1 enable outside crypto ikev1 policy 130 authentication crack encryption des hash sha group 2 lifetime 86400 crypto ikev1 policy 140 authentication rsa-sig encryption des hash sha group 2 lifetime 86400 crypto ikev1 policy 150 authentication pre-share encryption des hash sha group 2 lifetime 86400 ! crypto ca trustpoint PNL-Trustpoint-1 enrollment terminal fqdn remote.petenetlive.com subject-name CN=remote.petenetlive.com,OU=IS,O=PeteNetLive,C=GB,St=Teesside, L=Middlesbrough,EA=admin@petenetlive.com! keypair PNL-NEW-KEYPAIR crl configure crypto ca trustpool policy crypto ca certificate chain ASDM_TrustPoint1 certificate ca 33f5d6ed96a558bc45f43f6c9b8fd82d 30820397 3083027f a0030201 02021033 f5d6ed96 a558bc45 f43f6c9b 8fd82d30 0d06092a 864886f7 0d010105 05003052 31133011 060a0992 268993f2 2c640119 16036e65 74311b30 19060a09 92268993 f22c6401 19160b70 6574656e 65746c69 7665311e 301c0603 55040313 15706574 656e6574 6c697665 2d504e4c 2d44432d 4341301e 170d3133 31313131 31313135 30305a17 0d323331 31313131 31323530 305a3052 31133011 060a0992 268993f2 2c640119 16036e65 74311b30 19060a09 92268993 f22c6401 19160b70 6574656e 65746c69 7665311e 301c0603 55040313 15706574 656e6574 6c697665 2d504e4c 2d44432d 43413082 0122300d 06092a86 4886f70d 01010105 00038201 0f003082 010a0282 010100c8 2d21e8cb 317741d7 e4eb4af4 2561f92a efec293a 9202bc38 e9d25eb7 3a0ff9e0 7c7ee9b3 8e76f328 df115581 3f70ac45 91b402b4 dba25c80 6dee49da eb904bda f2fbb21f 5661ba2a 81f9cd37 87d87811 05cce829 8112495b 0587b272 12b6d3c1 107d9529 e860900b 947af212 0b72eb0e de2f5891 87be7172 1fc02f38 ba82d0c9 ec3351b2 c6fe216a 0f674e81 608ba7f9 5fd9343a 4d815a12 0dbc0747 854211ba c0a32cdb 18fe8a92 bc5dd319 f4fba969 ed95c7d6 a51620f3 d3510b56 17471ece 89c2393d c14b42b9 2d4fc2c5 7f47b9b0 c4645c60 00d02e1c e54669b9 e54d0d49 1b6a4a09 e5f1ad5c e2f901d9 b679ef5a 27de98bf 089c79b4 6723295a 436db902 03010001 a3693067 30130609 2b060104 01823714 0204061e 04004300 41300e06 03551d0f 0101ff04 04030201 86300f06 03551d13 0101ff04 05300301 01ff301d 0603551d 0e041604 146baa8b 30599cfb d5a0b40a 33a9c296 f4f24ec2 80301006 092b0601 04018237 15010403 02010030 0d06092a 864886f7 0d010105 05000382 0101007a d4edaf88 6bd0d3d5 916c9c1c 3d67d551 f78b41f6 75740965 f6dca8df 30878d56 65b900c8 cb27aa65 9092c9f0 c3bdc080 ded23cb0 10715db9 af8cd39c 5416d8d2 a0ee7ae2 ceb09be7 145a0969 1bf672db e0c532d2 26a27e8a f897f474 e9e638e1 bf12e385 3bb9af1e bdaadecd cbcf5a61 23c5b68f a040a5e0 70150541 d190eeef 3d72d702 b0d9d3fa 0241802a b87505c6 a217c714 e9f55692 b9bdd84f 25351f18 35bf53c1 b24d10be 876ef392 c971dee4 10a5d244 d08624eb 6d29975a 2f35e3d1 38260a1d 51e6b661 f0c709a7 0e072039 530a26b8 78d00f22 a754c0f7 90fb58a0 5d564259 ceafe29f 22e95391 7ea10a81 629f384c 7ed8d009 02f65068 e93ff0 quit crypto ca certificate chain PNL-Trustpoint-1 certificate 1a000000056df312597af00c80000000000005 3082062a 30820512 a0030201 0202131a 00000005 6df31259 7af00c80 00000000 0005300d 06092a86 4886f70d 01010505 00304b31 13301106 0a099226 8993f22c 64011916 03636f6d 311b3019 060a0992 268993f2 2c640119 160b7065 74656e65 746c6976 65311730 15060355 0403130e 504e4c2d 44432d50 524f442d 4341301e 170d3135 30363135 31353131 32325a17 0d313730 36313531 35323132 325a3081 c9312530 2306092a 864886f7 0d010902 13167265 6d6f7465 2e706574 656e6574 6c697665 2e636f6d 310b3009 06035504 06130247 42311130 0f060355 04081308 54656573 73696465 31163014 06035504 07130d4d 6964646c 65736272 6f756768 31143012 06035504 0a130b50 6574654e 65744c69 7665310b 30090603 55040b13 02495331 1f301d06 03550403 13167265 6d6f7465 2e706574 656e6574 6c697665 2e636f6d 31243022 06092a86 4886f70d 01090116 1561646d 696e4070 6574656e 65746c69 76652e63 6f6d3082 0122300d 06092a86 4886f70d 01010105 00038201 0f003082 010a0282 010100ed 6403f970 5c3d8f90 c106cc7a 85b69965 05ac5a50 2f3f0351 984e28aa d68d1f28 88d44ae6 99997b06 cc7ca9a0 573db801 d8277276 b6e7d7a7 6863da35 29156dcd fbe063f2 9855bf75 b5529c22 ecbd87f0 9be50cc4 cf5d245f 9e7b4443 6e8afe02 9442f79d 16f0d4e6 09cdb3f4 0771173d 707a0cae 9facd254 a9ba4401 d3ce14fe 1ecee991 b83f7ca8 f11f549f b4b0f302 6d09eec7 b522d7b7 97af7648 a2f99b93 207c3f0c 62800df7 532478ad 9020c6e6 87fb956c d20289f6 68efe7ff a7914fea 7b28d9f4 e8504c40 48f65d88 dffcfa3e 5ecbc50a b28b07dc 792ce53d 0475ef96 12c3d402 d2ad7fcb b1099266 1fb5087b 71910dd4 d0b33dcf 7cc585c7 af0b4702 03010001 a3820286 30820282 300e0603 551d0f01 01ff0404 030205a0 30210603 551d1104 1a301882 1672656d 6f74652e 70657465 6e65746c 6976652e 636f6d30 1d060355 1d0e0416 0414e3d5 5aaa3004 d607bd3f 13384329 1acf7f21 92f3301f 0603551d 23041830 16801495 d2ae01e1 45769582 39b946bf a2799ccd c5d28a30 81d40603 551d1f04 81cc3081 c93081c6 a081c3a0 81c08681 bd6c6461 703a2f2f 2f434e3d 504e4c2d 44432d50 524f442d 43412c43 4e3d504e 4c2d4443 2d50524f 442c434e 3d434450 2c434e3d 5075626c 69632532 304b6579 25323053 65727669 6365732c 434e3d53 65727669 6365732c 434e3d43 6f6e6669 67757261 74696f6e 2c44433d 70657465 6e65746c 6976652c 44433d63 6f6d3f63 65727469 66696361 74655265 766f6361 74696f6e 4c697374 3f626173 653f6f62 6a656374 436c6173 733d6352 4c446973 74726962 7574696f 6e506f69 6e743081 c406082b 06010505 07010104 81b73081 b43081b1 06082b06 01050507 30028681 a46c6461 703a2f2f 2f434e3d 504e4c2d 44432d50 524f442d 43412c43 4e3d4149 412c434e 3d507562 6c696325 32304b65 79253230 53657276 69636573 2c434e3d 53657276 69636573 2c434e3d 436f6e66 69677572 6174696f 6e2c4443 3d706574 656e6574 6c697665 2c44433d 636f6d3f 63414365 72746966 69636174 653f6261 73653f6f 626a6563 74436c61 73733d63 65727469 66696361 74696f6e 41757468 6f726974 79303d06 092b0601 04018237 15070430 302e0626 2b060104 01823715 0885fbfb 0d83ea8c 0c83e187 2282c9d9 5783d9e2 675c86b2 fd3486f3 8d1b0201 64020104 30130603 551d2504 0c300a06 082b0601 05050703 01301b06 092b0601 04018237 150a040e 300c300a 06082b06 01050507 0301300d 06092a86 4886f70d 01010505 00038201 01002154 6bf54ea2 23a10a75 77df1b15 65c4c2b9 f17ff795 1cc28834 f41e6d88 3e03f18a 6e2bdc05 f1da80b3 10ccf096 eeec10c4 07dccb0a 0791a99f afda01ac 6cc7d985 82060c56 9e871a56 136805b3 7c277162 ae034197 addfe623 2bb814dd a401b053 b44fd7a6 302237ac f5bcc024 a25d3f84 d8d3ecb4 de0d9c7e 51e56c95 5e2ebf7a fee86ac6 26dcbaf8 09e4864f f3956447 398ed790 8cba02c3 bddca424 3777d625 3e39ed27 8b2778b8 20414b5d 30d1b20a ee1e2771 deea6f40 e2ed07de 8e66e2b6 651d7b19 4f3594d6 8acc0713 fd4436cc c38e9f92 b0ebc89a f39c599d 28a23040 d46dd8ad 80fec713 d38987f5 0c473098 5584e2de 3a1be0e3 72c24d48 90de quit certificate ca 5ec427e4910fa2bf47e1269e7fdd7081 30820371 30820259 a0030201 0202105e c427e491 0fa2bf47 e1269e7f dd708130 0d06092a 864886f7 0d010105 0500304b 31133011 060a0992 268993f2 2c640119 1603636f 6d311b30 19060a09 92268993 f22c6401 19160b70 6574656e 65746c69 76653117 30150603 55040313 0e504e4c 2d44432d 50524f44 2d434130 1e170d31 35303631 32313231 3935375a 170d3330 30363132 31323239 35365a30 4b311330 11060a09 92268993 f22c6401 19160363 6f6d311b 3019060a 09922689 93f22c64 0119160b 70657465 6e65746c 69766531 17301506 03550403 130e504e 4c2d4443 2d50524f 442d4341 30820122 300d0609 2a864886 f70d0101 01050003 82010f00 3082010a 02820101 00ad6ce6 b3d3852b 6524ee38 bab2beb8 1184f717 0bcebe1f 7b590260 6f0d0503 6d3409cb fcc7af7c f197cc74 91de290f cd65da5b cb5715b9 5c975ad6 20ba8573 4e4058fc 383f40d2 08f6390d f4c5c3e5 c7fc8571 ba7613a4 5e0dafde b98b8641 f9b5ba7f c50142c6 7854a785 22fa94d8 2f648590 0a0287ab 568fcac4 e6fde0aa 11cafe44 beadd840 7c1fa631 89be34c0 bf15858e c44f78be c1140f04 f1b89eb0 23442430 bacd9b9d a3b2620b 5d0e59c1 520b39e2 f95c9e91 305bd92b 4eab53b6 bfee551d 57e1f864 a043a757 39150ca7 bfdfb6ab 77510fa9 c8c35eec 02a59c75 460cdd61 7cae7949 9879e472 970bb444 25d01556 336b1a86 1ec95330 cac03f5e 01020301 0001a351 304f300b 0603551d 0f040403 02018630 0f060355 1d130101 ff040530 030101ff 301d0603 551d0e04 16041495 d2ae01e1 45769582 39b946bf a2799ccd c5d28a30 1006092b 06010401 82371501 04030201 00300d06 092a8648 86f70d01 01050500 03820101 005c4437 216d5cc1 38a0e3bb 8af4657d 83fca1a3 57483d54 4a73a663 c8bf8c2a b0280cc4 155f4a15 72da34ee 6e67ae3f c503b73f 3e267f05 b1be022e 2e979295 b661e942 ef8d2039 4da5e555 a1babc03 33792b4d 85272d81 0484c36c fd49c383 dd95b1a3 64dbca14 b01bc48a 61b6cb84 38128fbe 2860097c 1a0e15a1 6a3c409a be6074fb be64d87a 6d46b11e 8548fb44 dfc35483 1c7668cd e72828fa 102a2069 8939f613 11ec5bb6 341a70fc a6a85bc6 a93cdc73 59b36756 cba6f787 957d3eca 1ef9a057 31c2ae9c 26ab72f5 096129c6 0ed0bc05 0a7bca34 ae6fd90a 1e86cf91 49f558ea e174de18 dc8cb428 922bb233 ee5cf072 98a78f60 1a98f540 7c227063 e2 quit ! telnet 0.0.0.0 0.0.0.0 inside telnet timeout 5 ssh 192.168.1.0 255.255.255.0 inside ssh timeout 5 ssh version 2 console timeout 0 ! YOUR NEW FIREWALL HAS A MANAGEMENT INTERFACE, YOU MIGHT NOT WANT TO COPY THIS OVER ! management-access Inside ! tls-proxy maximum-session 24 ! threat-detection basic-threat threat-detection statistics port threat-detection statistics protocol threat-detection statistics access-list no threat-detection statistics tcp-intercept ntp server 87.194.255.141 source outside ntp server 194.117.157.4 source outside prefer ssl encryption 3des-sha1 webvpn enable outside anyconnect-essentials anyconnect image disk0:/anyconnect-win-2.5.2014-k9.pkg 1 anyconnect profiles SSL_VPN disk0:/Petenetlive-profile.xml anyconnect enable tunnel-group-list enable ! group-policy DefaultRAGroup internal group-policy DefaultRAGroup attributes dns-server value 192.168.1.12 192.168.1.13 vpn-tunnel-protocol ikev2 l2tp-ipsec default-domain value petenetlive.com group-policy DfltGrpPolicy attributes dns-server value 192.168.1.12 192.168.1.13 vpn-tunnel-protocol ikev1 ikev2 l2tp-ipsec ssl-client ssl-clientless address-pools value VPN_Pool ! username user1 password G0=2iYoApombmlE5de7 encrypted username user1 attributes service-type remote-access ! tunnel-group DefaultRAGroup general-attributes address-pool VPN_Pool ! class-map inspection_default match default-inspection-traffic ! policy-map type inspect dns preset_dns_map parameters message-length maximum client auto message-length maximum 512 policy-map global_policy class inspection_default inspect dns preset_dns_map inspect ftp inspect tftp inspect icmp inspect pptp inspect ipsec-pass-thru inspect icmp error class class-default set connection decrement-ttl ! service-policy global_policy global smtp-server 192.168.1.41 192.168.1.42 prompt hostname context no call-home reporting anonymous call-home profile CiscoTAC-1 no active destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService destination address email callhome@cisco.com destination transport-method http subscribe-to-alert-group diagnostic subscribe-to-alert-group environment subscribe-to-alert-group inventory periodic monthly subscribe-to-alert-group configuration periodic monthly subscribe-to-alert-group telemetry periodic daily no call-home reporting anonymous : end
Related Articles, References, Credits, or External Links
NA