KB ID 0000982
Problem
Reverse Route injection is the process that can be used on a Cisco ASA to take a route for an established VPN, and populate/inject that route into the routing table of other devices in it’s routing group.
In the example below, on the main site, we have a Layer 3 switch that’s routing all the 192.168.x.x networks, and we have an established site to site VPN to a remote site. To access the web server at 172.16.1.10 the 192.168.x.x networks need a route to it.
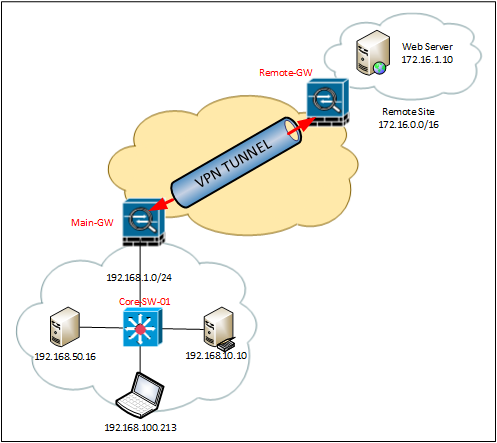
I’m going to use OSPF, (the ASA also supports EIGRP and RIP.)
Solution
1. We already have a site to site VPN, let’s find out what cryptomap it is using.
Main-GW# show run crypto map
crypto map CRYPTO-MAP 1 match address VPN-INTERESTING-TRAFIC
crypto map CRYPTO-MAP 1 set pfs
crypto map CRYPTO-MAP 1 set peer 123.123.123.60
crypto map CRYPTO-MAP 1 set ikev1 transform-set VPN-TRANSFORM
crypto map CRYPTO-MAP interface outside
Main-GW#2. So in this example it’s called CRYPTO-MAP 1, let’s enable reverse route injection for that crypto map.
Main-GW# configure terminal Main-GW(config)# crypto map CRYPTO-MAP 1 set reverse-route
3. Now create a ‘prefix-list‘ that contains our remote VPN subnet. (Note: if you had a lot of remote subnets you could add them separately or simply summarise them if they were contiguous networks).
Main-GW(config)# prefix-list PL-VPN-ROUTES description Route-Map For Injecting Remote VPN Routes Main-GW(config)# prefix-list PL-VPN-ROUTES seq 5 permit 172.16.0.0/16
4. Now create a ‘route-map‘ that uses our prefix-list.
Main-GW(config)# route-map RM-VPN-ROUTES permit 10 Main-GW(config-route-map)# match ip address prefix-list PL-VPN-ROUTE Main-GW(config-route-map)# set metric 12000 Main-GW(config-route-map)# set metric-type type-1 Main-GW(config-route-map)# exit Main-GW(config)# route-map RM-VPN-ROUTES deny 100
5. To be honest you would already have OSPF setup at this point but, for completeness, let’s run through the OSPF setup.
Main-GW(config)# router ospf 20 Main-GW(config-router)# router-id 192.168.1.1 Main-GW(config-router)# network 192.168.1.0 255.255.255.0 area 0 Main-GW(config-router)# log-adj-changes
6. And while still in config-router mode, set it to redistribute our VPN network(s). And finally remember the ASA wont send out any networks, without a default-information originate command.
Main-GW(config-router)# redistribute static subnets route-map RM-VPN-ROUTES Main-GW(config-router)# default-information originate
7. Save the changes.
Main-GW# write mem
Building configuration...
Cryptochecksum: 79745c0a 509726e5 b2c66028 021fdc7d
7424 bytes copied in 1.710 secs (7424 bytes/sec)
[OK]
Main-GW#8. To make sure it has worked, on the core switch CORE-SW-01, look at the routing table.
Core-SW-01#show ip route Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route Gateway of last resort is 123.123.123.123 to network 0.0.0.0 O E1 172.16.0.0/16 [110/12011] via 192.168.1.1, 00:00:04, GigabitEthernet0/0 C 192.168.10.0/24 is directly connected, GigabitEthernet0/1 C 192.168.50.0/24 is directly connected, GigabitEthernet0/2 C 192.168.100.0/24 is directly connected, GigabitEthernet0/3 O*E2 0.0.0.0/0 [110/1] via 192.168.1.1, 00:00:03, GigabitEthernet0/0
Related Articles, References, Credits, or External Links
Cisco ASA 5500 – VPN Reverse Route Injection With EIGRP
