KB ID 0000967
Problem
I’ve been doing a lot of PKI work over the last few days, testing device enrollment and NDES etc, and came across this problem being logged on my issuing/subordinate CA server;
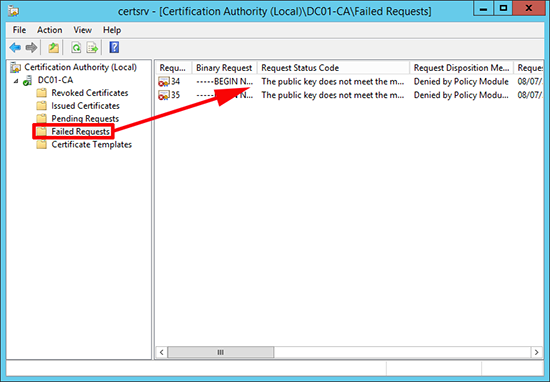
Log Name: Application Source: Microsoft-Windows-CertificationAuthority Event ID: 53 Task Category: None Level: Warning Keywords: User: SYSTEM Description: Active Directory Certificate Services denied request 35 because The public key does not meet the minimum size required by the specified certificate template. 0x80094811 (-2146875375 CERTSRV_E_KEY_LENGTH). The request was for SERIALNUMBER=4279256517 + OID.1.2.840.113549.1.9.2="sprugal.testbench.local ". Additional information: Denied by Policy Module Resubmitted by TESTBENCHAdministrator
Solution
In addition on the server itself in the Certification Authority Management console, under failed requests, it was showing the same error;
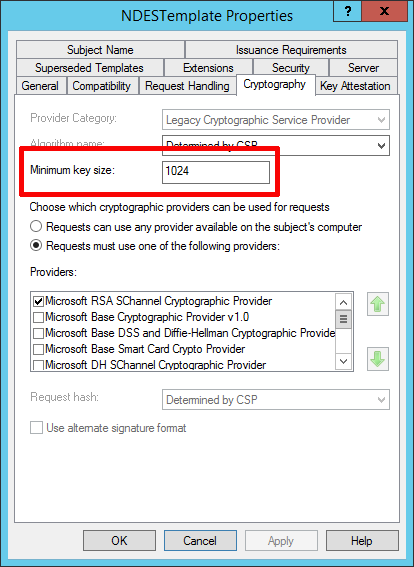
By default the certificate that NDES / MSCEP used as a template for your network devices is called ‘IPSec (Offline request)’ I’ve cloned that and made my own called NDESTemplate, but if you take a look on the Cryptography tab you can see that the minimum key size is set to 1024.
The network devices that are attempting to enroll with my server must have a key-length that is shorter, how can you tell? Well my devices are all Cisco ones (Routers and Firewalls). The Cisco ASA will tell you what key length is uses, but there is no command in router IOS to let me know. However if you use Putty and open an SSH session to the device it will tell you.
In the example below, the key length on this device is 2048 so that should be fine;
But this one is only 768 bits long! This device would generate the sort of errors I’m seeing on my Windows server.
So how do you fix the problem on the device, if you have not got your trustpoint setup then simply issue the following commands;
R1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. R1(config)#crypto key zeroize rsa % All RSA keys will be removed. % All router certs issued using these keys will also be removed. Do you really want to remove these keys? [yes/no]: yes R1(config)# *Jul 11 14:26:50.619: %SSH-5-DISABLED: SSH 1.99 has been disabled R1(config)#
If you have setup a trustpoint, simply remove the trustpoint and it removes all the keys
R1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. R1(config)#no crypto pki trustpoint PNL-TRUSTPOINT NOTE YOUR TRUSTPOINT WILL HAVE A DIFFERENT NAME!! % Removing an enrolled trustpoint will destroy all certificates received from the related Certificate Authority. Are you sure you want to do this? [yes/no]: yes % Be sure to ask the CA administrator to revoke your certificates. No enrollment sessions are currently active. R1(config)#
Related Articles, References, Credits, or External Links
NA