KB ID 0000995
Problem
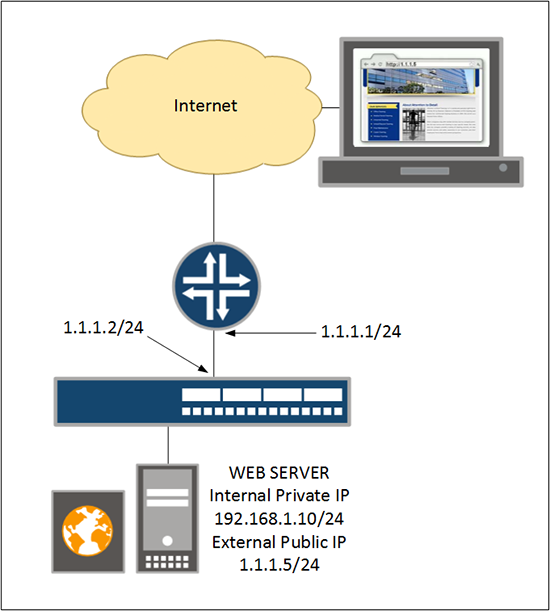
Setting up ‘Static NAT’ is the process of taking one of your ‘spare’ public IP addresses, and permanently mapping that public IP to a private IP address on your network.
In the example above I want to give my web sever which has an internal IP address of 192.168.1.10/24, the public IP address of 1.1.1.5/24. So if someone out on the Internet wants to view my website, they can browse to http://1.1.1.5 (or a URL that I’ve pointed to 1.1.1.5 like http://www.mywebsite.com). Then that traffic will be NATTED, on the firewall for me.
Solution
1. Create a rule-set from the ‘untrust’ zone. Then add a rule to that rule-set, that has a destination of 1.1.1.5/32, and finally set it to NAT that traffic to 192.168.1.10/32.
— JUNOS 12.1X44-D30.4 built 2014-01-11 03:56:31 UTC
root@FW-02% cli root@FW-02> configure Entering configuration mode
[edit] root@FW-02# set security nat static rule-set UNTRUST-TO-TRUST from zone untrust
[edit] root@FW-02# set security nat static rule-set UNTRUST-TO-TRUST rule NAT-RULE-1 match destination-address 1.1.1.5/32
[edit] root@FW-02# set security nat static rule-set UNTRUST-TO-TRUST rule NAT-RULE-1 then static-nat prefix 192.168.1.10/32
2. Set the firewall to proxy-arp (advertise your pubic IP address with is MAC address), then add the web server to the global address book.
Note: ge-0/0/0.0 is the physical address you are advertising the new IP address from, on firewalls in a failover cluster you would use the Reth address i.e. reth0.0
[edit] root@FW-02# set security address-book global address WEB-SERVER 192.168.1.10/32
3. Allow traffic OUT from the web server. Here I’m letting out all ports, if you wanted just web traffic then use the keyword junos-http (TCP Port 80 (http)).
[edit] root@FW-02# set security policies from-zone trust to-zone untrust policy WEB-SERVER-OUT match source-address WEB-SERVER
[edit] root@FW-02# set security policies from-zone trust to-zone untrust policy WEB-SERVER-OUT match destination-address any
[edit] root@FW-02# set security policies from-zone trust to-zone untrust policy WEB-SERVER-OUT match application any
[edit] root@FW-02# set security policies from-zone trust to-zone untrust policy WEB-SERVER-OUT then permit
4. Then allow traffic IN to the web server, (here I’m locking it down to just http).
[edit] root@FW-02# set security policies from-zone untrust to-zone trust policy WEB-SERVER-IN match destination-address WEB-SERVER
[edit] root@FW-02# set security policies from-zone untrust to-zone trust policy WEB-SERVER-IN match application junos-http
[edit] root@FW-02# set security policies from-zone untrust to-zone trust policy WEB-SERVER-IN then permit
5. Save the changes.
Juniper Allowing Traffic To Custom Ports And Applications
1. Although Juniper have a lot of built in ‘applications’ you can allow, what if you want to create your own? Below I’ll create a custom application for Remote Desktop Protocol (TCP port 3389).
[edit] root@FW-A# set applications application APP-RDP destination-port 3389
2. You could now use this application in your security policies e.g.
Related Articles, References, Credits, or External Links
NA